Introduction: Penetration testing (or ethical hacking) is one of the hottest cybersecurity career paths in 2025, especially in Malaysia and Singapore. As businesses and governments go digital, the demand for skilled pentesters is booming. In fact, Malaysia aims to have 25,000 cybersecurity professionals by 2025 but had only about 15,248 as of 2023, leaving a huge talent gap of nearly 12,000. Singapore’s cyber job market is similarly thriving, with over 1,600 cybersecurity job openings in May 2025. This guide will walk you through a complete roadmap – from education and certifications to skills, tools, job hunting, and beyond – to help you launch a successful penetration testing career in Malaysia or Singapore. We’ll cover local degrees and bootcamps, essential certifications like OSCP and CEH, hands-on tools (Kali Linux, Burp Suite, Metasploit), salary expectations (in MYR and SGD), and tips for building experience through CTFs, bug bounties, labs, and more. Whether you’re a fresh grad or aspiring career-changer, this 2025 guide will equip you with practical steps to kickstart your journey as an entry-level pentester in the vibrant Malaysia/Singapore cyber job market. Let’s dive in!
Why Choose a Penetration Testing Career in 2025? 🎯
High Demand in Malaysia & Singapore: Cybersecurity jobs are surging across Southeast Asia, and penetration testers are especially sought-after. With internet usage and digital services at all-time highs, companies need pentesters to probe their defenses. The Malaysian government warns of a shortage of experts – the nation needs 27,000 cybersecurity workers by end-2025 but is still far from that target. In Singapore, organizations report a severe skills gap: 92% of companies faced breaches in the past year partly due to talent shortages. Sectors like finance, healthcare, and telecom are urgently hiring security testers to protect sensitive data. Simply put, there’s never been a better time to enter the field – employers are actively looking for fresh talent, and skill shortages mean junior pentesters have abundant opportunities for growth.
Local Initiatives Boosting Cyber Careers: Both countries are investing heavily in cybersecurity talent development. Malaysia has rolled out programs like the National Cybersecurity Policy, Digital Transformation Plan, and the Cyber Security Act 2024 to spur demand for security experts. The Communications Ministry launched a Cybersecurity Centre of Excellence in 2024 with industry partners to offer hands-on training. A new Malaysia Cyber Security Academy opening in 2025 will focus on technical TVET training for cyber roles. Singapore, through its Cyber Security Agency (CSA), runs initiatives under the SG Cyber Talent framework – for example, the Youth Cyber Exploration Programme (YCEP) bootcamp gets students excited about cybersecurity careers. There are also mid-career conversion programs (like the Cyber Security Associates and Technologists scheme) to upskill professionals into cybersecurity. All these efforts indicate strong government and industry support for aspiring pentesters.
Job Market and Salary Potential: A penetration testing career offers not just purpose (helping organizations stay safe) but also attractive salaries. In Malaysia, entry-level pentesters can earn a solid income (more on exact figures in the Salary section), and experienced consultants are very well-compensated. Singapore’s mature cyber job market offers even higher pay; for example, entry-level cybersecurity roles start around SGD $70K annually (≈$5.8K/month), and seasoned experts can earn up to SGD $250–300K per year. Recruiters in Singapore report technology roles (including cybersecurity) saw ~5-15% salary growth in 2024 and 2025. In short, both countries reward skilled pentesters handsomely in 2025.
Insight: “Remote and hybrid work arrangements increase the demand for skills, as unmanaged devices can pose major security threats,” noted Fahmi Fadzil, Malaysia’s Communications and Digital Minister. Post-pandemic work trends have expanded attack surfaces, further driving up the need for penetration testers to secure organizations in the new normal.
Education Paths – Degrees, Courses, and Bootcamps 🎓
There’s no single “correct” way to become a penetration tester. Some start with formal degrees, while others are self-taught or come from related IT backgrounds. Here are the common education paths in Malaysia and Singapore:
-
University Degrees in Cybersecurity or IT: Earning a bachelor’s degree in Computer Science, Cybersecurity, or related fields provides a strong foundation. Many top universities in both countries now offer specialized programs. In Malaysia, universities such as University of Malaya (UM), Universiti Teknologi Malaysia (UTM), Universiti Sains Malaysia (USM), and private institutions like Asia Pacific University (APU) and Multimedia University (MMU) have reputable cybersecurity or information security degrees. These programs cover programming, networks, cryptography, and sometimes offer pentesting electives. In Singapore, world-class schools like National University of Singapore (NUS) and Nanyang Technological University (NTU) offer degrees in Info-Security or Computing with cybersecurity specializations. Institutes like Singapore Institute of Technology (SIT) and Singapore Management University (SMU) also have cybersecurity degree courses or partnerships (e.g. with overseas universities like University of Wollongong or James Cook University). A formal degree isn’t strictly required to be a pentester, but it can equip you with broad knowledge and make you more visible to employers (especially for fresh graduates).
-
Cybersecurity Bootcamps and Certifications Courses: If a full degree isn’t feasible or you already have a degree in another field, consider shorter intensive courses. There are bootcamps and professional training programs designed to quickly build practical cyber skills. For example, in Singapore, private academies like the Vertical Institute or ThriveDX offer bootcamps in ethical hacking, and SANS Institute runs high-end security courses (though pricey). The government-supported SG Cyber Youth initiative runs the YCEP bootcamp for students, and polytechnics offer specialist diplomas in cybersecurity. In Malaysia, you’ll find bootcamp-style courses such as Nexperts Academy’s Cyber Security Bootcamp (an intensive 160-hour program) and training by organizations like CyberSecurity Malaysia (the national agency) through its CyberGuru platform. Even global providers like Google offer the Google Cybersecurity Professional Certificate online in Malaysia, which is a beginner-friendly way to learn security fundamentals. Bootcamps can be great for hands-on learning and often include career support, but do vet their credibility and placement rates.
-
Online Courses and Self-Learning: The pentesting community thrives on self-learners. There are abundant online resources (many free or affordable) to teach yourself hacking skills. Platforms like TryHackMe, Hack The Box, and INE offer guided labs and challenges from basic to advanced levels. Websites like Coursera and edX have courses in cybersecurity (some in partnership with universities). A self-taught route demands discipline, but it’s absolutely possible to land a job this way if you build the right skills and portfolio. In fact, companies increasingly value skills over paper qualifications – many hiring managers say they focus on practical abilities and are open to self-taught candidates who can prove themselves. You can start with a Beginner’s Guide to Penetration Testing to understand the fundamentals, then dive into specific skills as you go.
Tip: Whether you choose a degree or not, never stop learning on your own. The field changes quickly, and the best pentesters are constantly updating their knowledge. Even as a student, try to complement theory with practice (set up a home lab, participate in hacking competitions, etc.). In cybersecurity, passion and curiosity go a long way. As one veteran pentester famously said, “I don’t believe you can be a good penetration tester if you’re not passionate about IT security… It’s more than a job, and constant self-learning is a must.” Enthusiasm and an autodidactic mindset will carry you further than any one qualification.
Credit: [StationX]
Certifications: Boost Your Credibility 🏅
While skills matter most, certifications can significantly enhance your job prospects – especially for entry-level roles where employers use certs as a baseline filter. In Malaysia and Singapore, many job postings list cybersecurity certs as “preferred” or even required. In fact, 94% of organizations in Singapore prefer hiring candidates with certifications, and 92% would even fund employees to get certified. The right certification proves to recruiters that you have a verified level of knowledge, and it can set you apart as a committed professional. Here are some top certs to consider on your penetration testing career path:
This roadmap organizes certifications into domains, skill levels (Expert, Intermediate, Beginner), and relevant sub-domains.
481 certifications listed | July 2024
✨ Communication and Network Security
The communication and network security domain covers the ability to secure communication channels and networks. Topics include secure and converged protocols, wireless networks, cellular networks, hardware operation (warranty and redundant power) and third-party connectivity. IP networking (IPSec, IPv4 and IPv6) are also included in this domain.
Expert
- CCIE Sec (Cisco Certified Implementation Expert - Security -
$2,050 Hands-on Lab, $12,000 est Travel cost) - CCIE Ent (Cisco Certified Internetwork Expert - Enterprise Infrastructure -
~$2,050 hands-on lab, ~$12,000 in travel costs) - JNCIE Sec (Juniper Networks Certified Internet Expert, Security -
$1,400 Hands-on Lab) - CCDE (Cisco Certified Design Expert -
~$1,600 written exam with hands-on lab) - FCX (Fortinet Certified Expert -
$400 written exam, $1600 in-person lab)
Intermediate
- CCNP Sec (Cisco Certified Network Professional - Security -
~$1,200 exam) - JNCIP Sec (Juniper Networks Certified Internet Professional, Security -
$400 exam) - PCNSE (Palo Alto Networks Certified Network Security Engineer -
$175 exam) - FCSS ZTA (Fortinet Certified Solution Specialist - Zero Trust Access -
$800 two exams) - F5 CSE Sec (F5 Big-IP Certified Solution Expert - Security -
$135 exam) - CCNP Ent (Cisco Certified Network Professional - Enterprise -
~$600 exam) - CCSM (Checkpoint Certified Security Master -
$350 exam) - PCSAE (Palo Alto Certified Cloud Security Automation Engineer -
$350 exam) - PCCSE (Prisma Certified Cloud Security Engineer -
$350 exam) - FCSS NS (Fortinet Certificed Solution Specialist - Network Security -
$800 two exams) - CCSE (Checkpoint Certified Security Expert -
$250 exam) - JNCIS Sec (Juniper Networks Certified Internet Specialist, Security -
$300 exam) - F5 CTS APM (F5 Big-IP Certified Technical Specialist - Access Policy Manager -
$135 exam) - FCP NS (Fortinet Certified Professional - Network Security -
$400 for 2 exams) - CCNA (Cisco Certified Network Associate -
~$330 exam) - F5 CTS DNS (F5 Big-IP Certified Technical Specialist - Domain Name Services -
$135 exam) - PCDRA (Palo Alto Networks Certified Detection and Remediation Analyst -
$155 exam) - CWSP (CWNP Certified Wireless Security Professional -
$325 exam) - CREST CCNIA (CREST Certified Network Intrusion Analyst -
$2,481 exam & essay, Hands on exam in UK)
Beginner
- F5 CA (F5 Big-IP Certified Administrator -
$135 exam) - eNDP (eLearnSecurity Network Defense Professional -
$400 exam) - MNSE (Mosse Institute Network Security Essentials -
$450 certification programme, 100% practical. No expiry.) - PCNSA (Palo Alto Networks Certified Network Security Administrator -
$155 exam) - OWSE (ISECOM OSSTMM Wireless Security Expert -
$100 annual sub, Unknown exam cost) - JNCIA Sec (Juniper Networks Certified Internet Associate, Security -
$200 exam) - FCA (Fortinet Certificed Associate -
Free course and exam required) - WCNA (Protocol Analysis Institute Wireshark Certified Network Analyst -
$299 exam) - CCSA (Checkpoint Certified Security Administrator -
$250 exam) - ITS-NS (Certiport IT Specialist - Network Security -
$127 exam) - CCT (Cisco Certified Technician -
$165 exam) - SOG NSP (SecOps Group Certified Network Security Practitioner -
$249 exam) - Net+ (CompTIA Network+ -
$369 exam) - FCF (Fortinet Certified Fundamentals Cybersecurity -
Free 3 courses with exams req) - PCCET (Palo Alto Networks Certified Cybersecurity Entry-level Technician -
$110 exam)
✨ IAM (Identity and Access Management)
(The identity and access management domain covers the attacks that target the human gateway to gain access to data. Other topics include ways to identify users with rights to access the information and servers. Identify and access management covers the topics of applications, Single sign-on authentication, privilege escalation, Kerberos, rule-based or risk-based access control, proofing and establishment of identity.)
Intermediate
- CIMP (Identify Management Institute Certified Identity Management Professional -
$295 + Membership) - FCSS SASE (Fortinet Certified Solution Specialist - Secure Access Service Edge -
$800 two exams) - CIAM (Identify Management Institute Certified Identify and Access Manager -
$390 Exam) - CIDPRO (IDPro Certified Identity Professional -
$700 exam) - SF CIAMD (SalesForce Certified Identity and Access Management Designer -
$400 exam) - CIGE (IMI Certified Identity Governance Expert -
$395 exam)
Beginner
- CIST (IMI Certfied Identity and Security Technologist -
$295 exam) - SC-300 (Microsoft Certfied: Identity and Access Administrator Associate -
$165 exam) - CAMS (IMI Certfied Access Management Specialist -
$195 exam) - SC-900 (Microsoft Certified: Security, Compliance, and Identity Fundamentals -
$99 exam)
✨ Security Architecture and Engineering
(The security architecture and engineering domain covers important topics concering security engineering plans, designs, and principles. Topics include assessing and mitigating information system vulnerabilities, fundamental concepts of security models and security architectures in critical areas like access control. Cloud systems, cryptography, system infiltrations (ransomware, fault-injection and more) and virtualized systems are also covered in this domain.)
Expert
Cloud/SysOps
- VCDX DCV (VMware Certified Design Expert in Datacenter Virtualization-
$3,995 exams, Application also req.) - VCIX DCV (VMware Certified Implementation Expert in DatacenterVirtualization -
$900 two exams) - AWS SAP (Amazon Web Services CertifiedSolutions Architect - Professional -
$300 exam) - AZ-305(Microsoft Azure Solutions Architect Expert -
$330 exam) - VCIX NV (VMware Certified Implementation Expert in NetworkVirtualization -
$900 two exams) - Google PCSA(Google Professional Cloud Architect -
$200 exam)
*nix
- RHCA (Red HatCertified Architect -
~$3,745 exam, plus travel) - RHCE (Red HatCertified Engineer -
$400 exam) - LPIC-3(Linux Professional Institute Certified: 303 Security -
$200 exam) - SCE (SUSE CertifiedEngineer -
$195 practical exam)
ICS/IoT
- ISA CE (ISACybersecurity Expert -
$2,700 course + exam, Course required) - CACE (Excida IEC 62443 CertifiedAutomation Cybersecurity Expert -
$700 exam)
General Engineering
- CREST CRTSA (CREST Registered TechnicalSecurity Architect -
$2,300 two exams, In person in the UK) - SABSA SCM (SABSA Chartered SecurityArchitect - Master Certificate -
$3,750 exam & thesis, Branded courserequired) - GDAT(GIAC Defending Advanced Threats -
$979 exam, SANS course recommended) - SC-100(Microsoft Cybersecurity Architect -
$165 exam) - SABSA SCP (SABSA Chartered SecurityArchitect - Practitioner Certificate -
$3,750 written exam, Branded courserequired) - GDSA (GIAC Defensible SecurityArchitecture -
$979 exam, SANS course recommended)
Intermediate
Cloud/SysOps
- FCSS PCS (Fortinet Certified Solution Specialist -Public Cloud Security -
$400 exam) - GCTD(GIAC Cloud Threat Detection -
$979 exam, SANS course recommended) - MS-100 (Microsoft 365 Certified EnterpriseAdministrator Expert -
$165 exam) - GPCS(GIAC Public Cloud Security -
$979 exam, SANS course recommended) - GCSA(GIAC Cloud Security Automation -
$979 exam, SANS course recommended) - FCSS SO (Fortinet Certified Solution Specialist -Security Operations -
$400 exam) - PDSO CDE(PDSO Certified DevSecOps Expert -
$1199, Exam and training bundled) - VCP DCV (VMware Certified Professional in Datacenter Virtualization -
$375exam, Branded course required) - CCSP ((ISC)2 Certified CloudSecurity Professional -
$599 exam) - FCP PCS (Fortinet Certified Professional - PublicCloud Security -
$400 for 2 exams) - AWS CSS(Amazon Web Services Certified Security - Specialty -
$150 exam) - SFCCCC(SalesForce Certified Community Cloud Consultant -
$200 exam, Must beSalesForce Admin Certified) - EXIN PCSA (EXIN Professional CloudSolution Architect -
$315 exam) - VCP NV (VMware Certified Professional in Network Virtualization-
$375 exam, Branded course required) - AZ-500 (MicrosoftAzure Security Engineer Associate -
$165 exam) - CSA CGC (Cloud Security Alliance CloudGovernance & Compliance -
$315 exam) - GCLD (GIAC Cloud Security Essentials -
$979exam SANS course recommended) - AWS SAA (Amazon Web Services CertifiedSolutions Architect - Associate -
$150 exam) - EXIN PCSerM (EXIN Professional CloudService Manager -
$315 exam)
*nix
- GCWN (GIAC Certified WindowsSecurity Administrator -
$979 exam, SANS course recommended) - CKS (Cloud Native ComputingFoundation Certified Kubernetes Security Specialist -
$375 lab, Brandedcourse required) - LFCS (Linux Foundation CertifiedSystem Administrator -
$300 exam) - FCP SO (Fortinet Certified Professional - SecurityOperations -
$400 for 2 exams) - RHCSA (Red HatCertified System Administrator -
$400 exam) - CKA (Cloud Native ComputingFoundation Certified Kubernetes Administrator -
$375 lab, Branded courserequired) - LPIC-2 (LinuxProfessional Institute Certified: Linux Engineer -
$400 2 exams)
ICS/IoT
- GRID (GIAC Response and Industrial Defense -
$979 exam, SANS course encouraged) - CSSA(Infosec Institute Certified SCADA Security Architect -
$4,599 exam, Courserequired) - ISA CDS (ISA Certified DesignSpecialist -
$2,700 course + exam) - TUV COTCP(TUV Rheinland Certified Operational Technology Cybersecurity Professional(GERMAN) -
$415 exam) - GCIP (GIAC Critical InfrastructureProtection -
$979 exam, SANS course encouraged) - ISA CRAS (ISA Certified RiskAssesment Specialist -
$2,700 course + exam, Course required)
General Engineering
- CIS LI (IBITGQ CertifiedISO 27001 Information Security Management Specialist Lead Implementer -
$2008 course exam, Branded course required) - SFCTA (SalesforceCertified Technical Architect -
$6000, Must be SF SA Certified) - SABSA SCF (SABSA Chartered Security Architect- Foundation Certificate -
$3,750 exam, Branded course required) - SPLK-3001 (Splunk Enterprise Security CertifiedAdministrator -
$130 exam, Branded course recommended) - SFSA (SalesForceSystem Architect -
$400 hands-on lab) - CCSE (ECCouncil Certified Cloud Security Engineer -
$100 exam, EC Council CourseRecommended) - MCSE (Mosse Institute Cloud SecurityEngineer -
$600 exam)
Beginner
Cloud/SysOps
- Google PCSE (Google Professional Cloud Security Engineer -
$200 exam) - EXIN PCSM (EXIN Professional CloudSecurity Manager -
$315 exam) - MDSO (Mosse Institute Certified DevSecOpsEngineer -
$450 exam) - CSA CCSK (Cloud SecurityAlliance Certificate of Cloud Security Knowledge -
$395 exam) - C)CSO (Mile2 Certified Cloud SecurityOfficer -
$550 exam) - Server+ (CompTIA Server+-
$319 exam) - PDSO CDP (PDSO Certified DevSecOps Professional -
$799, Exam and training bundled) - EXIN PCD (EXIN Professional Cloud Developer -
$315 exam) - Cloud+ (CompTIA Cloud+ -
$369 exam) - Google ACE(Google Associate Cloud Engineer -
$125 exam) - SOG CCSP-AWS (SecOps Group CertifiedCloud Security Practitioner - AWS -
$249 exam) - AWS CP(Amazon Web Services Certified Cloud Practitioner -
$100 exam) - EXIN PCA (EXIN Professional CloudAdministrator -
$315 exam) - Cloud Essnt(CompTIA Cloud Essentials -
$138 exam)
*nix
- SCA (SUSE CertifiedAdministrator -
$149 exam) - DCA (Docker CertifiedAssociate -
$195 exam) - LPIC-1 (LinuxProfessional Institute Certified: Linux Administrator -
$400 2 exams) - KCNA (Cloud Native ComputingFoundation Kubernetes and Cloud Native Associate -
$250 exam, Brandedcourse required) - Linux+ (CompTIA Linux+ -
$369 exam) - LFCA(Linux Foundation Certified IT Associate -
$200 exam) - Apple ACSP (Apple CertifiedSupport Professional -
$250 exam, Limited test locations) - A+ (CompTIA A+ -
$253 exam)
ICS/IoT
- ISA CAP (ISA CertifiedAutomation Specialist -
$467 exam) - TUV COSM (TUV Certified OTSecurity Manager -
$3,070 Course) - GICSP (GIAC Global IndustrialSecurity Professional -
$979 exam, SANS course encouraged) - AZ-220(Azure IoT Developer Specialty -
$165 exam) - ISA CFS (ISA CertifiedFundamentals Specialist -
$2,700 course + exam, Course required) - EITCA/IS (EITCA/ISInformation Security Certificate -
$120 exam) - CACS (Excida IEC 62443 CertifiedAutomation Cybersecurity Specialist -
$700 exam) - TUV COSP (TUV Certified OTSecurity Practitioner -
$2725 course) - CIOTSP (CertNexus CertifiedInternet of Things Security Practitioner -
$250 exam)
General Engineering
✨ Asset Security
(The Asset Security domain deals with the issues related to the collection, storage, maintenance, retention and destruction of data. It also covers knowledge of different roles regarding data handling (owner, controller and custodian) as well as data protection methods and data states. Other topics include resource provision, asset classification and data lifecycle management.)
Expert
- ASIS CPP (ASIS Certified Protection Professional -
$485 exam)
Intermediate
- CIPT (IAPP Certified Information Privacy Technologist -
$550 exam) - CDPSE (ISACA Certified Data Privacy Solutions Engineer -
$880 Application) - EPDPP (EXIN Privacy and Data Protection Practitioner -
$243 Exam, Course req'd) - CIPA (IMI Certified Identity Protection -
$295 Exam) - DCPP (DSCI Certified Privacy Professional -
$205 Exam) - CIMP (IMI Certified Identity Management Professional -
$295 Exam) - CDP (IMI Certified in Data Protection -
$395 Exam)
Beginner
- ASIS APP (ASIS Associate Protection Professional -
$350 exam) - CRFS (IMI Certified Red Flag Specialist -
$295 exam) - CIPP (IAPP Certified Information Privacy Professional -
$550 exam) - EPDPF (EXIN Privacy and Data Protection Foundation -
$207 exam) - EPDPE (EXIN Privacy and Data Protection Essentials -
$145 exam)
✨ Security and Risk Management
(The security and risk management domain covers general on skills related to the implementation of user awareness programs as well as security procedures. Emphasis is also placed on risk management concerning the acquisition of new services, hardware and software (supply chain). Other skills include social engineering defense mechanisms.)
Expert
- ITIL Master (ITIL Master -
$4,000 Interview) - GSE (GIAC Security Expert -
~$7475 for 10 exams) - PgMP (PMI Program Management Professional -
$1,000 exam) - CISSP Concentrations ((ISC)2 Certified Information Systems Security Professional Concentrations -
$599 exam) - NCSC CCPLP (NCSC Certified Cybersecurity Professional - Lead Practitioner -
$1388 interview) - Zach EAPro (Zachman Enterprise Architect Professional (Level 3) -
$2,999 exam & case study, Level 1 & 2 cert not req'd) - PMP (PMI Project Management Professional -
$555 exam) - CISM (ISACA Certified Information Security Manager -
$760 exam) - S-ISME (SECO Information Security Management Expert -
$850 exam) - NCSC CCPSP (NCSC Certified Cybersecurity Professional - Senior Practitioner -
$907 interview) - CISSP ((ISC)2 Certified Information Systems Security Professional -
$749 exam) - TOGAF (OpenGroup TOGAF Certified -
$360 exam) - CCISO (EC Council Certified Information Security Officer -
$3,150 course exam, Branded course required) - EEXIN ISM (EXIN Information Security Management Expert -
EST $799 oral exam) - GSTRT (GIAC Strategic Planning, Policy and Leadership -
$979 exam, SANS course recommended) - NCSC CCPP (NCSC Certified Cybersecurity Professional - Practitioner -
$225 interview) - PSM III (Scrum.org Professional Scrum Master III -
$500 exam, Branded course required) - GSP (GIAC Security Professional -
~$3735 for 5 exams) - GISP (GIAC Information Security Professional -
$979 exam, SANS course recommended)
Intermediate
GRC (Governance, Risk, and Compliance) & General Management
- ITIL SL (ITIL Strategic Leader -
$4,800 two courseexams, 2 branded courses required) - Zach EAP (Zachman Enterprise Architect Practitioner (Level 2) -
$2,999 exam & case study, Level 1 cert not req'd) - GSLC (GIAC Security LeadershipCertification -
$979 exam, SANS course recommended) - S-CISO (SECO Certified InformationSecurity Officer -
Resume review) - CASP+ (CompTIA Advanced SecurityPractitioner+ -
$509 exam) - ITIL MP (ITIL Managing Professional -
$9,600 4course exams, 4 branded courses requires) - Scrum SPS(Scrum Scaled Professional Scrum -
$250 exam) - GLEG (GIAC Law of Data Security &Investigations -
$979 exam, SANS course recommended) - CISSM (GAQMCertified Information Systems Security Manager -
$170 exam) - CGRC ((ISC)2 Certified inGovernance, Risk and Compliance -
$599 exam) - CRISC (ISACA Certified inRisk and Information Systems Control -
$760 exam) - CSM (GAQM Certified ScrumMaster -
$128 exam) - CASM (GAQM Certified AgileScrum Master -
$128 exam) - CM)ISSO (Mile2 Certified MasterInformation Systems Security Officer -
Complete C)SP, C)ISSO, C)ISSM andIS20 ($2200)) - S-ISP (SECO Information SecurityPractitioner -
$550) - Scrum PSD (Scrum Professional ScrumDeveloper -
$200 exam) - GCPM (GIAC Certified ProjectManager -
$979 exam, SANS course recommended) - BCS PCIRM (BCSPractitioner Certificate in Information Risk Management -
$287 exam) - PEXIN ISM (EXINInformation Security Management Professional -
$268 exam) - MGRC (Mosse Institute Certified GRC ExpertCertification -
$450 certification programme, 100% practical. No expiry.) - M_o_R P (Axelos M_o_R Practitioner Risk Management -
$560 exam) - CPD (GAQM CertifiedProject Director -
$210 exam) - PMI ACP (PMI Agile CertifiedPractitioner -
$495 exam) - EISM (EC CouncilInformation Security Manager -
$3,499, Branded course required) - CGEIT (ISACA Certified in theGovernance of Enterprise IT -
$760 exam) - EXIN 27001E (EXIN ISO/IEC 27001 Expert -
~$379 OralPresentation) - PECB 27005LM (PECB ISO/IEC 27005 Lead RiskManager -
~$1,595 exam, Course required) - DCCRP (DRI Certified Cyber ResilienceProfessional -
$400 Exam) - Scrum PAL (Scrum Professional AgileLeadership -
$200 exam) - CAPM (PMICertified Associate in Project Management -
$300 exam) - PSM II (Scrum.org Professional ScrumMaster II -
$250 exam) - APMG 20000P (APMG ISO/IEC20000 Practitioner -
$308 Exam, Foundation or ITIL req'd) - C)ISRM (Mile2Certified Information Systems Risk Manager -
$550 exam) - APMG 27001P (APMG ISO/IEC27001 Practitioner -
$400 exam, Application essay) - PECB 27001LI (PECB ISO/IEC 27001 LeadImplementer -
$930 exam, Course required) - Programming Language (Learning a programminglanguage is valuable to any IT professionals career. Recommendations:Python, Ruby, C++)
- CCP (EC First Certified CCMC Professional -
$2,995 exam, Courserequired) - C)ISSO (Mile2 Certified InformationSystems Security Officer -
$550 exam) - CIS RM (IBITGQ Certified ISO 27005Information Security Management Specialist Risk Management -
$2,783 courseexam, Branded course required) - EXIN 27001P (EXINISO/IEC 27001 Professional -
$279 exam) - PECB 27032CM (PECB ISO/IEC 27032Lead Cybersecurity Manager -
$899-$2,999 course exam, Course required) - C)HISSP (Mile2 Certified HealthcareInformation Systems Security Practitioner -
$550 exam) - BCS PCIAA (BCSPractitioner Certificate in Information Assurance Architecture -
$290 exam) - CCSA (EC First Certified Cyber Security Architect -
$695 exam) - PPM (GAQM Professionalin Project Management -
$210 exam) - C)ISSM (Mile2 Certified InformationSystems Security Manager -
$550 exam) - TUV ITSM (TUV ITSecurity Manager (GERMAN) -
$415 exam, Course required) - CCRMP (IBITGQ Certified in ManagingCyber Security Risk -
$2,629 course exam, Branded course required) - PECB 27005RM (PECB ISO/IEC 27005 Risk Manager -
~$995 exam, Course required) - CSBA (QAI CertifiedSoftware Business Analyst -
$350 exam + written essay)
Beginner
- CNDA (EC Council Certified NetworkDefense Architect -
$200 application, Requires CEH cert) - DACRP (DRI Associate Cyber ResilienceProfessional -
$200 exam, Course req) - CISRM (IBITGQ Certified ISO 27005Information Security Management Specialist Risk Management -
$2,783 courseexam, Branded course required) - DCRMP (DRI Certified Risk ManagementProfessional -
$400 exam, Application essay) - SSAP (SANS Security Awareness Professional -
$1219 Exam, SANS MGT433 courserecommended) - GRCP (OCEG Governance, Risk, and Compliance Professional -
$399 12 monthlicense) - SACP (The H Layer Security Awareness and CultureProfessional -
$369 Exam) - CISP (GAQMCertified Information Security Professional -
$170 exam) - Zach EAA (Zachman Enterprise Architect Associate (Level 1) -
$2,999 course exam, Branded course required) - CAD (GAQM Certified AgileDeveloper -
$128 exam) - CAC (GAQM Certified Agile Coach-
$170) - ISMI CSMP (ISMI CertifiedSecurity Management Professional -
$1159) - CSCS (EC First Certified Security Compliance Specialist -
$695exam) - APMG 27001F (APMG ISO/IEC27001 Foundation -
$400 exam, Application essay) - PECB 27001F (PECB ISO/IEC 27001 Foundation -
$500-749 exam, Course required) - C)SLO (Mile2 Certified Security LeadershipOfficer -
$550 exam) - GSEC(GIAC Security Essentials Certification -
$979 exam, SANS courserecommended) - SSCP ((ISC)2 SystemsSecurity Certified Practitioner -
$249 exam) - Security+ (CompTIASecurity+ -
$404 exam) - M_o_R Fdn (Axelos M_o_R Framework Foundation -
$495 exam) - Fair Fdn (Fair Institute Analysis Fundamentals-
$1499 exam, Course required) - PSM I (Scrum.org Professional ScrumMaster I -
$150 exam) - APMG 20000F (APMG ISO/IEC20000 Foundation -
$308 exam) - ISMI CSM (ISMICertified Security Manager -
$TBD) - BCS FISMP(BCS Foundation Certifiate in Information Security Management Principles -
$249 exam) - CC (ISC2 Certified inCybersecurity -
Free exam) - S-ISF (SECO Information SecurityFoundation -
$460 exam) - GISF (GIAC Information SecurityFundamentals -
$979 exam, SANS course recommended) - ITIL Fdn (ITIL Foundation -
$383 exam) - Project+ (CompTIA Projec+ -
$369 exam) - CIISec ICSF (CIISec Information andCybersecurity Fundamentals -
$450 exam) - FEXIN (EXIN Information Security Foundation -
$232exam) - EXIN 27001F (EXIN ISO/IEC27001 Foundation -
$232 exam) - PECB 27005F (PECB ISO/IEC 27005 Foundation -
$500-749 exam, Course required) - C CS F (IBITGQ Certified CyberSecurity Foundation -
$725 course exam, Branded course required) - CIS F (IBITGQ Certified ISO27001 Information Security Management Specialist Foundation -
$853 courseexam, Brandeed course required) - CSP (GAQM Certified SAFePractitioner -
$170 exam) - IIBA CCA (IIBA Certification in CybersecurityAnalysis -
$475 exam) - CITGP (IBITGQCertified in Implementing IT Governance - Foundation & Principles -
~$2,499course exam, Branded course required) - C)ISCAP (Mile2 Information SystemsCertification and Accredidation Professional -
$550 exam) - CSAP(Infosec Institute Certified Security Awareness Practitioner -
$2,599 exam,Course required) - PECB 27032F (PECB ISO/IEC 27032 Foundation -
$500-749 exam, Course required) - MCL (Mosse Institute Cybersecurity Leadership-
$450 exam) - ITS-C (Certiport ITSpecialist - Cybersecurity -
$127 exam)
✨ Security Assessment and Testing
(The security assessment and testing domain deals with all the techniques and tools used to find system vulnerabilities, weaknesses and potential areas of concern not addressed by security procedures and policies. Attack simulations, vulnerability assessment, compliance checks, and ethical disclosure also fall under this domain.)
Intermediate
- GSNA (GIAC Systems and Network Auditor -
$979 exam, SANS course recommended) - GCCC (GIAC Critical Controls Certification -
$979 exam, SANS course recommended) - PCI QSA (PCI Qualified Security Assessor -
$3000 req'd course) - CISA (ISACA Certified Information Systems Auditor -
$760 exam) - GMON (GIAC Continuous Monitoring -
$979 exam, SANS course recommended) - CIS LA (IBITGQ Certified ISO 27001 Information Security Management Specialist Lead Auditor -
$2,008 course exam, Branded course required) - GCIA (GIAC Certified Intrusion Analyst -
$979 exam, SANS course recommended) - CTPRA (Shared Assessment Certified Third-Party Risk Assessor -
$1295 course) - PECB 27001LA (PECB ISO/IEC 27001 Lead Auditor -
$930 exam, Course required) - IS20 (Mile2 IS20 Controls -
$550 exam) - C)ISSA (Mile2 Certified Information Systems Security Auditor -
$550 exam) - APMG 27001A (APMG ISO/IEC 27001 Auditor -
$400 exam, Application essay) - APMG 20000A (APMG ISO/IEC 20000 Auditor -
$308 Exam, Possible Course Req) - C)ISMS-LA (Mile2 Certified Information security Management Systems Lead Auditor -
$550 exam) - CIS IA (IBITGQ Certified ISO 27001 Information Security Management Specialist Internal Auditor -
$1543 course exam, Branded course required) - TUV MSA (TUV Rheinland Mobile Security Analyst (GERMAN) -
$415 exam, Course required) - CTPRP (Shared Assessment Certified Third-Party Risk Professional -
$1295 course) - IIA CIA (The Institute of Internal Auditors Certified Internal Auditor -
$1315 3 exams)
Beginner
- DCBCLA (DRI Certified Business Continuity Lead Auditor -
$400 exam, Application req) - TUV Auditor (TUV Rheinland IT Security Auditor (GERMAN) -
$415 exam, Course required) - DCBCA (DRI Certified Business Continuity Auditor -
$400 exam, Application req) - GRCA (OCEG Governance, Risk, and Compliance Auditor -
$399 12 month license) - CISST (GAQM Certified Information systems Security Tester -
$170 exam) - EXIN CIT (EXIN Cyber & IT Security -
$225 exam) - TUV CySec (TUV Rheinland Cybersecurity Specialist (GERMAN) -
$415 exam, Course required) - TUV CyAware (TUV Rheinland Cybersecurity Awareness (GERMAN) -
$415 exam, Course required)
✨ Software Security
(The software development security domain deals with implementing software-based security protocols within environments for which the IT professional is responsible. Risk analysis, vulnerability identification and auditing of source codes are all covered in this subset. Additional topics include software-designed security, maturity models, development methodologies, open-source and third-party development security.)
Intermediate
- GWEB (GIAC Certified Web Application Defender -
$979 exam, SANS course recommended) - S-CSPL (SECO Secure Programming Certified Leader -
$460 exam) - CSSLP ((ISC)2 Certified Secure Software Lifecycle Professional -
$599 exam) - CASE (EC Council Certified Application Security Engineer (.NET or Java) -
$550 exam) - DevNet Pro (Cisco DevNet Professional -
$1200 two exams, DevNet Associate req'd) - GMLE (GIAC Machine Learning Engineer -
$979 exam)
Beginner
- CASST (GAQM Certified Advanced Software Security Tester -
$210 exam) - CCSC (CertNexus Cyber Secure Coder -
$300 exam) - DevNet A (Cisco DevNet Associate -
$300 Exam) - SOG CAP (SecOps Group Certified AppSec Practitioner -
$249 exam) - CSST (GAQM Certified Software Security Tester -
$170 exam) - C)SWAE (Mile2 Secure Web Application Engineer -
$550 exam) - MASE (Mosse Institute Certified Application Security Engineer -
$450 exam) - S-SPF (SECO Secure Programming Foundation -
$460 exam)
✨ Security Operations
(The security operations domain covers topics ranging from investigations and digital forensic to detection and intrusion prevention tools, sandboxing and firewalls. Topics include user and entity behavior analytics, threat intelligence (threat hunting and threat feeds) log management, artifacts (mobile, computer and network), machine learning and AI-based tools, penetration testing, and exploitation development.)
Expert
Forensics
- GREM (GIAC Reverse Engineering Malware -
$979exam, SANS course recommended) - CFCE (IACIS Certified Forensic ComputerExaminer -
$750 4 peer reviewed exams) - CSFA (CSIAC CyberSecurityForensic Analyst -
$750 exam & lab) - GIME (GIACiOS and MacOS Examiner -
$979 exam, SANS course recommended)
Incident Handling & Threat Intelligence
- CCD (Certified CyberDefender -
$800course, 2 exam attempt included) - CAWFE (IACIS Certified AdvancedWindows Forensic Examiner -
$750 written exam & lab) - GCFA (GIAC Certified ForensicAnalyst -
$979 exam, SANS course recommended) - GCTI (GIAC Cyber ThreatIntelligence -
$979 exam, SANS course recommended) - CFSR (OpenText Certified ForensicSecurity Responder -
$250 written exam & lab) - GNFA(GIAC Network Forensic Analyst -
$979 exam, SANS course recommended) - MTIA (Mosse Institute CertifiedThreat Intelligence Analyst Certification -
$450 certification programme,100% practical. No expiry.) - GCFR (GIAC Cloud Forensics Responder -
$979exam, SANS course recommended) - BTL2 (Security Blue Team Level 2 -
$2,190course, 1 exam attempt included)
Penetration Testing
- CREST CSAM (CRESTCertified Simulated Attack Manager -
$2,499 2 exams) - MRT (Mosse Institute Certified Red TeamerCertification -
$450 certification programme, 100% practical. No expiry.) - CREST CCTINF (CREST CertifiedInfrastructure Tester -
$2,520 exam & lab) - HTB CWEE (Hack the Box Certified WebExploitation Expert -
$1260 Subscription available)
Exploitation
- OSEE (Offensive SecurityExploitation Expert -
$5,000 lab, Plus travel) - OSCE3 (Offensive Security Certified Expert 3 -
$4649 3 labs) - OSWE (Offensive SecurityWeb Expert -
~$1649 lab) - OSEP (OffensiveSecurity Experienced Penetration Tester -
$1,499 lab) - OSED (OffensiveSecurity Exploit Developer -
$1,499 lab) - GXPN (GIAC Exploit Researcherand Advanced Penetration Tester -
$979 exam, SANS course recommended) - GAWN (GIAC Assessing WirelessNetworks -
$979 exam, SANS course recommended)
Intermediate
Forensics
- GCFE (GIAC Cerified ForensicsExaminer -
$979 exam, SANS course recommended) - GASF (GIAC Advanced Smartphone Forensics -
$979 exam, SANS course recommended) - Cisco COP (Cisco CertifiedCyberOps Professional -
$700 two exams) - CCFE(Infosec Institute Certified Computer Forensics Examiner -
$4,599 exam,Course required) - MCPE (Mosse Institute CertifiedCyber Protection Expert -
$800 exam) - CMFE(Infosec Institute Certified Mobile Forensics Examiner -
$1,699 exam,Course required) - GX-FA (GIAC Experienced Forensics Analyst -
$1299 exam, SANS course recommended) - CDRP(Infosec Institute Certified Data Recovery Professional -
$4,599 exam,Course required) - eCDFP(eLearnSecurity Certified Digital Forensics Professional -
$400 exam) - GPYC (GIAC PythonCoder -
$979 exam, SANS course recommended) - MDFIR (Mosse Institute Certified DFIRSpecialist -
$450 certification programme, 100% practical. No expiry.) - SC-400 (Microsoft Certified InformationProtection Administrator Associate -
$165 exam) - CCE (ISFCE Certified Computer Examiner-
$485 written exam) - CM)DFI (Mile2 Certified MasterDigital Forensic Investigator -
Complete C)SP, C)DFE, C)NFE and C)CSA($2200)) - EnCE(OpenText EnCase Certified Examiner -
$200 two exams) - ACE(AccessData Certified Examiner -
$100 + software)
Incident Handling & Threat Intelligence
- GEIR (GIAC Enterprise Incident Response -
$979 exam, SANS course recommended) - eCTHP(eLearnSecurity Certified Threat Hunting Professional -
$400 lab) - GCED (GIAC Certified Enterprise Defender -
$979 exam, SANS course recommended) - GCDA (GIAC Certified Detection Analyst -
$979exam, SANS course recommended) - GCIH (GIAC Certified ForensicsAnalystr -
$979 exam, SANS course recommended) - MTH (Mosse Institute Certified Threat HunterCertification -
$450 certification programme, 100% practical. No expiry.) - CREST CRIA (CREST RegisteredIntrusion Analyst -
$612 exam & lab) - CREST CRTIA (CRESTRegistered Threat Intelligence Analyst -
$615 2 exams) - CREST CCHIA (CRESTCertified Host intrustion Analyst -
$2,481 exam & essay, Hands on exam inUK) - eCIR(eLearnSecurity Certified Incident Responder -
$400 lab) - C)IHE (Mile2 Certified Incident HandlingEngineer -
$550 exam)
Penetration Testing
- PACES (Pentester Academy CertifiedEnterprise Security Specialist -
$339-749 Lab access, Exam included) - S-CEHL (SECO Certified Ethical Hacker Leader -
Application) - CREST CRT (CREST RegisteredPenetration Tester -
$612 exam) - CRTO II (ZeroPoint Security Red Team Operator II -
$121 lab) - S-EHE (SECO Ethical Hacker Expert -
TBD(still), Being redesigned) - CREST CCTIM (CRESTCertified Threat Intelligence Manager -
$2,480 3 exams) - OSCP (Offensive SecurityCertified Professional -
$1,499 labs) - GX-PT(GIAC Experienced Penetration Tester -
$1299 exam, SANS course recommended) - GPEN (GIAC CertifiedPenetration Tester -
$979 exam, SANS course recommended) - OSWP (Offensive SecurityWireless Professional -
$450 labs) - CRTO (Zero PointSecurity Certified Red Team Operator -
$121 lab) - LPT(EC Council Licensed Penetration Tester -
$899 exam) - PNPT (TCM Security Practical NetworkPenetration Tester -
$299 exam) - GCPN (GIAC Cloud PenetrationTester -
$2,499 exam, SANS course recommended) - GRTP(GIAC Red Team Professional -
$979 exam, SANS course recommended) - SOG CAPenX (The SecurityOps Group CertifiedAppSec Pentesting eXpert -
$800 exam) - CSTL (CyberScheme Team Leader -
$1945 exam) - eCPPT(eLearnSecurity Certified Professional Penetration Tester -
$400 lab) - eWPT(eLearnSecurity Web Application Penetration Tester -
$400 lab) - CM)IPS (Mile2 Certified MasterIntrusion Prevention Specialist -
Complete C)VA, C)PEH, C)PTE and C)PTC($2200)) - HTB CBBH (Hack the Box Certified Bug Bounty Hunter-
$145 modules + $210 exam, $490 Subscription available)
Exploitation
- eWPTX (eLearnSecurityWeb Application Penetration Tester eXtreme -
$400 exam, $2000 training) - CREST CCSAS (CRESTCertified Simulated Attack Specialist -
$2,520 2 exams & lab) - MCD (Mosse Institute CertifiedCode Deobfuscation Specialist Certification -
$450 certification programme,100% practical. No expiry.) - GMOB (GIAC Mobile Device Security Analyst -
$399 exam, SANS course recommended) - PJMR (Practical Junior MalwareResearcher -
$399 lab) - CREA(Infosec Institute Certified Reverse Engineering Analyst -
$4,599 exam,Course required)
Beginner
Forensics
- OSIP (IntelTechniques OpenSource Intelligence Professional -
$300 practical exam) - Cisco COA (Cisco Certified CyberOpsAssociate Cyber Operations -
~$325 exam) - C)CSA (Mile2 Certified CybersecurityAnalyst -
$550 exam) - CHFI (EC Council Computer HackingForensics Investigator -
$650 exam) - SC-200 (Microsoft Certified: Security OperationsAnalyst Associate -
~$165 exam) - MRCI (Mosse Institute RemoteCybersecurity Internship Programme -
$49 certification programme, 100%practical. No expiry.) - EDRP(EC Council Disaster Recovery Professional -
$450 exam) - HTB CDSA (Hack the Box Certified DefensiveSecurity Analyst -
$145 modules + $210 exam, $490 Subscription available) - CySA+ (CompTIACybersecurity Analyst+ -
$404 exam) - CSX-P (ISACA Cybersecurity Practitioner -
$549lab) - C)NFE (Mile2Certified Network Forensics Examiner -
$550 exam, Groups only) - GOSI(GIAC Open Source Intelligence -
$979 exam, SANS course recommended) - OPSA (ISECOM OSSTMM ProfessionalSecurity Analyst -
$100 annual sub, Unknown exam fee) - CSAE (Cyber Struggle AEGIS -
$1700 course exam, Branded course required) - ASIS PCI (ASIS Professional CertifiedInvestigator -
$485 exam) - MOIS (MOIS Certified OSINT Expert Certification-
$450 certification programme, 100% practical. No expiry.) - CFA (GAQMCertified Forensic Analyst -
$128 exam) - CSA (EC CouncilCertified SOC Analyst -
$550 exam) - GFACT (GIAC FoundationalCybersecurity Technologies -
$979 exam, SANS course recommended) - ECSS (ECCouncil Certified Security Specialist -
$249 exam) - C)DFE (Mile2 Certified Digital ForensicsExaminer -
$550 exam) - C)SP (Mile2 Certified Security Principles -
$550 exam) - CSCU (ECCouncil Certified Secure Computer User -
$125 exam) - MICS (Mosse Institute Introductions toCyber Security -
Free exam)
Incident Handling & Threat Intelligence
- S-TA (SECO Certified Threat Analyst -
$550 exam) - ECIH (EC Council Certified IncidentHandler -
$300 exam) - OSDA (OffensiveSecurity Defense Analyst -
$2,499 exam, Learning subscription required) - CFR (CertNexusCyberSec First Responder -
$250 exam) - CTIA (EC Council Certified Threatintelligence Analyst -
$450 exam) - MAD SOCA (Mitre Att&ck Defender SecurityOperations Center Assessment -
$299 annual subscription) - MAD CTI (Mitre Att&ck Defender Cyber Threatintelligence -
$299 annual subscription) - CCOA (ISACA Certified CybersecurityOperations Analyst -
$760 exam) - CREST CPIA (CRESTPractitioner Intrusion Analyst -
$425 exam) - MESE (Mosse InstituteEnterprise Security Engineer -
$450 exam) - CREST CPTIA (CRESTPractitioner Threat Intelligence Analyst -
$425 exam) - S-SA (SECO Associate SOC Analyst -
$480exam) - DV AOPH (Dark Vortex AdversaryOperations and Proactive Hunting -
$2500 exam, Course required) - CND (ECCouncil Certified Network Defender -
$550 exam) - CSX-F (IBITGQ CyberIncident Response Management Foundation -
$768 course exam, Branded courserequired) - DV MILF (Dark Vortex Malware Incident and LogFoensics -
$2000 exam) - CIRM Fdn (IBITGQ CyberIncident Response Management Foundation -
$768 course exam, Branded courserequired)
Penetration Testing
- C)PSH (Mile2 Certified Powershell Hacker -
$550 exam) - CMWAPT(Infosec Institute Certified Mobile and Web App Penetration Tester -
$4,599exam, Course required) - C)PTC (Mile2 Certified Penetration TestingConsultant -
$550 exam) - CRTOP(Infosec Institute Certified Red Team Operations Professional -
$4,599exam, Course required) - CSR (Cyber Struggle Ranger -
Location Based Cost, Course Req) - CEH (ECCouncil Certified Ethical Hacker -
$1,199 exam) - SOG CAPen (The SecOpsGroup Certified AppSec Pentester -
$500 exam) - C)PTE (Mile2Certified Penetration Testing Engineer -
$550 exam) - SOG CNPen (The SecOpsGroup Certified Network Pentester -
$500 exam) - DV RTOS (Dark Vortex Red Team & OperationalSecurity -
$2500 exam, Course required) - SOG CMPen And (The SecOps Group CertifiedMobile Pentester - Android -
$400 exam) - SOG CMPen iOS (The SecOps Group Certified MobilePentester - iOS -
$400 exam) - DV MoS (Dark Vortex Malware on Steroids -
$2000 exam, Courserequired) - Pentest+ (CompTIA Pentes+ -
$404 exam) - C)VA (Mile2 CertifiedVulnerability Assessor -
$550 exam) - KLCP (Kali Linux Certified Professional -
$299exam)
Exploitation
- eMAPT(eLearnSecurity Mobile Application Penetration Tester -
$400) - BSCP (Portswigger Burp SuiteCertified Practioner -
$99 exam) - OPST (ISECOM OSSTMM ProfessionalSecurity Tester -
Unknown) - OSWA (OffensiveSecurity Web Assessor -
$2,499 Exam, Learning subscription required) - CSTM (CyberScheme Team Member -
$610 exam) - eJPT (eLearnSecurity JuniorPenetration Tester -
$249 lab) - S-EHP (SECO Ethical Hacking Practitioner -
$550 exam) - CHAT (ISECOM Certified Hacker AnalystTrainer -
$100 annual sub, Unknown exam price) - CREST CPSA (CRESTPractitioner Security Analyst -
$425 exam) - OPSE (ISECOM OSSTMM ProfessionalSecurity Expert -
$100 annual sub, Unknown exam cost) - MPT (Mosse Institute CertifiedPenetration Tester Certification -
$450 certification programme, 100%practical. No expiry.) - CPENT (EC Council CertifiedPenetration Testing Professional -
$999 exam) - CREST CCTAPP (CRESTCertified Web Application Tester -
$2,520 exam & lab) - HTB CPTS (Hack the Box CertifiedPenetration Testing Specialist -
$200 modules + $210 exam, $490Subscription available) - MRE (Mosse Institute Certified ReverseEngineer Certification -
$450 certification programme, 100% practical. Noexpiry.) - ECES (EC Council CertifiedEncryption Specialist -
$249 exam) - MCPT (Mosse Institute Cloud PenetrationTester -
$450 exam) - C)PEH (Mile2 CertifiedProfessional Ethical Hacker -
$550 exam) - GCPEH (GAQMCertified Professional Ethical Hacker -
$170 exam) - EEHF (EXIN Ethical Hacking Foundation -
$232 exam) - S-EHF (SECOEthical Hacking Foundation -
$460 exam) - CHA (ISECOM Certified Hacker Analyst-
$100 annual sub, Unknown exam cost) - DV OTD(Dark Vortex Offensive Tool Development -
$2000 exam, Course required) - MVRE (Mosse Institute Vulnerability Researcher and Exploitation Specialist -
$450 Exam)
-
OSCP (Offensive Security Certified Professional): The OSCP is often regarded as the certification for aspiring penetration testers. It’s a hands-on exam from Offensive Security where you must actually hack into lab machines within 24 hours and document the attacks. OSCP demonstrates practical pentesting skills (using Kali Linux, exploit development, etc.) and is highly respected worldwide by technical hiring managers. If you want to be taken seriously as a pentester, OSCP is a gold standard to aim for after you’ve built some core skills. (Note: Offensive Security has updated their program in 2024/2025 – passing PEN-200 now earns OSCP and a new OSCP+ designation for extra challenges.)
-
CEH (Certified Ethical Hacker): CEH by EC-Council is a popular entry-level hacking cert. It covers a broad range of topics (scanning, enumeration, viruses, cryptography, etc.) through a multiple-choice exam. CEH is sometimes critiqued for being more theoretical, but it remains widely recognized (HR departments and recruiters in Asia are very familiar with “Certified Ethical Hacker”). In Malaysia, many government-linked companies value CEH for baseline roles. It’s a good cert to show fundamental knowledge, though on its own it may not prove hands-on ability. Consider pairing CEH with practical experience or another cert.
-
CompTIA Security+ / Pentest+: CompTIA’s Security+ is a well-known certification covering general security concepts (network security, access control, threats, etc.). It’s vendor-neutral and good for establishing fundamental cybersecurity knowledge – useful if you’re completely new to the field. CompTIA Pentest+ is a newer cert specifically focused on penetration testing processes and tools. It sits between Security+ and OSCP in difficulty – more practical than CEH, but not as hands-on as OSCP. Both are globally recognized and can bolster a junior pentester’s resume.
-
CREST Certifications: CREST is an industry body that certifies pentesters, widely recognized in the UK and Asia. In Singapore and Malaysia, many cybersecurity consulting firms are CREST-certified and look for individuals with CREST qualifications. The CREST Registered Penetration Tester (CRT) exam, for example, is a practical test of web app and network hacking skills. Achieving CREST CRT (or the higher CPSA/CCT) can open doors to consultancies and projects (it’s even a requirement for some government/financial sector pentest contracts in the region). CREST exams are challenging but respected in the industry. If you plan to work for a pen-testing service provider, this is worth looking into down the line.
-
CISSP (Certified Information Systems Security Professional): CISSP is a senior-level certification covering a broad range of security management and design topics (governance, risk, crypto, etc.). It’s not pentesting-specific and requires 5 years experience (or fewer with waivers), so it’s not something for your initial step. However, many security leaders in Malaysia and Singapore hold CISSP, and larger companies often want their security employees to eventually get it. As you progress to higher roles (or if you lean towards management or defensive security later), CISSP or similar (CISM, CRISC) could be in your plan. For now, know that it exists but focus on the technical certs first.
There are many other certifications (OSCE3, GIAC GPEN/GWAPT from SANS, eLearnSecurity’s eJPT/eCPPT, etc.). Which to pursue will depend on your budget, your specialization interests, and job requirements. A sensible approach for 2025 is: start with one foundational cert (Security+ or CEH or the new ISC2 Certified in Cybersecurity (CC) for absolute beginners), then tackle a practical pentest cert like OSCP or Pentest+ to prove your hands-on skills. The combination of a fundamental cert + OSCP is extremely powerful for landing junior pentest jobs.
Certification Comparison: To help you decide, here’s a quick comparison of some key certifications relevant to penetration testing:
| Certification | Provider | Focus Area | Suitable For |
|---|---|---|---|
| OSCP (OffSec) | Offensive Security | Hands-on penetration testing on networks and apps. 24-hour hack exam. | Aspiring pentesters ready for a technical challenge; highly respected in pentest roles. |
| CEH (v12) | EC-Council | Broad “ethical hacking” topics (tools, phases, etc.), theory-based exam. | Beginners to show baseline knowledge; widely recognized by HR (especially in Asia). |
| CompTIA Pentest+ | CompTIA | Penetration testing process, tools, and reporting. Mix of multiple-choice and performance questions. | Those with 1-2 years experience or Security+ who want a practical cert before OSCP. |
| CREST CRT | CREST (UK) | Web app and infrastructure pentesting, hands-on exam. | Penetration testers aiming to work in security consultancies or regional firms requiring CREST. |
| CISSP | (ISC)² | Comprehensive cybersecurity management and design (8 domains). | Mid-career professionals; not specific to pentesting, but valuable for long-term career growth in security. |
Note: Certification costs vary. Some, like OSCP, cost a few thousand ringgit/dollars (including training labs), while others like Security+ or CEH also have substantial exam fees. Plan your budget and see if your employer (or future employer) offers any funding support. In Singapore, SkillsFuture credits or employer training budgets might offset costs; in Malaysia, look out for scholarships or initiatives (e.g., EC-Council offered RM5 million in scholarships in 2024 to train Malaysians in cyber courses). Also, remember that certs are a means to an end – they complement skills, not replace them. Make sure you actually learn the material (set up a lab, practice exploits, etc.) rather than just memorizing answers.
Essential Tools and Technologies to Master 🛠️
Pentesters are like digital locksmiths – we rely on a toolkit of specialized tools and technologies to probe systems. As you start out, familiarize yourself with the key tools of the trade. Many of these come bundled in Kali Linux, the go-to operating system for penetration testing. Don’t worry, you can install Kali in a virtual machine on your PC (or use alternatives like Parrot OS) – see our guide on Debian Lab Setup for Cyber-Security Enthusiast for how to set up a safe home lab environment. Here are the must-know tools and tech for an entry-level pentester:
-
Kali Linux: A Linux distribution loaded with hundreds of security tools. Kali is basically a one-stop platform for pentesting – you’ll use it for network scanning, web application attacks, password cracking, reverse engineering, and more. Get comfortable with the Linux command line and basic scripting; this will allow you to automate tasks and use tools effectively. Learning tip: Start by installing Kali in VirtualBox/VMware and explore. Try basic commands and run simple tools like
nmapornikto. Offensive Security (the makers of Kali) provide free documentation, and many online tutorials (YouTube, etc.) walk through using Kali for various hacks. -
Networking & OS Fundamentals: Not a “tool” per se, but knowledge of computer networks (TCP/IP, ports, protocols) and operating systems (Windows and Linux internals) is critical. You need to understand how data flows and how systems authenticate in order to find weaknesses. For example, knowing how Active Directory domain authentication works or how Linux file permissions work can reveal attack paths. If you’re not from an IT background, spend time learning networking (perhaps get CCNA basics or do an online course) and play with both Windows and Linux servers in your lab. These fundamentals underpin everything a pentester does.
-
Nmap: The classic network scanner. Nmap (Network Mapper) is used to discover hosts and open ports/services in a network, and to fingerprint software versions. It’s usually one of the first tools you’ll run in a pentest to map out the target environment. Mastering Nmap means learning various scan types (
-sS,-sV, etc.), using scripts (nmap -sCruns default NSE scripts for common vulnerabilities), and understanding the output. Learning tip: Practice scanning your own machines or try VulnHub VMs with known open ports. Read the free book “Nmap Network Scanning” or online cheat sheets. -
Burp Suite: The Burp Suite proxy by PortSwigger is an indispensable tool for web application penetration testing. It sits as a proxy between your browser and web servers, allowing you to intercept and modify HTTP requests/responses. With Burp, you can test for SQL injection, XSS, authentication issues, etc., and use its scanner (Burp Professional) to automate some findings. Burp Suite has an extender and collaborator for advanced tricks too. Learning tip: Use the free Burp Suite Community Edition along with test sites like DVWA (Damn Vulnerable Web App) or the labs on PortSwigger’s Web Security Academy (which is an excellent free resource). This will teach you how to manipulate parameters, replay requests, and exploit web vulns. We also have a detailed Social Engineering roadmap that complements technical web hacking by covering human-hacking tactics often used alongside tools like Burp.
-
Metasploit Framework: Metasploit is a powerful exploitation framework that every pentester should know. It contains a vast database of exploits for known vulnerabilities and provides a convenient way to exploit targets and establish sessions (it’s like a Swiss-army knife for post-exploitation). With Metasploit, you can, for example, use a Windows SMB exploit to pop a shell on an unpatched server, then use Metasploit’s payloads (like Meterpreter) for further control. Learning tip: Start Metasploit (
msfconsole) in Kali and explore basic commands. Try using it on an intentionally vulnerable VM (like Metasploitable2) – exploit a vulnerability and get a shell. Rapid7’s Metasploit Unleashed and other free tutorials walk through common scenarios. -
Wireshark: A network protocol analyzer that lets you capture and inspect traffic. While Wireshark is more often used in network troubleshooting or digital forensics, a pentester benefits from understanding packet captures too. For example, you might use Wireshark to analyze unencrypted credentials passing over the network, or to better understand an unfamiliar protocol you’re trying to exploit. It’s also useful when performing man-in-the-middle attacks or analyzing malware traffic. Learning tip: Open Wireshark on your own network, capture some packets, and learn to filter (e.g.,
http.requestortcp.port==80). Identify protocols and follow TCP streams. This builds your intuition of network communications – critical for advanced testing.
Of course, the list of tools goes on: SQLmap for automating SQL injection attacks, John the Ripper/Hashcat for password cracking, OWASP ZAP as an open-source alternative to Burp, Nessus/OpenVAS for vulnerability scanning, and many more. Don’t get overwhelmed – you don’t need to master every tool at once. Focus on one category at a time (say, network scanning with Nmap, then web with Burp/ZAP, then exploitation with Metasploit). Over time, as you participate in more CTF challenges or lab exercises, you’ll naturally pick up new tools.
To summarize, here’s a table of core pentesting tools and how you can start learning each:
| Tool/Technology | Purpose | How to Learn & Practice |
|---|---|---|
| Kali Linux | Linux OS pre-loaded with security tools; the main pentesting platform. | Practice: Install Kali in a VM; use it as your hacking workspace. Learn basic Linux commands and explore the included tools (Nmap, Burp, etc.). Kali’s official docs and community forums are helpful. |
| Nmap | Network scanning and enumeration (find open ports, services, OS). | Practice: Scan your local network or lab VMs with various flags (-sS, -A, etc.). Use Nmap’s output to sketch network diagrams. The Nmap Book (free online) is a great resource. |
| Burp Suite | Intercepting proxy for web application testing (modify traffic, scan for vulns). | Practice: Use Burp Community Edition on test sites (e.g. DVWA or PortSwigger’s Web Security Academy challenges). Learn to intercept login requests, fuzz parameters, and exploit basic web bugs (SQLi, XSS). |
| Metasploit Framework | Exploit development and launch platform; contains hundreds of exploits and payloads. | Practice: Set up a vulnerable target (e.g. Metasploitable VM) and use Metasploit modules to exploit it. Try exploit/windows/smb/ms17_010_eternalblue on an unpatched Win7 VM for example. Metasploit’s wiki and TryHackMe rooms can guide you. |
| Wireshark | Packet capture and analysis; useful for understanding network traffic or finding credentials. | Practice: Capture traffic on your own network (with permission!). Filter for interesting data (HTTP, FTP, ARP poisoning if you test it). Lots of free pcap files are available online to learn analysis techniques. |
Remember, tools are just aids – the real skill is in knowing how and when to use them. A good pentester approaches a target methodically: reconnaissance, scanning, enumeration, exploitation, and post-exploitation, choosing the right tool at each phase. You’ll get a feel for this workflow as you train. Our Beginner’s Guide to Penetration Testing covers common tools and techniques in each phase, which is a great starting point if you need a refresher on methodology.
Technical and Soft Skills You Need 🧠💬
Being a great penetration tester is not only about hacking tools or coding exploits. Companies seek well-rounded professionals with a mix of technical expertise and soft skills. Let’s break down the essential skills:
Technical Skills:
- Strong Fundamentals in IT: As mentioned, knowledge of operating systems (Windows/Linux), networking, databases, and web technologies is crucial. If you know how systems are supposed to work, you can better figure out how to break them. Make sure you understand concepts like IP addressing, DNS, VPNs, firewalls, etc. Practice setting up a small network or domain controller in your lab to see how things connect.
- Vulnerability Knowledge: Familiarize yourself with common vulnerability classes and attack techniques. For web apps, study the OWASP Top 10 (e.g., injection flaws, XSS, CSRF). For networks, learn about SMB relay attacks, man-in-the-middle, buffer overflows, and so on. As a pentester, you’ll often explain these issues to clients, so know both how to exploit them and how to recommend fixes.
- Scripting & Programming: You don’t need to be a software engineer, but basic coding skills give you a huge advantage. Scripting (Python, Bash, or PowerShell) helps automate tasks and write small hacking scripts. For instance, you might write a Python script to scrape a website for certain info or automate password guessing. Understanding code also means you can read exploit scripts or tweak open-source tools. Many pentesters also eventually learn some C/C++ or Assembly for exploit development, but that’s not mandatory at entry level. Start with Python – it’s widely used in security.
- Active Directory and Cloud: In corporate environments, Active Directory (AD) is a big part of internal pentests. Learn how AD authentication works, what Kerberos is, and attacks like Pass-the-Ticket or Golden Ticket. Similarly, basics of cloud (AWS/Azure) security are increasingly valuable – e.g., knowing how to test misconfigured S3 buckets or Azure AD. You might not deal with cloud in every junior role, but cloud skills are a bonus as companies migrate to cloud services.
- Security Tools Proficiency: We’ve covered tools – ensure you can confidently operate the major ones (at least the ones in the table above). Employers might not expect you to be a master of all, but they will expect familiarity. For example, you might be asked in an interview: “How do you enumerate open ports and services on a target network?” – They expect you to mention using Nmap or similar. Or “What tool would you use to intercept web traffic?” – Answer: Burp Suite. Show that you’ve actually used these tools, not just read about them.
Soft Skills:
- Analytical Thinking and Problem-Solving: Penetration testing is like puzzle-solving. You need a mindset that enjoys digging into problems and thinking creatively. Sometimes an attack vector isn’t obvious – maybe a low-severity bug can be chained with another to escalate privileges. A great pentester is persistent and inventive in finding ways in. This analytical trait is something you build by practice: doing CTF challenges, solving Hack The Box machines, etc., all train you to think outside the box.
- Communication (Written & Verbal): Arguably as important as your hacking prowess is your ability to communicate findings. As a pentester, you’ll write reports explaining vulnerabilities and recommendations. Those reports must be clear, structured, and accessible to non-experts. Work on your writing skills – can you describe a technical issue in plain English? Likewise, you may present results to IT teams or managers. Practice speaking confidently about your work. One tip: write blog posts or LinkedIn articles about your security learnings (even just summaries of a lab you did). This not only improves communication but also builds your personal brand.
- Teamwork and Collaboration: Pentesters often work in teams, especially on larger engagements. You might be coordinating with another tester on different scopes, or working with a developer team when doing a DevSecOps review. Being able to collaborate, share information, and even mentor or be mentored is key. Show that you can work well with others – mention class projects, hackathon teams, or community contributions on your CV.
- Ethics and Professionalism: You are being hired to break into systems – ethics are paramount. Employers need to trust that you will use your skills responsibly and follow the rules of engagement. Always act with integrity, respect client confidentiality, and follow legal/ethical guidelines (never hack anything without proper authorization). In interviews, you may be asked ethical questions (e.g., “What would you do if you discovered illegal activity during a test?”). Having a solid ethical compass and understanding of laws (like Malaysia’s CMA or Singapore’s CMA act) is part of the job.
- Adaptability and Quick Learning: The cyber landscape evolves constantly. New vulnerabilities, technologies, and attack methods appear every year. You should demonstrate that you can adapt and learn on the fly. Maybe a client uses a custom application or a new cloud service – you might need to research it during an engagement. Show enthusiasm for learning new things. Having a few self-learned projects (like “taught myself malware analysis basics” or “completed 50 rooms on TryHackMe”) on your resume can indicate you’re a quick study.
One more often-underrated skill: report writing. It’s worth emphasizing – the final deliverable of a pentest is usually a report. Good report writing (clear structure, risk ratings, actionable remediation steps) will make you stand out as a professional. It’s okay if you’re not an expert writer at first, but be prepared to put in effort to improve. You can find public pentest report templates and examples online to study their language and format.
Getting Hands-On: CTFs, Bug Bounties, and Home Labs 🛡️
Certifications and courses give you knowledge, but experience is what truly builds skill and confidence. The catch-22 is you need experience to get a job, but you need a job to get experience. The solution? Simulated and self-guided practice. Here are ways to gain practical experience in penetration testing before your first job:
-
Capture The Flag (CTF) Challenges: CTFs are cybersecurity competitions where you solve “puzzles” or hacking challenges to find a hidden flag (a secret code). They’re fun and extremely educational. Platforms like Hack The Box (HTB) and TryHackMe provide a variety of scenarios that mimic real-world pentest situations – from exploiting a vulnerable web app to cracking a network. By practicing on these, you learn by doing. Start with beginner-friendly CTFs: TryHackMe has guided paths (e.g., Complete Beginner path, Offensive Pentesting path). Over time, attempt HackTheBox machines; each “box” is a virtual machine with misconfigurations or vulnerabilities you must exploit to gain root access. As you progress, keep note of the techniques learned. Many local universities and communities in Malaysia and Singapore host CTF events too (often online). Participating in these competitions can also get you noticed – some companies sponsor or attend them to spot talent. Plus, you can mention your CTF achievements on your CV (e.g., “Solved 80+ challenges on TryHackMe, ranked top 10%”). This shows passion and hands-on skill.
-
Build a Home Lab: A home lab is your personal playground for hacking safely. It can be as simple as your laptop running VirtualBox with a couple of VMs. Set up an attack machine (Kali Linux VM) and a couple of target VMs (download intentionally vulnerable systems from VulnHub or use Docker images of DVWA, Juice Shop, etc.). Then practice different attacks in a controlled environment. Our guide on Debian Lab Setup provides a walkthrough for setting up a lab using Debian-based VMs, which you can adapt for Kali and target images. Try to simulate an actual pentest: scan the target, find a weakness, exploit it, then document what you did. Your home lab is also great for experimenting with tools you’re learning. For example, if you read about a new exploit in 2025, you can recreate it in your lab to see it in action. This kind of practice cements your understanding far more than just reading theory.
-
Bug Bounty Programs: Bug bounties are like real-world CTFs with cash rewards. Companies (like Facebook, Grab, or even government agencies) invite security researchers to test their public applications for vulnerabilities. If you find a valid security bug, you report it responsibly and can get a bounty (money or recognition). Platforms such as HackerOne, Bugcrowd, and Intigriti host programs from companies around the world. While it’s quite challenging to find unique bugs as a beginner (competition is fierce), participating in bug bounties teaches you how to test real, production systems legally. Start with smaller scope programs or those labeled “easy” or “good for beginners.” Even if you don’t find a severe bug, you might discover some minor ones and learn a lot in the process. Be sure to read write-ups from other hackers on their bug bounty findings – this gives insight into creative methodologies. We have a whole Bug Bounty Programs guide on our blog that explains how these programs work and tips to get started. Notably, in Singapore, the Government Technology Agency (GovTech) has run Government bug bounty programs on occasion, which is something to watch for locally. Bug bounties can even turn into job offers if you excel – some companies have hired top hackers from their bounty programs.
-
Open-Source Contributions and Personal Projects: A great way to stand out is by contributing to the security community. This could mean writing scripts/tools and open-sourcing them on GitHub, or contributing to existing projects. For example, you might write a new Nmap NSE script for a specific service, improve documentation for an open-source security tool, or share exploit code for a new CVE you researched. You could also develop your own small tool (maybe a Burp plugin or a recon script) and publish it. Employers love to see this kind of initiative because it shows you’re not just using tools, you understand them enough to build or improve them. Even if you’re not a coding wizard, you can contribute by writing write-ups of CTFs or vulnhub machines on a personal blog. Explaining how you compromised a target in a blog post demonstrates both skill and communication. If writing isn’t your thing, consider making a short video tutorial on a hacking technique – whatever medium, sharing knowledge reflects well on you. Plus, it helps others, which builds your network (people might recognize your handle on forums or social media for your contributions).
-
Internships or Apprenticeships: Don’t overlook internship opportunities or trainee programs. Some security consulting firms and large companies in Malaysia/Singapore offer internships in their cybersecurity teams. As an intern pentester or security analyst, you might start with assisting on vulnerability assessments, writing reports, or doing recon tasks – but you get exposure to real projects and mentorship from senior hackers. For instance, Malaysian firms like LGMS or Condition Zebra have been known to welcome fresh grads (their job posts often say “fresh graduates are welcome to apply” for junior roles). In Singapore, firms like PwC, Deloitte, and other consultancies have associate roles or internships in offensive security/red teaming. Even if an internship is not specifically titled “penetration testing,” a broader cyber internship (say in a SOC or IT security team) can provide relevant experience and foot in the door. It’s easier to pivot internally to pentest roles once you have some security work experience.
Pro tip: Treat your self-driven projects like real experience on your resume. Under a “Projects” section, list things like “Developed a home lab with 10 VMs to practice network and web penetration testing,” or “Solved over 100 CTF challenges across HackTheBox and TryHackMe platforms,” or “Reported 2 security vulnerabilities through bug bounty programs (XSS in [Company] web app, etc.).” These concrete achievements can impress hiring managers even if you haven’t held a formal pentest job yet. They show initiative and practical skill, which often counts as much as professional experience for entry-level candidates.

Navigating the Job Market: Landing Your First Pentester Role 💼
With your education, certs, and hands-on practice in place, the next step is to actually get that entry-level pentester job. Here’s how to approach the job hunt in Malaysia and Singapore, plus insight into the local market:
Job Titles to Search For: Entry-level penetration testing roles might not always be titled “Penetration Tester.” Also look for titles like “Cybersecurity Analyst,” “Security Consultant (Penetration Testing),” “Red Team Associate,” “Vulnerability Assessment Analyst,” or “Information Security Engineer.” In consulting companies, junior pentesters are often called Associate Consultants in Cybersecurity. In larger organizations (banks, telecom, etc.), the role might be under a security team with a broad title but involve pentesting tasks. So read job descriptions – if it mentions performing VAPT (Vulnerability Assessment and Penetration Testing), that’s essentially a pentest role even if the title is “Security Analyst.”
Top Employers and Sectors: In Malaysia, specialized cybersecurity firms (e.g., LGMS, Condition Zebra, LE Global, etc.) are known to hire penetration testers for client projects. Consulting and Big Four firms (Deloitte, PwC, EY, KPMG) have cybersecurity divisions and often recruit fresh grads as well – these roles expose you to a variety of industries via client engagements. Don’t overlook financial institutions (banks like Maybank, CIMB, DBS), telecom companies (Maxis, Singtel), and managed security service providers – they often have internal red teams or at least need pentesters for compliance. In Singapore, aside from similar consulting firms, many global companies have regional security teams based there. You’ll find openings at tech giants’ security teams, defense contractors, and government agencies (CSA, GovTech, DSTA) for those with the right clearances and qualifications. Even startups and fintech companies in SG are hiring security engineers to do continuous pentesting of their products. The Singapore cyber job market is robust with both local and international players – which is why you see over 1,600 cybersecurity job listings in Singapore on JobStreet in 2025.
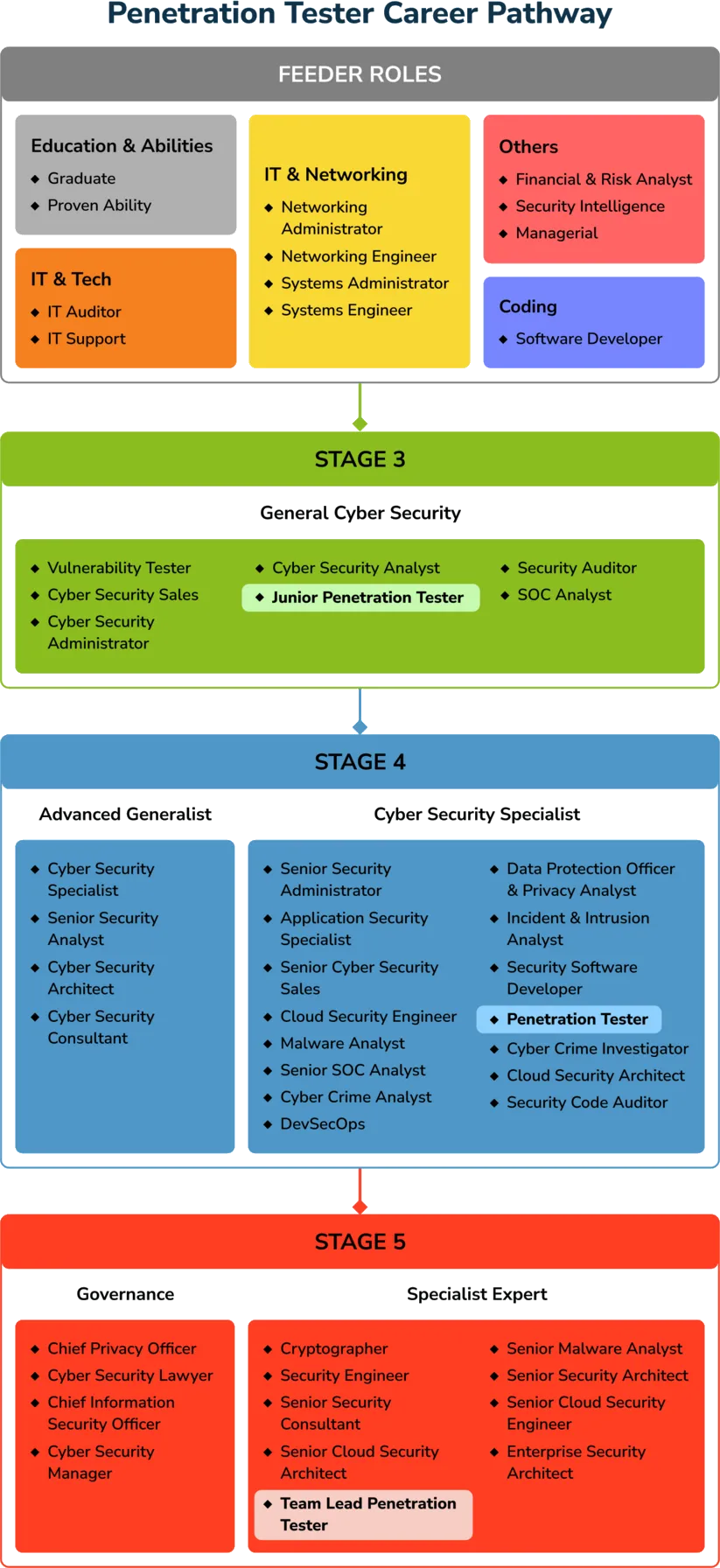
Credit: [StationX]
Where to Find Jobs: Leverage the popular job portals and networks:
✨ 🇸🇬 Click to check Top 20 Websites to Find IT Jobs in Singapore
| # | Website | Focus / Notes |
|---|---|---|
| 1 | MyCareersFuture | Official government portal; trusted source for local IT jobs |
| 2 | JobStreet SG | Popular across SEA; strong in tech, finance, and corporate hiring |
| 3 | LinkedIn Jobs | Top choice for IT professionals and remote-friendly opportunities |
| 4 | eFinancialCareers SG | Great for fintech, cyber risk, and IT roles in banking sector |
| 5 | Tech in Asia Jobs | Focused on startups, regional tech jobs, and remote options |
| 6 | NodeFlair | Singapore-based tech career platform with salary transparency |
| 7 | STJobs | Backed by The Straits Times, mostly local listings |
| 8 | JobTech | AI-driven platform that curates real-time job market data |
| 9 | Glints SG | Fast-growing platform for tech & creative roles, great for startups |
| 10 | JobsCentral SG | Covers both IT and non-IT sectors; good for fresh grads |
| 11 | StartupJobs Asia | Startup-centric, often includes equity-based and flexible roles |
| 12 | HackerTrail | Tech-specific hiring platform, includes coding challenges |
| 13 | Wantedly SG | Company culture-focused job search for startups and tech firms |
| 14 | Monster SG | International platform, useful for IT and expat positions |
| 15 | GrabJobs | Features chatbot-based application process, includes tech support roles |
| 16 | Xcruit | New-age job platform with integrated video resumes |
| 17 | InternSG | Best for internships, junior roles in IT, marketing, and engineering |
| 18 | TalentTribe | Visual job descriptions, focuses on tech and youth jobs |
| 19 | JobsDB SG | Still active, though many jobs are mirrored with JobStreet |
| 20 | DrJobs SG | Popular in the expat and overseas Singaporean community |
✨ 🇲🇾 Click to check Top 20 Websites to Find IT Jobs in Malaysia
| # | Website | Focus / Notes |
|---|---|---|
| 1 | JobStreet | Most popular job portal in Malaysia, strong IT category |
| 2 | Great for IT & cybersecurity, allows direct networking with employers | |
| 3 | JobsCentral | IT, engineering, and graduate jobs |
| 4 | Hiredly (WOBB) | Young, startup-friendly; includes internships & entry-level IT roles |
| 5 | myFutureJobs | Government portal, good for local IT and GLC jobs |
| 6 | Tech in Asia Jobs | Startup-focused, regional, many remote tech jobs |
| 7 | Glints | IT jobs in startups & SMEs, also has freelance and contract listings |
| 8 | FastJobs | Simple UI; has tech support, IT admin, and basic dev jobs |
| 9 | Jobstore | Broad platform, decent number of tech job listings |
| 10 | Indeed Malaysia | Global portal, wide range of local and expat-friendly IT roles |
| 11 | Job Majestic | Specializes in high-paying or niche roles, strong tech presence |
| 12 | FutureLab | Mentorship platform with growing job board for students and juniors |
| 13 | Monster Malaysia | Older platform but still lists IT jobs across Asia |
| 14 | Bossjob | AI-based matching, supports messaging employers directly |
| 15 | JobCart | Malaysian job portal gaining traction in tech & digital job markets |
| 16 | Jobify | Emerging site, startup jobs, internships, tech openings |
| 17 | Ricebowl | Bilingual portal (English/Chinese), includes tech jobs |
| 18 | TribeHired | For tech and startup talent, includes high-level developer roles |
| 19 | Maukerja | Blue-collar + tech support/IT admin roles |
| 20 | InternSheeps | Internships in IT, cybersecurity, and digital marketing |
✨ 🌐 Click to check Top 10 Fresh Remote IT Job Sites
| # | Website | Focus / Highlights |
|---|---|---|
| 1 | We Work Remotely | One of the oldest & largest platforms for remote software & DevOps jobs |
| 2 | Remote OK | Remote tech jobs with global employers; filter by timezone |
| 3 | Turing | U.S. companies hiring vetted remote developers from Asia |
| 4 | Remotive | Curated list of remote dev, cloud, and cyber jobs globally |
| 5 | Jobspresso | Remote-only jobs in tech, sysadmin, cybersecurity, product, and support |
| 6 | Working Nomads | Daily updated list of remote tech roles from global sources |
| 7 | Outsourcely | Remote jobs from startups looking to hire directly — no commission cuts |
| 8 | Pangian | Remote jobs with timezone matching; strong in tech, cyber, data |
| 9 | Hubstaff Talent | Free remote job marketplace for freelancers and long-term IT contracts |
| 10 | CodementorX | High-paying freelance/remote developer jobs, especially for experienced devs |
- JobStreet and JobsDB: These are heavily used in Malaysia and Singapore. A quick search for “penetration testing” or “cybersecurity” yields hundreds of openings (e.g., ~544 cyber security jobs in Malaysia as of May 2025). Set up email alerts on these sites for relevant keywords so you don’t miss new postings.
- LinkedIn: This is crucial. Keep your LinkedIn profile updated with your skills and projects. Follow companies you’re interested in and engage with their content. Many jobs get posted on LinkedIn or through recruiters scanning profiles. Networking on LinkedIn can lead to referrals – connect with cybersecurity professionals, join groups like “Cybersecurity Malaysia” or “SG InfoSec Community,” and share your own learning journey (it shows enthusiasm).
- Niche Job Boards: In Singapore, sites like MyCareersFuture (government portal) list tech jobs and sometimes grad programmes. Globally, sites like Indeed or Glassdoor also list local positions (Glassdoor showed 200+ cyber jobs in MY and 500+ in SG recently). Additionally, check specialized forums or community boards: the Malaysian cybersecurity community (e.g., LE-Global forum, local OWASP chapters) might share job leads; Singapore has groups like Division Zero (Div0) where jobs might be passed around.
- Career Fairs & Meetups: Attend tech career fairs (universities often host them – even if you’re alumni you can sneak in or join public tech fairs). Cybersecurity conferences or community meetups (e.g., BSidesKL, Hack In The Box, DevSecOps meetups, etc.) are great for networking. Bring business cards or just swap contacts – it might not yield an immediate job, but building relationships can lead to opportunities down the road. Many jobs, especially in a small industry like cybersecurity, come through word-of-mouth referrals.
Local Market Trends: In Malaysia, the government and industries are waking up to cybersecurity in a big way. There’s a push in sectors like finance, healthcare, and critical infrastructure to hire or outsource pentesters due to new regulations (for instance, healthcare providers are now required to beef up security after a Cyber Security Act). Additionally, Budget 2025 incentives (tax relief for companies investing in digital security) may spur more hiring of security vendors and experts. All this means lots of new openings. In Singapore, the trend includes a rise in contract roles and consultants – by 2025, an estimated 30% of tech pros in SG might be on contract, which includes pentesters engaged per project. This can be an opportunity: contract roles (or bug bounty/consultancy gigs) can be easier to land for newcomers and eventually convert to full-time. Also, both markets are seeing a focus on skills over degrees now, so your practical lab and CTF experience is going to be a plus.
Applying and Interviewing: Tailor your resume for each application. Highlight relevant skills (list the tools you know, the certs you have or are pursuing, and the practical projects you did). Use keywords like “penetration testing, vulnerability assessment, Kali Linux, OSCP, CTF, network security” – many HR screeners look for these. For fresh grads, listing coursework or final year projects related to security can help. A short cover letter or email expressing why you’re interested in that company and role (and how you can contribute) can set you apart since many don’t bother writing one. Be sure to mention any connection to the local context if applicable (e.g., “I’m an active member of [University’s] Cybersecurity Club, where we trained for CyberSEA Games 2024” or “I follow MAS cybersecurity guidelines closely” for SG banking jobs).
When you get called for an interview, be ready for both technical and behavioral questions. Some common entry-level pentester interview questions include:
- “Explain the steps you take in a penetration test.” – Here, talk through reconnaissance, scanning, exploitation, post-exploitation, reporting (show you know the methodology).
- “What are some common vulnerabilities you would look for in a web application?” – Mention things like SQL injection, XSS, broken access control, etc., perhaps referencing OWASP Top 10, and maybe an example of how you’d test for one.
- “Have you used [X tool] and what for?” – If they ask about Burp, Metasploit, or others you listed on your resume, be ready to describe a scenario of using it (for example, “Yes, I used Burp Suite to intercept and modify JWT tokens in a lab application to test access controls”).
- “How do you keep yourself updated in cybersecurity?” – They want to see passion. You could say you follow cybersecurity news, read blogs (like Top 10 Cybersecurity Threats to Watch in 2025), practice on HackTheBox, etc. This is where you mention your lab/CTF activities proudly.
- Behavioral questions: “Tell us about a challenging problem you solved,” or “How do you handle tight deadlines or learning something quickly?” – have a story ready perhaps about a CTF challenge you initially couldn’t solve but persevered, or how you self-learned a new tool under time pressure during a competition.
If the role is client-facing (consulting), they may also test your soft skills: e.g. role-play a scenario where you have to explain a vulnerability to a non-technical client. Practice simplifying technical jargon. Instead of saying “SQLi with UNION-based extraction of the user table,” you’d say “a database flaw that could allow an attacker to see all user records – like what happened in the XYZ breach – and here’s how to fix it.” Showing that you can communicate effectively will assure them you can handle real engagements.
Finally, don’t be discouraged by rejection. Cybersecurity is in demand but entry roles can still be competitive, especially in Singapore. You might apply to 20 jobs and hear back from 3 – that’s normal. Keep improving yourself in the meantime. Sometimes, taking a slightly adjacent job first helps (for example, a SOC analyst or IT security support role) and then transitioning internally to pentest after a year. Or perhaps a short contract gig leads to permanent. Be open to these pathways. The important thing is getting your foot in the industry door – once you have some experience, moving up and around becomes much easier.

Salary Expectations in 2025 💰
Let’s talk numbers. What kind of salary can you expect as a penetration tester in Malaysia or Singapore? Salaries vary based on your experience, certifications, the company’s size, and the sector. Below is a rough comparison of penetration tester salary ranges (monthly) in 2025 for Malaysia (MYR) and Singapore (SGD):
| Role Level | Malaysia (MYR) per month | Singapore (SGD) per month |
|---|---|---|
| Entry-Level Pentester (0–2 years) | RM 3,000 – RM 5,500 | $3,500 – $5,500 |
| Mid-Level Pentester (3–5 years) | RM 6,000 – RM 10,000 | $6,000 – $9,000 |
| Senior/Lead Pentester (5+ years) | RM 12,000 – RM 18,000+ | $10,000 – $15,000+ |
Notes: These figures are estimates for 2025. Entry-level in Malaysia might average around RM4k–5k for fresh graduates in KL, but could be lower (~RM3k) in smaller cities or higher (RM6k+) in top consulting firms or critical sectors. In Singapore, fresh graduates with a Bachelor’s in InfoSec often start around S$4k–5k at many companies, and those with a Master’s or some internship experience might get a bit more. The mid-level range corresponds to someone who has done a few years of testing and possibly has OSCP/CREST certs – these professionals are in high demand, hence the significant increase. Senior roles (lead consultants, team leads, principal testers) command very high salaries, especially in Singapore where talent is often poached by banks or MNCs. It’s not uncommon for a seasoned pentester in SG to break S$12k/month, and the very top experts or managerial leads can reach ~S$15-20k/month (which aligns with the ~SGD $200K annual figures seen in some reports).
In Malaysia, while absolute numbers are lower, the field is lucrative relative to general IT jobs. A senior pentester earning RM15k/month is doing extremely well, given the national averages. Also consider benefits: many companies provide bonuses, training allowances for certifications, and other perks which add value beyond base pay.
For context, globally the average pentester salary in 2025 is reported around $90k/year, and Singapore’s averages are about 120% higher than Malaysia’s on a USD basis. The gap reflects cost of living and market maturity. But the upside is that Malaysia’s demand is rising sharply, so salaries have been climbing and will continue to. Employers know they need to offer competitive pay to attract the limited talent available.
Salary negotiation tips: When you receive an offer, don’t hesitate to negotiate if you have evidence of your value (certifications achieved, internship experience, or competing offers). In Singapore, companies expect candidates to negotiate – just be polite and back your ask with reasoning. In Malaysia, there’s sometimes less room for fresh grads, but if you have something unique (say OSCP certified already), you can justify a higher start. Keep an eye on annual salary surveys by recruitment firms (e.g., Hays, Michael Page) which often list cybersecurity roles. For example, a 2024 survey might show a range for “Security Analyst” vs “Security Consultant” that you can cite. Additionally, factor in that some roles pay overtime or bonuses if you travel or handle many projects.
One more thing: contract roles in Singapore may offer higher monthly rates (since they often don’t include certain benefits). For instance, a contract pentester might get S$6k–7k as a fresher for a 1-year contract, which is a bit higher than a perm role, but be mindful of job stability and converting to perm later.
Ultimately, think of the first couple of years as an investment in learning. The salary will grow quickly as you prove yourself. With 5+ years of solid experience, you could even explore regional or global roles (some Malaysian experts take up jobs in Singapore or Middle East for a big jump, or remote gigs for US/EU companies). The pentesting career can be very rewarding both intellectually and financially.
Building Your Cybersecurity Profile (CV, Portfolio, Networking) 📋✨
Breaking into the industry requires more than just skills; you have to present those skills effectively. Here’s how to craft your personal brand and portfolio to impress recruiters and hiring managers:
-
Crafting a Strong Cybersecurity CV: Your resume should scream “cybersecurity” at a glance. Use a clear format and focus on relevant content. Start with a summary that mentions your key qualifications (degree or certs) and your passion for penetration testing (e.g., “Offensive security enthusiast with hands-on experience in ethical hacking labs and CTF competitions”). In the skills section, list technical skills like “Penetration Testing (Web App & Network), Vulnerability Assessment, Kali Linux, Metasploit, Burp Suite, Python, Linux administration, etc.” Include languages (programming and human, if relevant – e.g., knowing Malay or Chinese can be a plus in social engineering contexts). For experience, if you have formal experience (internships, freelance gigs), describe what you did specifically (e.g., “Performed security assessment of web application using Burp Suite and identified 5 major vulnerabilities”). For non-security jobs or school projects, try to frame tasks in a security or technical light: did you manage a server? develop software? That shows transferable skills. Include a “Projects” subsection where you list your lab and CTF endeavors: show that you walk the talk. For example: “Home Cyber Lab – Set up and secured a lab with 5 VMs, then conducted simulated attacks to practice exploits (e.g., buffer overflow on Windows Server)”; “Bug Bounty – Participated in HackerOne, received 2 hall of fame mentions for reporting XSS vulnerabilities”; “CTF – Ranked in top 10% on TryHackMe (username: yourhandle) with over 100 challenges solved.” These concrete examples can be discussed in interviews and prove you’re self-driven. Finally, list your certifications (even those in progress) and any relevant awards (maybe you won a CTF or got a scholarship). Keep the CV to 2 pages max, but make every line count.
-
Online Presence and Portfolio: In 2025, having an online portfolio is a differentiator. This could be as simple as a GitHub profile or a personal website/blog. If you have coding projects (exploit scripts, custom tools, CTF write-ups), put them on GitHub and share the link on your CV. Recruiters do check candidates’ GitHub or personal blog if provided – it can really boost your credibility. A personal blog is also a great idea: you could write articles like “How I hacked a vulnerable VM in 3 steps” or “My experience preparing for OSCP”. Optimize these posts with keywords (who knows, maybe a recruiter googling “entry-level pentester Malaysia” stumbles on your blog!). Since this is an SEO-focused guide: use LinkedIn to your advantage too. Write a post about your journey, incorporate keywords like penetration testing career, cybersecurity jobs in Malaysia, etc., and hashtags – it might catch the eye of someone hiring or at least help build your network. Also, ensure your LinkedIn profile is fully filled out, with a professional-looking photo, a headline like “Aspiring Penetration Tester | OSCP Certified (if applicable) | Cybersecurity Enthusiast”, and a summary highlighting your skills and ambition. Many recruiters in SG and MY actively search LinkedIn for terms like “OSCP” or “penetration testing”, so having those in your profile can lead to inbound opportunities.
-
Networking and Mentoring: Sometimes who you know can be as important as what you know. Engage with the cybersecurity community locally. Join Facebook or Telegram groups related to cybersecurity in Malaysia/Singapore. There are Discord servers for Hack The Box or local DefCon groups – be an active, positive participant. You might find a mentor this way or at least peers to study and share job tips with. Consider volunteering at cyber events (like helping organize a CTF or volunteering at conferences); it exposes you to industry professionals. When people see you’re passionate and involved, they’re more likely to refer you to openings. Don’t be afraid to reach out politely to professionals for advice – for example, if you find a senior pentester on LinkedIn who posts useful content, leave thoughtful comments or send a brief message appreciating their insights and maybe ask a specific question. Building genuine connections can lead to insider knowledge of openings or even recommendations.
-
Reference Your Knowledge of Local Context: When applying in Malaysia or Singapore, it helps to show you understand the local cybersecurity landscape. For instance, mention that you’re aware of relevant laws (PDPA, Cybersecurity Act) or standards (e.g., Threats prevalent in the region, compliance standards like Singapore’s Cybersecurity Code of Practice or Bank Negara’s guidelines). This isn’t required per se, but it’s a bonus point demonstrating you’re attuned to the environment you’ll work in. For example, a bank in Malaysia will be impressed if you know about RMiT (Risk Management in IT) guidelines that include pentest requirements. A company in Singapore might appreciate that you followed news of recent cyber incidents affecting SG companies. Our article on Top 10 Cybersecurity Threats to Watch in 2025 might give you some talking points on emerging threats in the region.
-
Continuous Improvement: Finally, outline a bit of your growth plan. Employers love candidates who have a vision for their professional development. You might say in interviews, “In the next year I plan to obtain the OSCP certification and specialize further in cloud penetration testing,” or “I’m working on improving my malware analysis skills to complement pentesting, as I know some roles value that crossover.” This shows you’re proactive and likely to continue adding value. Just be careful to convey this in a way that also shows you’re committed to the role at hand (they want to know you’ll stick around, not train up and jump ship immediately).

Real-World Insights and Next Steps 🚀
Embarking on a penetration testing career is challenging but incredibly rewarding. The journey involves wearing multiple hats: the student, the hacker, the consultant, the writer. It’s normal to feel overwhelmed at times by the sheer breadth of things to learn. The key is to take it step by step, and enjoy the process of continuous learning. As a final dose of motivation, here are a couple of insights from professionals and success stories:
Quote from a Local Professional: “In Singapore, where 92% of organizations have experienced breaches due to the cyber skills gap, it’s crucial for us to bridge that divide by building a well-trained workforce as the first line of defense against cyber threats,” notes Jess Ng, Country Head for Singapore at a global cybersecurity firm. This underlines that companies are very aware of the talent shortage – they need people like you! Even big firms are investing in training fresh talent, so don’t underestimate your value as an up-and-comer in the field.
Quote on Attitude: “Attitude is much more important than having done a certain course. If your heart’s not in it, you won’t keep up in penetration testing,” one expert pentester says. Take this to heart – a curious, can-do attitude will accelerate your career. Show that you’re genuinely interested in security beyond just landing a job: tinker with new tools, stay late to solve that last CTF challenge, share knowledge with peers. Employers notice and appreciate this spark.
Now, let’s outline some next steps you can act on immediately after reading this guide:
-
Make a Learning Plan: Write down which certification or skill you will tackle first and set a timeline. For example, “By July 2025, complete TryHackMe’s Pentesting pathway; By Oct 2025, pass the CompTIA Security+ exam; By Dec 2025, build a portfolio website.” Having a plan turns lofty goals into achievable tasks.
-
Join a Community: If you haven’t already, join a local cybersecurity group or online forum this week. For instance, sign up for CyberSecurity Malaysia’s community events or CSA’s Cyber Youth programmes. Being part of a community will keep you motivated and informed about opportunities (sometimes job openings get shared in these groups first!).
-
Apply for an Entry Opportunity: Don’t wait to feel “100% ready” – start applying for internships or junior roles as soon as you meet most of the requirements. Every interview, even if you don’t get the job, is practice and a chance to network. Remember to leverage internal links and resources: revisit our Cybersecurity Career Accelerator guide for general career tips, and our Social Engineering Roadmap to broaden your skillset into the human side of pentesting, which can make you a more versatile candidate.
-
Keep Updated and Stay Ethical: Set up a routine to follow cybersecurity news (like subscribing to ThreatPost or Follow CSA’s advisories). This keeps your knowledge relevant – for example, if a new critical vulnerability (like Log4Shell) emerges, you should know about it and perhaps even practice exploiting it in your lab. And always uphold the ethical code: only hack within legal boundaries (your lab, CTFs, or with permission). A mistake in ethics can ruin a budding career, whereas a strong ethical reputation will make you trusted and employable anywhere.
In conclusion, launching a penetration testing career in Malaysia and Singapore in 2025 is a journey filled with opportunities. The cybersecurity field here is hungry for talent, and with the roadmap provided – from education and certs to skills and job-hunting strategies – you have a solid game plan to join this exciting profession. Stay curious, stay persistent, and don’t be afraid to ask questions and seek mentors along the way. As you break into this field, you’re not just advancing your own career, but also contributing to a safer digital ecosystem in the region. Good luck, and happy hacking (ethically, of course)!

