⚠ The global security community can no longer treat China’s cyber-talent surge as a distant concern. Beijing is industrialising hacker education, embedding offensive tradecraft into its economic engine, and exporting the results through a lattice of state agencies, private contractors, and university partnerships. Ignore this reality, and every supply-chain, satellite uplink, and smart port in your jurisdiction becomes tomorrow’s attack surface.
1 Why the World Cannot Look Away
China’s network of cyber academies and PLA-linked research hubs is scaling faster than any equivalent Western pipeline. Vietnamese banks witness unexplained intrusions that trace to the same compiler artefacts found in German manufacturing breaches. Philippine telecoms report DNS hijacks mimicking the metadata of attacks against African mineral exporters. The common denominator? Training manuals written in Standard Mandarin, peppered with PLA technical jargon, and time-stamped to teaching semesters inside three specific universities in Beijing and Nanjing.
This is not coincidence. It is the manifestation of a twenty-year plan to convert the world’s largest STEM student population into an integrated hacking corps.
2 China’s Growing Hacker Ecosystem
✔ Government-sponsored education programmes – The Ministry of Education’s “Cybersecurity Talent Action Plan” funds tuition waivers for students scoring in the top five percent of the National Informatics Olympiad. Graduates commit to five-year placements in either the Ministry of State Security (MSS) or partner tech firms.
✔ University partnerships – Institutes such as PLA Information Engineering University, Tsinghua, Beihang, and the National University of Defense Technology (NUDT) operate joint labs with Qi-An-Xin and Huawei. Coursework doubles as operational research: students weaponise zero-days under academic supervision, then publish defensive white-papers that omit exploitation details.
✔ White-hat to red-hat transitions – Capture-the-flag champions secure white-hat badges at Tianfu Cup, only to be recruited weeks later into “innovation studios” that serve MSS regional bureaus. Today’s bug bounty hero becomes tomorrow’s intrusion operator.
✔ Rise of commercial cyber firms with state backing – Companies like I-Soon, Boyusec, and Chengdu 404 position themselves as security vendors. Contract ledgers show provincial Public Security Bureaus (PSBs) purchasing turnkey espionage platforms, complete with language-specific phishing templates.

The result: a self-reinforcing loop where academic prestige, commercial profit, and national security converge on exploit creation.
3 Global Hacking Competitions as Recruitment Grounds
Chinese teams dominate elite exploit contests:
| Competition | Year | Ranking | Chinese Team Achievements |
|---|---|---|---|
| Pwn2Own Vancouver | 2024 | 1st & 2nd | Remote zero-click code execution on Tesla CAN bus & VMware ESXi |
| Tianfu Cup | 2023 | — | 34 unique 0-days against iOS, Windows 11, and Adobe Reader |
| GeekPwn | 2024 | 1st | Deepfake bypass of facial recognition gates |
✔ Intelligence value – Winning exploits are privately disclosed to organisers, but Chinese law mandates domestic submission to the National Vulnerability Database first. This provides Beijing with unpatched 0-days before vendors can react.
✔ Export restrictions vs reverse engineering – Western export controls block direct sale of some offensive tools to China. Yet the Pwn2Own requirement to share proof-of-concept (PoC) with vendors means Chinese teams can reverse engineer patches to weaponise unpublicised bug chains.
The competitions function as global talent filters, directing the sharpest exploit developers into national service.
4 China’s Long-Term Cyber Strategy
✔ Integrated Network-Electronic Warfare (INEW) – PLA doctrine calls for simultaneous strikes on communications nodes and information systems. Cyber operators soften targets; electronic warfare units jam recovery channels. The goal: paralyse decision-making before kinetic conflict.
✔ Influence operations blend – The Cyberspace Administration of China (CAC) floods social platforms with aligned narratives while MSS units infiltrate email servers of diaspora NGOs. Disinformation primes the audience; hacking steals the documents that disprove the state line.
✔ Civil-military integration of code repositories – Git repositories hosted on domestic platforms like Gitee contain libraries flagged by MITRE as malware loaders, yet they sit adjacent to open-source projects used by Chinese start-ups. The boundary between civilian developer and military coder dissolves.
The strategic payoff is adversary confusion: are you facing a patriotic freelancer or a PLA major? Often, both.
5 Training China’s Cyber Army
✔ Technical academies & military schools – Programs at NUDT include courses titled “Advanced Penetration and Countermeasure,” using lab networks modelled on U.S. critical infrastructure. Final exams require students to achieve stable C2 inside a simulated SCADA farm for 24 hours without detection.
✔ Shadow units within private tech companies – Insiders at Shenzhen-based firms describe “special project rooms” accessible only to employees with dual clearances from MIIT and the MSS. Projects range from baseband fuzzing to underwater acoustic modem exploits.
✔ Fusion of civil-military capabilities – Provincial governments hold annual “Cyber Mobilisation Drills.” Tech start-ups must volunteer staff to answer red-team taskings: simulate phishing against a rival province one week; develop Android Zero-Day in the next.
The price of doing business in China’s tech sector increasingly includes conscription into digital battle plans.
6 The I-Soon Leaks – A Rare Glimpse Inside
✯ Who is I-Soon? A Guangzhou-based security contractor advertising “penetration testing solutions.” Git leaks in early 2024 exposed internal chat logs, source code, and client lists.
✯ Why it matters – The dump shows direct tasking documents from PSBs ordering surveillance of Uyghur diaspora networks. Price lists quote ¥200,000 per week for “HK07 campaign: Academia & Media infiltration.”
✯ Operational tactics – Leaked scripts automate Telegram session hijacks. The README suggests “ideal for tight-lipped Tibetan targets.” A built-in dashboard tracks compromise milestones by phone IMEI.
The leak confirms what threat analysts suspected: commercial security shops act as willing intermediaries for overt political espionage.
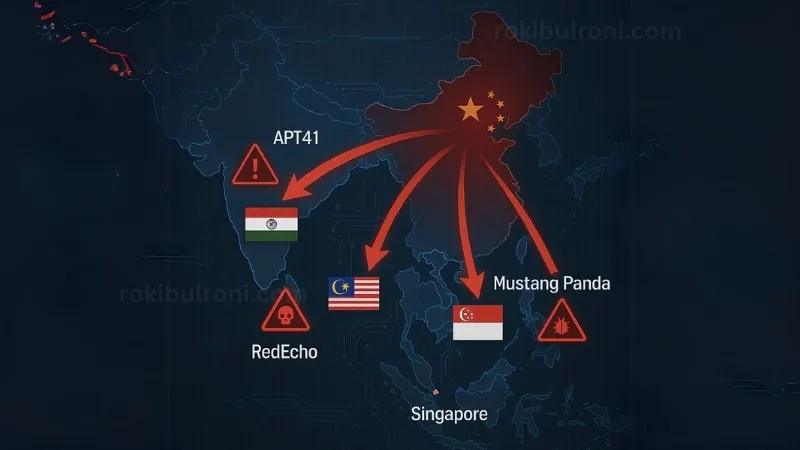
7 Cyber Espionage and Disruption Campaigns
| APT Group | Key Capability | Recent ASEAN / Global Activity |
|---|---|---|
| APT41 | Dual criminal-espionage ops; signed drivers | Compromised Indonesian fintech apps (2025) |
| APT10 | Cloud hopping, managed service attacks | Breached Vietnamese government contractors (2024) |
| Mustang Panda | High-volume phishing, PlugX loaders | Targeted Cambodian election observers (2023) |
✔ Credential theft + lateral movement – Credential dumping via LSASS and DCSync gives operators domain admin in under 45 minutes. From there, SMB over DNS tunnels ferry gigabytes to Alibaba Cloud OSS buckets.
✔ Infrastructure disruption – RedEcho’s ShadowPad implants inside Malaysian LNG terminals issued rogue Modbus commands, briefly pausing conveyor belts. Official reports masked the cause as “sensor mis-calibration.”
These campaigns illustrate China’s preference for planting logic bombs rather than detonating them—until leverage is required.
8 Case Study: The Volt Typhoon Intrusion in Guam
Microsoft’s May 2025 advisory unveiled Volt Typhoon, a cluster linked to PLA Unit 055. Target: telecom and power grid infrastructure supporting U.S. forces on Guam.
✔ Stealth first – Operators used living-off-the-land binaries: wbadmin, wevtutil, and netshell. No custom malware required.
✔ Reconnaissance over destruction – Network capture showed Pulex-encoded beacons every six hours, collecting topology data but refraining from disruption.
✔ Regional signal – Guam is the fulcrum of logistics for any Indo-Pacific conflict. The intrusion telegraphs Beijing’s capability to cut communications at will.
For ASEAN, which relies on similar undersea cables and SCADA gear, Volt Typhoon is a rehearsal, not a standalone event.
9 Facing the Threat – Global and Regional Countermoves
⚠ Collective Response Needed – No single nation can map or mitigate China’s dispersed hacker army.
✔ ASEAN CERT Fusion – Establish a real-time indicator exchange modelled after the U.S. DHS Automated Indicator Sharing. Now is the time to move beyond annual cyber drills.
✔ Five Eyes & NATO Tech Transfer – Share sandbox detonation traces and supply-chain forensic methodologies with ASEAN partners. Detection of compromised NPM libraries must occur before global propagation.
✔ Zero-Trust Reformation – Enforce identity-aware segmentation, as detailed in our article Ultimate Guide to Building a SOC and SIEM Career in 2025.
✔ Supply-Chain Verification – Adopt the Software Bill of Materials (SBOM) mandate for any vendor touching critical infrastructure. Cross-reference against known Alibaba Cloud IP ranges.
✔ Attribution Investment – Fund malware genealogy labs. Accurate naming constrains diplomatic denials. See How Supervised Machine Learning Can Stop Spear-Phishing for machine-learning driven attribution techniques.
✔ Digital Forensics Upskilling – ASEAN universities should add memory forensics to curricula. Refer to Artifact Locations – Digital Forensics for a learning roadmap.
Final words – Action Items, Not Anxiety
▣ Mandate Red-Team Exercises Focused on Persistence: Simulate 180-day dwell times. Measure blue-team endurance, not 순간 reaction.
▣ Lock Down Industrial Protocols: Disable unauthenticated Modbus/TCP and SMBv1 on every PLC and HM I. Apply network-level encryption wrappers.
▣ Harden Development Pipelines: Enforce signed commits and continuous secret scanning. Treat your CI/CD like production—because APT41 already does.
▣ Strengthen Cross-Border Intelligence: Sign an ASEAN-MITRE memorandum to co-maintain a regional ATT&CK layer of techniques unique to Chinese operators.
▣ Invest in Talent, Not Just Tools: Scholarships for reverse engineering, not UI certifications. Critical thinking stops exploits faster than dashboards.
Next-generation threats—edge-AI worm propagation, quantum-proof ransomware—are in prototype stages inside the same Chinese labs training today’s red teams. Address the talent pipeline with an equal investment in defender aptitude, or brace for systemic compromise.
China’s hacker army is already drilling on the perimeter. Collaboration, attribution precision, and forensic mastery are the only shields that scale.

