Breaking into a Security Operations Center (SOC) and Security Information and Event Management (SIEM) career in 2025 can be one of the most rewarding paths in cybersecurity. SOC analysts are on the front lines defending organizations from cyber threats, and SIEM tools are their trusted weapons for detecting and investigating incidents. This ultimate guide will walk you through everything you need to know – from understanding what SOC and SIEM entail, to learning the skills, building your home lab and portfolio, certifications, job hunting tips, and more. Whether you’re in Malaysia, Singapore, or anywhere globally, these insights will help you launch a successful SOC analyst career. For a real-world architecture case study, read Building a 24/7 Tier-1 SOC in Malaysia.
What is a SOC (Security Operations Center)?
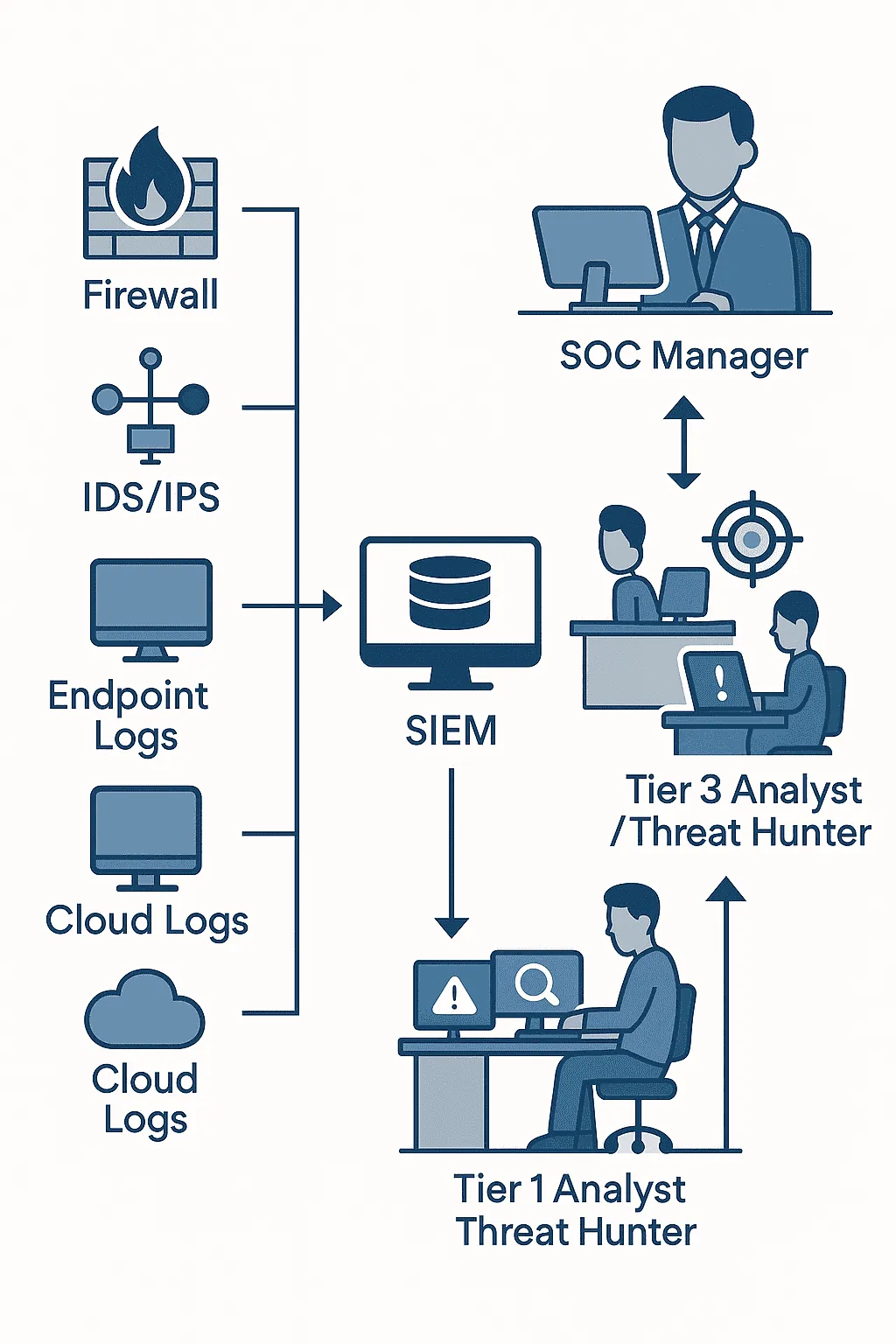
A Security Operations Center (SOC) is a dedicated team or facility where cybersecurity professionals monitor, detect, and respond to security incidents in real-time. Think of it as the “nerve center” of an organization’s cyber defense. The SOC team works 24/7 (often in shifts) to identify threats, analyze security alerts, and take action to protect the company’s digital assets.
Key functions of a SOC include:
- Continuous Monitoring: Using tools like SIEMs, intrusion detection systems, and dashboards to watch over network traffic, system logs, and user activities for any signs of threats.
- Incident Detection & Analysis: Investigating alerts and suspicious events to determine if they’re actual security incidents or false positives. SOC analysts often sift through thousands of alerts each day – making quick triage and analysis skills critical.
- Incident Response: When a real threat is confirmed, the SOC coordinates the response – containing the attack (e.g., isolating affected systems), mitigating damage, and recovering systems. They follow predefined incident response playbooks to handle common attack scenarios.
- Reporting & Compliance: Documenting incidents and creating reports for management and compliance requirements. This helps improve security posture and meet standards/regulations.
- Proactive Defense: Beyond reacting to attacks, many SOCs also proactively hunt for threats (threat hunting) and fine-tune security tools to better detect emerging threats.
In summary, a SOC is people + processes + technology all working together to guard an organization. Large organizations often have a physical SOC room with big screens and a team on computers, while smaller companies or startups might outsource this function to specialized providers.

What is SIEM (Security Information and Event Management)?
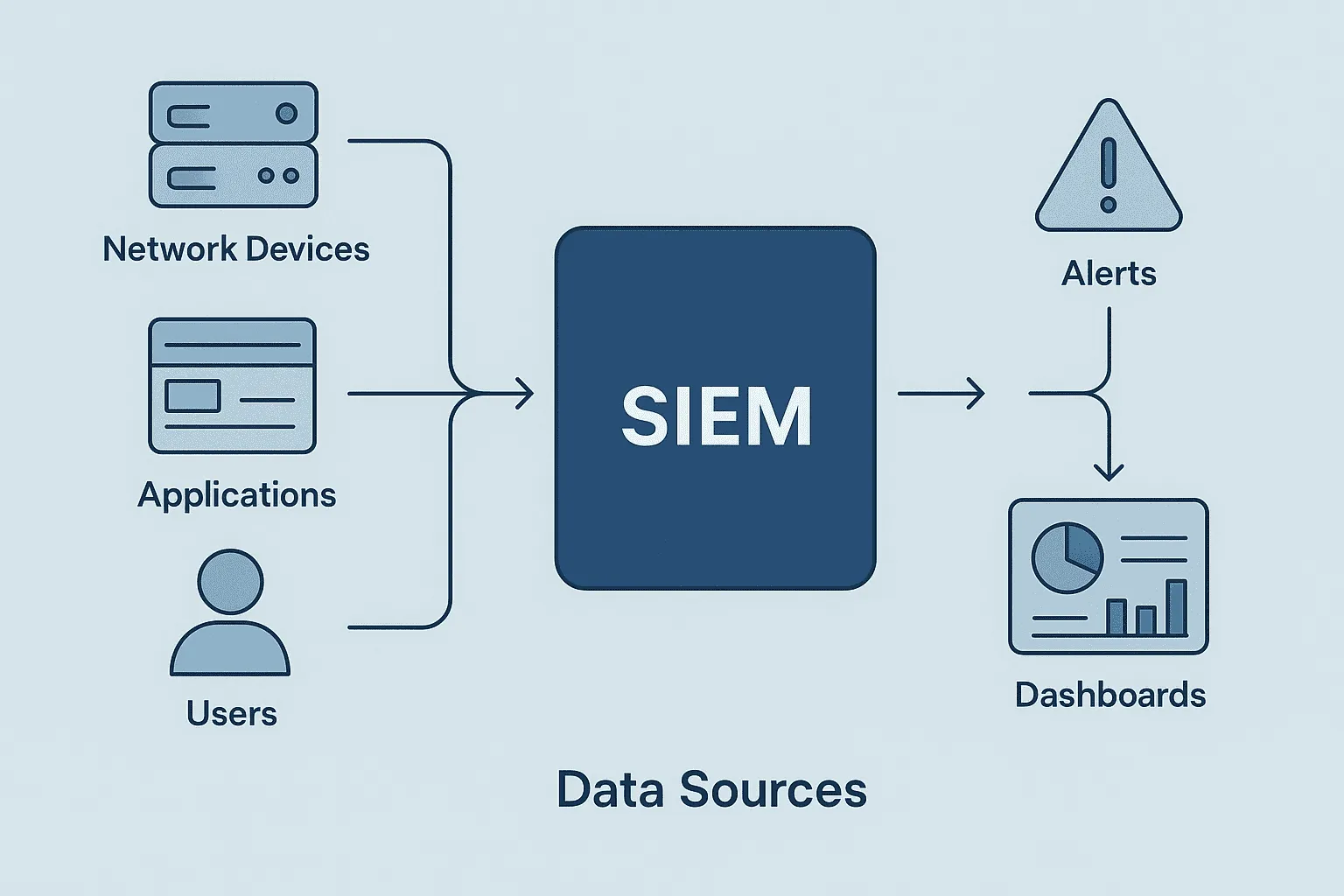
Security Information and Event Management (SIEM) is a category of software tools that aggregate and analyze activity from many different resources across your IT infrastructure. A SIEM collects log data and security events from sources like network devices, servers, applications, and endpoints, then correlates and flags suspicious patterns or anomalies in real-time.
In simpler terms, a SIEM is the central brain of the SOC – ingesting millions of log entries and highlighting the important ones so analysts can focus on real threats. Key capabilities of SIEM tools include:
-
Log Collection: Pulling in event logs from various sources (firewalls, antivirus, operating systems, cloud services, etc.) into one place.
-
Correlation & Detection: Using rules or machine learning to correlate events and detect attacks (e.g., multiple failed logins followed by a new account creation might indicate a breach).
-
Alerting: Generating alerts or notifications for SOC analysts when potentially malicious events are detected.
-
Forensics & Search: Allowing analysts to search through historical logs and data to investigate incidents (e.g. tracing the steps an attacker took).
-
Dashboard & Reporting: Providing dashboards that visualize security status and reports for trends, compliance, or management.
-
Retention: Storing log data for months or years for compliance or future analysis.
Still deciding what platform fits? See SIEM vs. SOAR — Which One Do You Need?.
Popular SIEM solutions include both commercial products (like Splunk, IBM QRadar, Microsoft Sentinel) and open-source platforms (like the Elastic Stack, Wazuh, and Graylog). We will compare these in detail later. For now, understand that SIEM knowledge is crucial for SOC analysts – you’ll spend a lot of time using one to investigate alerts and threats.
SOC Analyst Roles and Career Path (Tier 1, 2, 3 and Beyond)
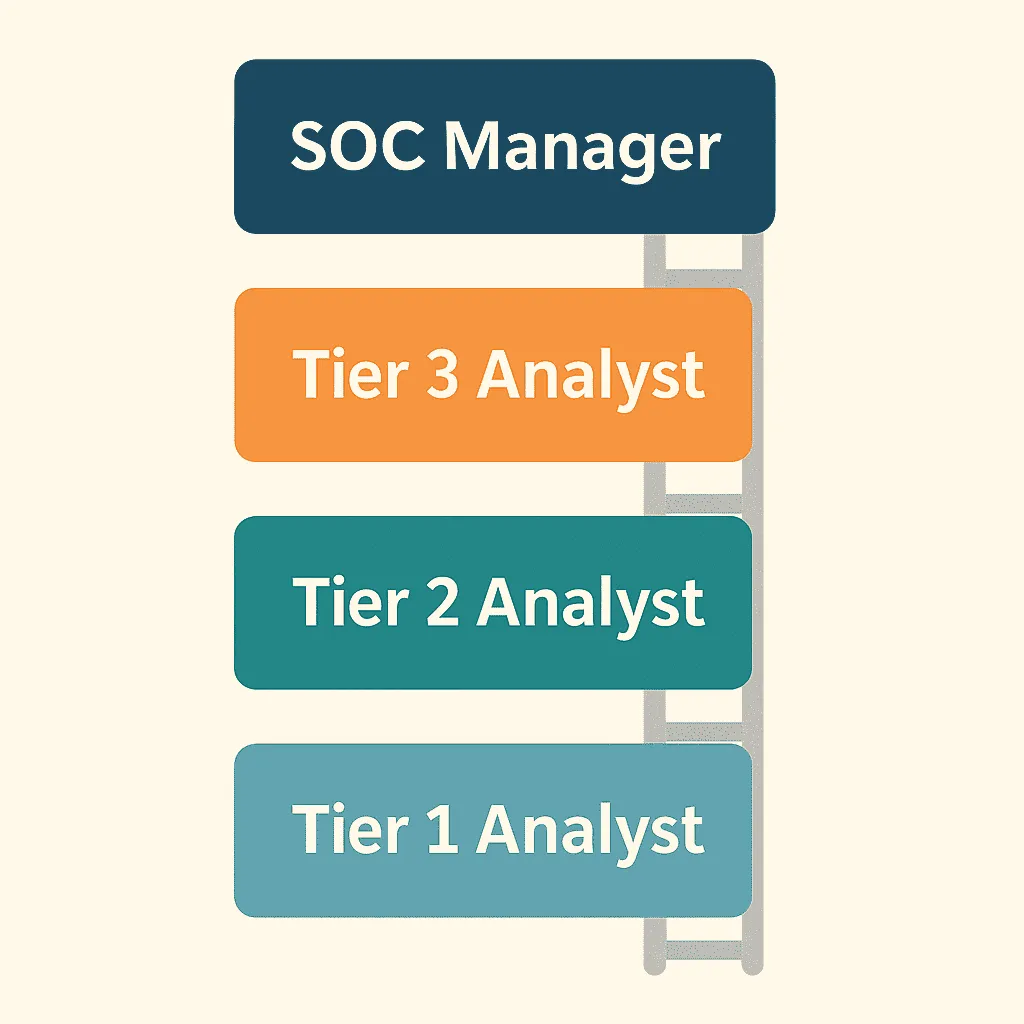
Within a SOC, there is typically a tiered structure of analysts, indicating different experience levels and responsibilities. This tiered model ensures that simpler tasks are handled by junior analysts, while more complex incidents go to experienced staff. Here’s how the SOC analyst career path generally looks:
Tier 1 – Junior SOC Analyst (L1): Tier-1 analysts are the first line of defense. They monitor incoming alerts and perform initial triage. Their job is to weed out false positives and escalate real threats to higher tiers. Responsibilities include monitoring SIEM alerts, basic investigation (checking event logs, IP addresses, virus scan results), and following standard operating procedures or playbooks for common events. They need strong attention to detail and the ability to stay calm under pressure as they often handle a high volume of alerts.
Tier 2 – Intermediate SOC Analyst (L2): Tier-2 analysts handle incidents escalated by Tier 1. They are more experienced and can perform in-depth investigations. Responsibilities include confirming breaches, analyzing malware or impacted systems, and taking containment actions (like disconnecting a compromised host, or blocking an attacker’s IP). They also coordinate with IT teams to remediate issues (e.g. applying patches, resetting credentials) and may fine-tune detection rules in the SIEM to reduce false positives. Tier-2 analysts have a solid technical background and typically 2-5 years of experience in security.
Tier 3 – Senior SOC Analyst / Threat Hunter (L3): Tier-3 analysts are experts who handle the most complex incidents and proactively hunt for threats that evade normal detection. Responsibilities include threat hunting (searching through networks and endpoints for stealthy indicators of compromise), deep-dive forensic analysis on logs or infected machines, and guiding the incident response process for critical incidents. They also mentor junior analysts and help design security monitoring strategies. L3 analysts often have 5+ years experience, and sometimes specialized skills in malware analysis, reverse engineering, or cyber threat intelligence.
SOC Lead / Manager: Above the tiers of analysts, many SOCs have a team lead or SOC manager. This person oversees the whole Security Operations Center – managing the team schedules, integrating new tools, setting up processes, and reporting to upper management on security metrics. They ensure the SOC runs efficiently and continuously improves. A SOC manager usually has years of hands-on experience plus management skills, and may advance to roles like Incident Response Director or Security Operations Director over time.
The tiered path isn’t the only route – some organizations might have specialized roles like Digital Forensics Investigator, Threat Intelligence Analyst, or SIEM Engineer (who manages and tunes the SIEM system). However, most entry-level folks start as SOC analysts (Tier 1) and work their way up the ladder as they gain experience.
Below is a summary of the SOC analyst tiers and their focus areas:
| SOC Role | Typical Experience | Key Focus & Responsibilities |
|---|---|---|
| Tier 1 SOC Analyst (L1) | 0–2 years (entry level) | Monitor alerts (SIEM, IDS); initial triage of events; identify false positives vs. real threats; follow playbooks for common incidents; escalate serious issues to Tier 2. |
| Tier 2 SOC Analyst (L2) | ~2–5 years (mid-level) | Deep investigation of incidents; malware analysis and network forensics; containment and remediation actions; coordinate with IT/engineering teams; adjust security tool rules to improve detection. |
| Tier 3 SOC Analyst / Threat Hunter (L3) | 5+ years (senior) | Proactive threat hunting in logs and systems; analyze advanced/stealth threats; lead incident response for major breaches; root cause analysis; develop new detection techniques; mentor junior analysts. |
| SOC Lead / Manager | 5–10+ years | Team leadership & mentoring; ensure 24/7 coverage; incident response planning; KPI reporting (e.g. response times, number of incidents); strategy and improving SOC processes; liaise with upper management. |
Essential Skills and Certifications for SOC Analysts
Becoming a SOC analyst requires a mix of technical know-how, analytical thinking, and communication skills. Here are some of the most important skills and knowledge areas you should build:
- Networking & Operating Systems: A solid grasp of how networks function (TCP/IP, ports, protocols) and how Windows/Linux systems work. Many attacks involve network traffic or OS-level exploitation, so you should understand things like firewall logs, Windows Event Logs, Linux commands, etc.
- Security Fundamentals: Know the common types of cyber attacks (malware, phishing, DDoS, SQL injection, etc.) and security concepts (encryption, authentication, etc.). Understanding the Cyber Kill Chain or MITRE ATT&CK framework can help in recognizing attack patterns.
- SIEM and Log Analysis: As mentioned, SIEM tools are central. Learn how to search and filter logs, create basic correlation rules, and interpret alerts. Being comfortable with at least one SIEM (like writing Splunk queries or Azure Sentinel KQL queries) is a big plus for job readiness.
- Threat Detection & Response: Learn the process of investigating alerts – how to trace an alert to source data, how to identify if it’s a false alarm or real incident, and steps to contain and eradicate threats. Familiarity with incident response processes (detection, analysis, containment, recovery, post-mortem) is key.
- Scripting and Automation: Basic scripting (Python, Bash, or PowerShell) can help automate repetitive tasks and parse through log data quickly. Many SOCs appreciate analysts who can write a quick script to, say, parse logs or automate a lookup. It’s not required to be a full programmer, but being script-savvy differentiates you.
- Communication and Reporting: SOC analysts must document incidents clearly and sometimes explain findings to non-technical managers. Strong written communication is needed for writing incident reports and Standard Operating Procedures (SOPs). Being able to present your findings in layman’s terms is also valued.
- Adaptability and Continuous Learning: The threat landscape evolves fast. A good SOC analyst is always learning about new vulnerabilities, hacker tactics, and new security tools. Curiosity and a proactive learning attitude will serve you well. For wider career planning tips, read Cybersecurity Career Accelerator.
Recommended Certifications: Earning industry certifications can boost your credibility. Here’s a roadmap of certifications commonly pursued by SOC professionals at different stages:
| Career Stage | Certifications to Consider |
|---|---|
| Entry-Level (0–1 years) | - CompTIA Security+: Establishes core cybersecurity knowledge (network security, threats, vulnerabilities) - (ISC)² Certified in Cybersecurity (CC): An entry-level cert by (ISC)² covering security basics - CompTIA Network+ (or Cisco CCNA): Solid understanding of networks (helpful for SOC work) |
| Intermediate (1–3 years) | - CompTIA CySA+: Focuses on cybersecurity analyst skills (threat detection, incident response) - EC-Council CEH: Certified Ethical Hacker (knowledge of hacking techniques, though CySA+ is more SOC-focused) - Splunk Core Certified User/Power User: Validates ability to use a popular SIEM tool (Splunk) effectively - Microsoft SC-200 (Security Operations Analyst): Shows skills in using Microsoft Sentinel and Defender in SOC operations |
| Advanced (3+ years) | - (ISC)² CISSP: Broad, management-level certification (often pursued once you have 5+ years experience) - GIAC GCIA or GCIH: SANS/GIAC certifications in intrusion analysis or incident handling (highly regarded technical certs) - ISACA CISM: Management-focused cert for those looking to move into leadership (requires experience) |
Keep in mind, certifications are optional but helpful. Many SOC analysts start without them, especially in entry-level roles, but having one can set you apart. For instance, Security+ is often considered a baseline cert for many junior cybersecurity jobs. In Malaysia and Singapore, HR departments sometimes filter resumes based on certifications like CEH or CISSP, so having those can increase your interview chances. Choose certs that align with your career stage and budget – and remember to balance studying for certs with gaining practical skills via labs and projects.
This roadmap organizes certifications into domains, skill levels (Expert, Intermediate, Beginner), and relevant sub-domains.
481 certifications listed | July 2024
✨ Communication and Network Security
The communication and network security domain covers the ability to secure communication channels and networks. Topics include secure and converged protocols, wireless networks, cellular networks, hardware operation (warranty and redundant power) and third-party connectivity. IP networking (IPSec, IPv4 and IPv6) are also included in this domain.
Expert
- CCIE Sec (Cisco Certified Implementation Expert - Security -
$2,050 Hands-on Lab, $12,000 est Travel cost) - CCIE Ent (Cisco Certified Internetwork Expert - Enterprise Infrastructure -
~$2,050 hands-on lab, ~$12,000 in travel costs) - JNCIE Sec (Juniper Networks Certified Internet Expert, Security -
$1,400 Hands-on Lab) - CCDE (Cisco Certified Design Expert -
~$1,600 written exam with hands-on lab) - FCX (Fortinet Certified Expert -
$400 written exam, $1600 in-person lab)
Intermediate
- CCNP Sec (Cisco Certified Network Professional - Security -
~$1,200 exam) - JNCIP Sec (Juniper Networks Certified Internet Professional, Security -
$400 exam) - PCNSE (Palo Alto Networks Certified Network Security Engineer -
$175 exam) - FCSS ZTA (Fortinet Certified Solution Specialist - Zero Trust Access -
$800 two exams) - F5 CSE Sec (F5 Big-IP Certified Solution Expert - Security -
$135 exam) - CCNP Ent (Cisco Certified Network Professional - Enterprise -
~$600 exam) - CCSM (Checkpoint Certified Security Master -
$350 exam) - PCSAE (Palo Alto Certified Cloud Security Automation Engineer -
$350 exam) - PCCSE (Prisma Certified Cloud Security Engineer -
$350 exam) - FCSS NS (Fortinet Certificed Solution Specialist - Network Security -
$800 two exams) - CCSE (Checkpoint Certified Security Expert -
$250 exam) - JNCIS Sec (Juniper Networks Certified Internet Specialist, Security -
$300 exam) - F5 CTS APM (F5 Big-IP Certified Technical Specialist - Access Policy Manager -
$135 exam) - FCP NS (Fortinet Certified Professional - Network Security -
$400 for 2 exams) - CCNA (Cisco Certified Network Associate -
~$330 exam) - F5 CTS DNS (F5 Big-IP Certified Technical Specialist - Domain Name Services -
$135 exam) - PCDRA (Palo Alto Networks Certified Detection and Remediation Analyst -
$155 exam) - CWSP (CWNP Certified Wireless Security Professional -
$325 exam) - CREST CCNIA (CREST Certified Network Intrusion Analyst -
$2,481 exam & essay, Hands on exam in UK)
Beginner
- F5 CA (F5 Big-IP Certified Administrator -
$135 exam) - eNDP (eLearnSecurity Network Defense Professional -
$400 exam) - MNSE (Mosse Institute Network Security Essentials -
$450 certification programme, 100% practical. No expiry.) - PCNSA (Palo Alto Networks Certified Network Security Administrator -
$155 exam) - OWSE (ISECOM OSSTMM Wireless Security Expert -
$100 annual sub, Unknown exam cost) - JNCIA Sec (Juniper Networks Certified Internet Associate, Security -
$200 exam) - FCA (Fortinet Certificed Associate -
Free course and exam required) - WCNA (Protocol Analysis Institute Wireshark Certified Network Analyst -
$299 exam) - CCSA (Checkpoint Certified Security Administrator -
$250 exam) - ITS-NS (Certiport IT Specialist - Network Security -
$127 exam) - CCT (Cisco Certified Technician -
$165 exam) - SOG NSP (SecOps Group Certified Network Security Practitioner -
$249 exam) - Net+ (CompTIA Network+ -
$369 exam) - FCF (Fortinet Certified Fundamentals Cybersecurity -
Free 3 courses with exams req) - PCCET (Palo Alto Networks Certified Cybersecurity Entry-level Technician -
$110 exam)
✨ IAM (Identity and Access Management)
(The identity and access management domain covers the attacks that target the human gateway to gain access to data. Other topics include ways to identify users with rights to access the information and servers. Identify and access management covers the topics of applications, Single sign-on authentication, privilege escalation, Kerberos, rule-based or risk-based access control, proofing and establishment of identity.)
Intermediate
- CIMP (Identify Management Institute Certified Identity Management Professional -
$295 + Membership) - FCSS SASE (Fortinet Certified Solution Specialist - Secure Access Service Edge -
$800 two exams) - CIAM (Identify Management Institute Certified Identify and Access Manager -
$390 Exam) - CIDPRO (IDPro Certified Identity Professional -
$700 exam) - SF CIAMD (SalesForce Certified Identity and Access Management Designer -
$400 exam) - CIGE (IMI Certified Identity Governance Expert -
$395 exam)
Beginner
- CIST (IMI Certfied Identity and Security Technologist -
$295 exam) - SC-300 (Microsoft Certfied: Identity and Access Administrator Associate -
$165 exam) - CAMS (IMI Certfied Access Management Specialist -
$195 exam) - SC-900 (Microsoft Certified: Security, Compliance, and Identity Fundamentals -
$99 exam)
✨ Security Architecture and Engineering
(The security architecture and engineering domain covers important topics concering security engineering plans, designs, and principles. Topics include assessing and mitigating information system vulnerabilities, fundamental concepts of security models and security architectures in critical areas like access control. Cloud systems, cryptography, system infiltrations (ransomware, fault-injection and more) and virtualized systems are also covered in this domain.)
Expert
Cloud/SysOps
- VCDX DCV (VMware Certified Design Expert in Datacenter Virtualization-
$3,995 exams, Application also req.) - VCIX DCV (VMware Certified Implementation Expert in DatacenterVirtualization -
$900 two exams) - AWS SAP (Amazon Web Services CertifiedSolutions Architect - Professional -
$300 exam) - AZ-305(Microsoft Azure Solutions Architect Expert -
$330 exam) - VCIX NV (VMware Certified Implementation Expert in NetworkVirtualization -
$900 two exams) - Google PCSA(Google Professional Cloud Architect -
$200 exam)
*nix
- RHCA (Red HatCertified Architect -
~$3,745 exam, plus travel) - RHCE (Red HatCertified Engineer -
$400 exam) - LPIC-3(Linux Professional Institute Certified: 303 Security -
$200 exam) - SCE (SUSE CertifiedEngineer -
$195 practical exam)
ICS/IoT
- ISA CE (ISACybersecurity Expert -
$2,700 course + exam, Course required) - CACE (Excida IEC 62443 CertifiedAutomation Cybersecurity Expert -
$700 exam)
General Engineering
- CREST CRTSA (CREST Registered TechnicalSecurity Architect -
$2,300 two exams, In person in the UK) - SABSA SCM (SABSA Chartered SecurityArchitect - Master Certificate -
$3,750 exam & thesis, Branded courserequired) - GDAT(GIAC Defending Advanced Threats -
$979 exam, SANS course recommended) - SC-100(Microsoft Cybersecurity Architect -
$165 exam) - SABSA SCP (SABSA Chartered SecurityArchitect - Practitioner Certificate -
$3,750 written exam, Branded courserequired) - GDSA (GIAC Defensible SecurityArchitecture -
$979 exam, SANS course recommended)
Intermediate
Cloud/SysOps
- FCSS PCS (Fortinet Certified Solution Specialist -Public Cloud Security -
$400 exam) - GCTD(GIAC Cloud Threat Detection -
$979 exam, SANS course recommended) - MS-100 (Microsoft 365 Certified EnterpriseAdministrator Expert -
$165 exam) - GPCS(GIAC Public Cloud Security -
$979 exam, SANS course recommended) - GCSA(GIAC Cloud Security Automation -
$979 exam, SANS course recommended) - FCSS SO (Fortinet Certified Solution Specialist -Security Operations -
$400 exam) - PDSO CDE(PDSO Certified DevSecOps Expert -
$1199, Exam and training bundled) - VCP DCV (VMware Certified Professional in Datacenter Virtualization -
$375exam, Branded course required) - CCSP ((ISC)2 Certified CloudSecurity Professional -
$599 exam) - FCP PCS (Fortinet Certified Professional - PublicCloud Security -
$400 for 2 exams) - AWS CSS(Amazon Web Services Certified Security - Specialty -
$150 exam) - SFCCCC(SalesForce Certified Community Cloud Consultant -
$200 exam, Must beSalesForce Admin Certified) - EXIN PCSA (EXIN Professional CloudSolution Architect -
$315 exam) - VCP NV (VMware Certified Professional in Network Virtualization-
$375 exam, Branded course required) - AZ-500 (MicrosoftAzure Security Engineer Associate -
$165 exam) - CSA CGC (Cloud Security Alliance CloudGovernance & Compliance -
$315 exam) - GCLD (GIAC Cloud Security Essentials -
$979exam SANS course recommended) - AWS SAA (Amazon Web Services CertifiedSolutions Architect - Associate -
$150 exam) - EXIN PCSerM (EXIN Professional CloudService Manager -
$315 exam)
*nix
- GCWN (GIAC Certified WindowsSecurity Administrator -
$979 exam, SANS course recommended) - CKS (Cloud Native ComputingFoundation Certified Kubernetes Security Specialist -
$375 lab, Brandedcourse required) - LFCS (Linux Foundation CertifiedSystem Administrator -
$300 exam) - FCP SO (Fortinet Certified Professional - SecurityOperations -
$400 for 2 exams) - RHCSA (Red HatCertified System Administrator -
$400 exam) - CKA (Cloud Native ComputingFoundation Certified Kubernetes Administrator -
$375 lab, Branded courserequired) - LPIC-2 (LinuxProfessional Institute Certified: Linux Engineer -
$400 2 exams)
ICS/IoT
- GRID (GIAC Response and Industrial Defense -
$979 exam, SANS course encouraged) - CSSA(Infosec Institute Certified SCADA Security Architect -
$4,599 exam, Courserequired) - ISA CDS (ISA Certified DesignSpecialist -
$2,700 course + exam) - TUV COTCP(TUV Rheinland Certified Operational Technology Cybersecurity Professional(GERMAN) -
$415 exam) - GCIP (GIAC Critical InfrastructureProtection -
$979 exam, SANS course encouraged) - ISA CRAS (ISA Certified RiskAssesment Specialist -
$2,700 course + exam, Course required)
General Engineering
- CIS LI (IBITGQ CertifiedISO 27001 Information Security Management Specialist Lead Implementer -
$2008 course exam, Branded course required) - SFCTA (SalesforceCertified Technical Architect -
$6000, Must be SF SA Certified) - SABSA SCF (SABSA Chartered Security Architect- Foundation Certificate -
$3,750 exam, Branded course required) - SPLK-3001 (Splunk Enterprise Security CertifiedAdministrator -
$130 exam, Branded course recommended) - SFSA (SalesForceSystem Architect -
$400 hands-on lab) - CCSE (ECCouncil Certified Cloud Security Engineer -
$100 exam, EC Council CourseRecommended) - MCSE (Mosse Institute Cloud SecurityEngineer -
$600 exam)
Beginner
Cloud/SysOps
- Google PCSE (Google Professional Cloud Security Engineer -
$200 exam) - EXIN PCSM (EXIN Professional CloudSecurity Manager -
$315 exam) - MDSO (Mosse Institute Certified DevSecOpsEngineer -
$450 exam) - CSA CCSK (Cloud SecurityAlliance Certificate of Cloud Security Knowledge -
$395 exam) - C)CSO (Mile2 Certified Cloud SecurityOfficer -
$550 exam) - Server+ (CompTIA Server+-
$319 exam) - PDSO CDP (PDSO Certified DevSecOps Professional -
$799, Exam and training bundled) - EXIN PCD (EXIN Professional Cloud Developer -
$315 exam) - Cloud+ (CompTIA Cloud+ -
$369 exam) - Google ACE(Google Associate Cloud Engineer -
$125 exam) - SOG CCSP-AWS (SecOps Group CertifiedCloud Security Practitioner - AWS -
$249 exam) - AWS CP(Amazon Web Services Certified Cloud Practitioner -
$100 exam) - EXIN PCA (EXIN Professional CloudAdministrator -
$315 exam) - Cloud Essnt(CompTIA Cloud Essentials -
$138 exam)
*nix
- SCA (SUSE CertifiedAdministrator -
$149 exam) - DCA (Docker CertifiedAssociate -
$195 exam) - LPIC-1 (LinuxProfessional Institute Certified: Linux Administrator -
$400 2 exams) - KCNA (Cloud Native ComputingFoundation Kubernetes and Cloud Native Associate -
$250 exam, Brandedcourse required) - Linux+ (CompTIA Linux+ -
$369 exam) - LFCA(Linux Foundation Certified IT Associate -
$200 exam) - Apple ACSP (Apple CertifiedSupport Professional -
$250 exam, Limited test locations) - A+ (CompTIA A+ -
$253 exam)
ICS/IoT
- ISA CAP (ISA CertifiedAutomation Specialist -
$467 exam) - TUV COSM (TUV Certified OTSecurity Manager -
$3,070 Course) - GICSP (GIAC Global IndustrialSecurity Professional -
$979 exam, SANS course encouraged) - AZ-220(Azure IoT Developer Specialty -
$165 exam) - ISA CFS (ISA CertifiedFundamentals Specialist -
$2,700 course + exam, Course required) - EITCA/IS (EITCA/ISInformation Security Certificate -
$120 exam) - CACS (Excida IEC 62443 CertifiedAutomation Cybersecurity Specialist -
$700 exam) - TUV COSP (TUV Certified OTSecurity Practitioner -
$2725 course) - CIOTSP (CertNexus CertifiedInternet of Things Security Practitioner -
$250 exam)
General Engineering
✨ Asset Security
(The Asset Security domain deals with the issues related to the collection, storage, maintenance, retention and destruction of data. It also covers knowledge of different roles regarding data handling (owner, controller and custodian) as well as data protection methods and data states. Other topics include resource provision, asset classification and data lifecycle management.)
Expert
- ASIS CPP (ASIS Certified Protection Professional -
$485 exam)
Intermediate
- CIPT (IAPP Certified Information Privacy Technologist -
$550 exam) - CDPSE (ISACA Certified Data Privacy Solutions Engineer -
$880 Application) - EPDPP (EXIN Privacy and Data Protection Practitioner -
$243 Exam, Course req'd) - CIPA (IMI Certified Identity Protection -
$295 Exam) - DCPP (DSCI Certified Privacy Professional -
$205 Exam) - CIMP (IMI Certified Identity Management Professional -
$295 Exam) - CDP (IMI Certified in Data Protection -
$395 Exam)
Beginner
- ASIS APP (ASIS Associate Protection Professional -
$350 exam) - CRFS (IMI Certified Red Flag Specialist -
$295 exam) - CIPP (IAPP Certified Information Privacy Professional -
$550 exam) - EPDPF (EXIN Privacy and Data Protection Foundation -
$207 exam) - EPDPE (EXIN Privacy and Data Protection Essentials -
$145 exam)
✨ Security and Risk Management
(The security and risk management domain covers general on skills related to the implementation of user awareness programs as well as security procedures. Emphasis is also placed on risk management concerning the acquisition of new services, hardware and software (supply chain). Other skills include social engineering defense mechanisms.)
Expert
- ITIL Master (ITIL Master -
$4,000 Interview) - GSE (GIAC Security Expert -
~$7475 for 10 exams) - PgMP (PMI Program Management Professional -
$1,000 exam) - CISSP Concentrations ((ISC)2 Certified Information Systems Security Professional Concentrations -
$599 exam) - NCSC CCPLP (NCSC Certified Cybersecurity Professional - Lead Practitioner -
$1388 interview) - Zach EAPro (Zachman Enterprise Architect Professional (Level 3) -
$2,999 exam & case study, Level 1 & 2 cert not req'd) - PMP (PMI Project Management Professional -
$555 exam) - CISM (ISACA Certified Information Security Manager -
$760 exam) - S-ISME (SECO Information Security Management Expert -
$850 exam) - NCSC CCPSP (NCSC Certified Cybersecurity Professional - Senior Practitioner -
$907 interview) - CISSP ((ISC)2 Certified Information Systems Security Professional -
$749 exam) - TOGAF (OpenGroup TOGAF Certified -
$360 exam) - CCISO (EC Council Certified Information Security Officer -
$3,150 course exam, Branded course required) - EEXIN ISM (EXIN Information Security Management Expert -
EST $799 oral exam) - GSTRT (GIAC Strategic Planning, Policy and Leadership -
$979 exam, SANS course recommended) - NCSC CCPP (NCSC Certified Cybersecurity Professional - Practitioner -
$225 interview) - PSM III (Scrum.org Professional Scrum Master III -
$500 exam, Branded course required) - GSP (GIAC Security Professional -
~$3735 for 5 exams) - GISP (GIAC Information Security Professional -
$979 exam, SANS course recommended)
Intermediate
GRC (Governance, Risk, and Compliance) & General Management
- ITIL SL (ITIL Strategic Leader -
$4,800 two courseexams, 2 branded courses required) - Zach EAP (Zachman Enterprise Architect Practitioner (Level 2) -
$2,999 exam & case study, Level 1 cert not req'd) - GSLC (GIAC Security LeadershipCertification -
$979 exam, SANS course recommended) - S-CISO (SECO Certified InformationSecurity Officer -
Resume review) - CASP+ (CompTIA Advanced SecurityPractitioner+ -
$509 exam) - ITIL MP (ITIL Managing Professional -
$9,600 4course exams, 4 branded courses requires) - Scrum SPS(Scrum Scaled Professional Scrum -
$250 exam) - GLEG (GIAC Law of Data Security &Investigations -
$979 exam, SANS course recommended) - CISSM (GAQMCertified Information Systems Security Manager -
$170 exam) - CGRC ((ISC)2 Certified inGovernance, Risk and Compliance -
$599 exam) - CRISC (ISACA Certified inRisk and Information Systems Control -
$760 exam) - CSM (GAQM Certified ScrumMaster -
$128 exam) - CASM (GAQM Certified AgileScrum Master -
$128 exam) - CM)ISSO (Mile2 Certified MasterInformation Systems Security Officer -
Complete C)SP, C)ISSO, C)ISSM andIS20 ($2200)) - S-ISP (SECO Information SecurityPractitioner -
$550) - Scrum PSD (Scrum Professional ScrumDeveloper -
$200 exam) - GCPM (GIAC Certified ProjectManager -
$979 exam, SANS course recommended) - BCS PCIRM (BCSPractitioner Certificate in Information Risk Management -
$287 exam) - PEXIN ISM (EXINInformation Security Management Professional -
$268 exam) - MGRC (Mosse Institute Certified GRC ExpertCertification -
$450 certification programme, 100% practical. No expiry.) - M_o_R P (Axelos M_o_R Practitioner Risk Management -
$560 exam) - CPD (GAQM CertifiedProject Director -
$210 exam) - PMI ACP (PMI Agile CertifiedPractitioner -
$495 exam) - EISM (EC CouncilInformation Security Manager -
$3,499, Branded course required) - CGEIT (ISACA Certified in theGovernance of Enterprise IT -
$760 exam) - EXIN 27001E (EXIN ISO/IEC 27001 Expert -
~$379 OralPresentation) - PECB 27005LM (PECB ISO/IEC 27005 Lead RiskManager -
~$1,595 exam, Course required) - DCCRP (DRI Certified Cyber ResilienceProfessional -
$400 Exam) - Scrum PAL (Scrum Professional AgileLeadership -
$200 exam) - CAPM (PMICertified Associate in Project Management -
$300 exam) - PSM II (Scrum.org Professional ScrumMaster II -
$250 exam) - APMG 20000P (APMG ISO/IEC20000 Practitioner -
$308 Exam, Foundation or ITIL req'd) - C)ISRM (Mile2Certified Information Systems Risk Manager -
$550 exam) - APMG 27001P (APMG ISO/IEC27001 Practitioner -
$400 exam, Application essay) - PECB 27001LI (PECB ISO/IEC 27001 LeadImplementer -
$930 exam, Course required) - Programming Language (Learning a programminglanguage is valuable to any IT professionals career. Recommendations:Python, Ruby, C++)
- CCP (EC First Certified CCMC Professional -
$2,995 exam, Courserequired) - C)ISSO (Mile2 Certified InformationSystems Security Officer -
$550 exam) - CIS RM (IBITGQ Certified ISO 27005Information Security Management Specialist Risk Management -
$2,783 courseexam, Branded course required) - EXIN 27001P (EXINISO/IEC 27001 Professional -
$279 exam) - PECB 27032CM (PECB ISO/IEC 27032Lead Cybersecurity Manager -
$899-$2,999 course exam, Course required) - C)HISSP (Mile2 Certified HealthcareInformation Systems Security Practitioner -
$550 exam) - BCS PCIAA (BCSPractitioner Certificate in Information Assurance Architecture -
$290 exam) - CCSA (EC First Certified Cyber Security Architect -
$695 exam) - PPM (GAQM Professionalin Project Management -
$210 exam) - C)ISSM (Mile2 Certified InformationSystems Security Manager -
$550 exam) - TUV ITSM (TUV ITSecurity Manager (GERMAN) -
$415 exam, Course required) - CCRMP (IBITGQ Certified in ManagingCyber Security Risk -
$2,629 course exam, Branded course required) - PECB 27005RM (PECB ISO/IEC 27005 Risk Manager -
~$995 exam, Course required) - CSBA (QAI CertifiedSoftware Business Analyst -
$350 exam + written essay)
Beginner
- CNDA (EC Council Certified NetworkDefense Architect -
$200 application, Requires CEH cert) - DACRP (DRI Associate Cyber ResilienceProfessional -
$200 exam, Course req) - CISRM (IBITGQ Certified ISO 27005Information Security Management Specialist Risk Management -
$2,783 courseexam, Branded course required) - DCRMP (DRI Certified Risk ManagementProfessional -
$400 exam, Application essay) - SSAP (SANS Security Awareness Professional -
$1219 Exam, SANS MGT433 courserecommended) - GRCP (OCEG Governance, Risk, and Compliance Professional -
$399 12 monthlicense) - SACP (The H Layer Security Awareness and CultureProfessional -
$369 Exam) - CISP (GAQMCertified Information Security Professional -
$170 exam) - Zach EAA (Zachman Enterprise Architect Associate (Level 1) -
$2,999 course exam, Branded course required) - CAD (GAQM Certified AgileDeveloper -
$128 exam) - CAC (GAQM Certified Agile Coach-
$170) - ISMI CSMP (ISMI CertifiedSecurity Management Professional -
$1159) - CSCS (EC First Certified Security Compliance Specialist -
$695exam) - APMG 27001F (APMG ISO/IEC27001 Foundation -
$400 exam, Application essay) - PECB 27001F (PECB ISO/IEC 27001 Foundation -
$500-749 exam, Course required) - C)SLO (Mile2 Certified Security LeadershipOfficer -
$550 exam) - GSEC(GIAC Security Essentials Certification -
$979 exam, SANS courserecommended) - SSCP ((ISC)2 SystemsSecurity Certified Practitioner -
$249 exam) - Security+ (CompTIASecurity+ -
$404 exam) - M_o_R Fdn (Axelos M_o_R Framework Foundation -
$495 exam) - Fair Fdn (Fair Institute Analysis Fundamentals-
$1499 exam, Course required) - PSM I (Scrum.org Professional ScrumMaster I -
$150 exam) - APMG 20000F (APMG ISO/IEC20000 Foundation -
$308 exam) - ISMI CSM (ISMICertified Security Manager -
$TBD) - BCS FISMP(BCS Foundation Certifiate in Information Security Management Principles -
$249 exam) - CC (ISC2 Certified inCybersecurity -
Free exam) - S-ISF (SECO Information SecurityFoundation -
$460 exam) - GISF (GIAC Information SecurityFundamentals -
$979 exam, SANS course recommended) - ITIL Fdn (ITIL Foundation -
$383 exam) - Project+ (CompTIA Projec+ -
$369 exam) - CIISec ICSF (CIISec Information andCybersecurity Fundamentals -
$450 exam) - FEXIN (EXIN Information Security Foundation -
$232exam) - EXIN 27001F (EXIN ISO/IEC27001 Foundation -
$232 exam) - PECB 27005F (PECB ISO/IEC 27005 Foundation -
$500-749 exam, Course required) - C CS F (IBITGQ Certified CyberSecurity Foundation -
$725 course exam, Branded course required) - CIS F (IBITGQ Certified ISO27001 Information Security Management Specialist Foundation -
$853 courseexam, Brandeed course required) - CSP (GAQM Certified SAFePractitioner -
$170 exam) - IIBA CCA (IIBA Certification in CybersecurityAnalysis -
$475 exam) - CITGP (IBITGQCertified in Implementing IT Governance - Foundation & Principles -
~$2,499course exam, Branded course required) - C)ISCAP (Mile2 Information SystemsCertification and Accredidation Professional -
$550 exam) - CSAP(Infosec Institute Certified Security Awareness Practitioner -
$2,599 exam,Course required) - PECB 27032F (PECB ISO/IEC 27032 Foundation -
$500-749 exam, Course required) - MCL (Mosse Institute Cybersecurity Leadership-
$450 exam) - ITS-C (Certiport ITSpecialist - Cybersecurity -
$127 exam)
✨ Security Assessment and Testing
(The security assessment and testing domain deals with all the techniques and tools used to find system vulnerabilities, weaknesses and potential areas of concern not addressed by security procedures and policies. Attack simulations, vulnerability assessment, compliance checks, and ethical disclosure also fall under this domain.)
Intermediate
- GSNA (GIAC Systems and Network Auditor -
$979 exam, SANS course recommended) - GCCC (GIAC Critical Controls Certification -
$979 exam, SANS course recommended) - PCI QSA (PCI Qualified Security Assessor -
$3000 req'd course) - CISA (ISACA Certified Information Systems Auditor -
$760 exam) - GMON (GIAC Continuous Monitoring -
$979 exam, SANS course recommended) - CIS LA (IBITGQ Certified ISO 27001 Information Security Management Specialist Lead Auditor -
$2,008 course exam, Branded course required) - GCIA (GIAC Certified Intrusion Analyst -
$979 exam, SANS course recommended) - CTPRA (Shared Assessment Certified Third-Party Risk Assessor -
$1295 course) - PECB 27001LA (PECB ISO/IEC 27001 Lead Auditor -
$930 exam, Course required) - IS20 (Mile2 IS20 Controls -
$550 exam) - C)ISSA (Mile2 Certified Information Systems Security Auditor -
$550 exam) - APMG 27001A (APMG ISO/IEC 27001 Auditor -
$400 exam, Application essay) - APMG 20000A (APMG ISO/IEC 20000 Auditor -
$308 Exam, Possible Course Req) - C)ISMS-LA (Mile2 Certified Information security Management Systems Lead Auditor -
$550 exam) - CIS IA (IBITGQ Certified ISO 27001 Information Security Management Specialist Internal Auditor -
$1543 course exam, Branded course required) - TUV MSA (TUV Rheinland Mobile Security Analyst (GERMAN) -
$415 exam, Course required) - CTPRP (Shared Assessment Certified Third-Party Risk Professional -
$1295 course) - IIA CIA (The Institute of Internal Auditors Certified Internal Auditor -
$1315 3 exams)
Beginner
- DCBCLA (DRI Certified Business Continuity Lead Auditor -
$400 exam, Application req) - TUV Auditor (TUV Rheinland IT Security Auditor (GERMAN) -
$415 exam, Course required) - DCBCA (DRI Certified Business Continuity Auditor -
$400 exam, Application req) - GRCA (OCEG Governance, Risk, and Compliance Auditor -
$399 12 month license) - CISST (GAQM Certified Information systems Security Tester -
$170 exam) - EXIN CIT (EXIN Cyber & IT Security -
$225 exam) - TUV CySec (TUV Rheinland Cybersecurity Specialist (GERMAN) -
$415 exam, Course required) - TUV CyAware (TUV Rheinland Cybersecurity Awareness (GERMAN) -
$415 exam, Course required)
✨ Software Security
(The software development security domain deals with implementing software-based security protocols within environments for which the IT professional is responsible. Risk analysis, vulnerability identification and auditing of source codes are all covered in this subset. Additional topics include software-designed security, maturity models, development methodologies, open-source and third-party development security.)
Intermediate
- GWEB (GIAC Certified Web Application Defender -
$979 exam, SANS course recommended) - S-CSPL (SECO Secure Programming Certified Leader -
$460 exam) - CSSLP ((ISC)2 Certified Secure Software Lifecycle Professional -
$599 exam) - CASE (EC Council Certified Application Security Engineer (.NET or Java) -
$550 exam) - DevNet Pro (Cisco DevNet Professional -
$1200 two exams, DevNet Associate req'd) - GMLE (GIAC Machine Learning Engineer -
$979 exam)
Beginner
- CASST (GAQM Certified Advanced Software Security Tester -
$210 exam) - CCSC (CertNexus Cyber Secure Coder -
$300 exam) - DevNet A (Cisco DevNet Associate -
$300 Exam) - SOG CAP (SecOps Group Certified AppSec Practitioner -
$249 exam) - CSST (GAQM Certified Software Security Tester -
$170 exam) - C)SWAE (Mile2 Secure Web Application Engineer -
$550 exam) - MASE (Mosse Institute Certified Application Security Engineer -
$450 exam) - S-SPF (SECO Secure Programming Foundation -
$460 exam)
✨ Security Operations
(The security operations domain covers topics ranging from investigations and digital forensic to detection and intrusion prevention tools, sandboxing and firewalls. Topics include user and entity behavior analytics, threat intelligence (threat hunting and threat feeds) log management, artifacts (mobile, computer and network), machine learning and AI-based tools, penetration testing, and exploitation development.)
Expert
Forensics
- GREM (GIAC Reverse Engineering Malware -
$979exam, SANS course recommended) - CFCE (IACIS Certified Forensic ComputerExaminer -
$750 4 peer reviewed exams) - CSFA (CSIAC CyberSecurityForensic Analyst -
$750 exam & lab) - GIME (GIACiOS and MacOS Examiner -
$979 exam, SANS course recommended)
Incident Handling & Threat Intelligence
- CCD (Certified CyberDefender -
$800course, 2 exam attempt included) - CAWFE (IACIS Certified AdvancedWindows Forensic Examiner -
$750 written exam & lab) - GCFA (GIAC Certified ForensicAnalyst -
$979 exam, SANS course recommended) - GCTI (GIAC Cyber ThreatIntelligence -
$979 exam, SANS course recommended) - CFSR (OpenText Certified ForensicSecurity Responder -
$250 written exam & lab) - GNFA(GIAC Network Forensic Analyst -
$979 exam, SANS course recommended) - MTIA (Mosse Institute CertifiedThreat Intelligence Analyst Certification -
$450 certification programme,100% practical. No expiry.) - GCFR (GIAC Cloud Forensics Responder -
$979exam, SANS course recommended) - BTL2 (Security Blue Team Level 2 -
$2,190course, 1 exam attempt included)
Penetration Testing
- CREST CSAM (CRESTCertified Simulated Attack Manager -
$2,499 2 exams) - MRT (Mosse Institute Certified Red TeamerCertification -
$450 certification programme, 100% practical. No expiry.) - CREST CCTINF (CREST CertifiedInfrastructure Tester -
$2,520 exam & lab) - HTB CWEE (Hack the Box Certified WebExploitation Expert -
$1260 Subscription available)
Exploitation
- OSEE (Offensive SecurityExploitation Expert -
$5,000 lab, Plus travel) - OSCE3 (Offensive Security Certified Expert 3 -
$4649 3 labs) - OSWE (Offensive SecurityWeb Expert -
~$1649 lab) - OSEP (OffensiveSecurity Experienced Penetration Tester -
$1,499 lab) - OSED (OffensiveSecurity Exploit Developer -
$1,499 lab) - GXPN (GIAC Exploit Researcherand Advanced Penetration Tester -
$979 exam, SANS course recommended) - GAWN (GIAC Assessing WirelessNetworks -
$979 exam, SANS course recommended)
Intermediate
Forensics
- GCFE (GIAC Cerified ForensicsExaminer -
$979 exam, SANS course recommended) - GASF (GIAC Advanced Smartphone Forensics -
$979 exam, SANS course recommended) - Cisco COP (Cisco CertifiedCyberOps Professional -
$700 two exams) - CCFE(Infosec Institute Certified Computer Forensics Examiner -
$4,599 exam,Course required) - MCPE (Mosse Institute CertifiedCyber Protection Expert -
$800 exam) - CMFE(Infosec Institute Certified Mobile Forensics Examiner -
$1,699 exam,Course required) - GX-FA (GIAC Experienced Forensics Analyst -
$1299 exam, SANS course recommended) - CDRP(Infosec Institute Certified Data Recovery Professional -
$4,599 exam,Course required) - eCDFP(eLearnSecurity Certified Digital Forensics Professional -
$400 exam) - GPYC (GIAC PythonCoder -
$979 exam, SANS course recommended) - MDFIR (Mosse Institute Certified DFIRSpecialist -
$450 certification programme, 100% practical. No expiry.) - SC-400 (Microsoft Certified InformationProtection Administrator Associate -
$165 exam) - CCE (ISFCE Certified Computer Examiner-
$485 written exam) - CM)DFI (Mile2 Certified MasterDigital Forensic Investigator -
Complete C)SP, C)DFE, C)NFE and C)CSA($2200)) - EnCE(OpenText EnCase Certified Examiner -
$200 two exams) - ACE(AccessData Certified Examiner -
$100 + software)
Incident Handling & Threat Intelligence
- GEIR (GIAC Enterprise Incident Response -
$979 exam, SANS course recommended) - eCTHP(eLearnSecurity Certified Threat Hunting Professional -
$400 lab) - GCED (GIAC Certified Enterprise Defender -
$979 exam, SANS course recommended) - GCDA (GIAC Certified Detection Analyst -
$979exam, SANS course recommended) - GCIH (GIAC Certified ForensicsAnalystr -
$979 exam, SANS course recommended) - MTH (Mosse Institute Certified Threat HunterCertification -
$450 certification programme, 100% practical. No expiry.) - CREST CRIA (CREST RegisteredIntrusion Analyst -
$612 exam & lab) - CREST CRTIA (CRESTRegistered Threat Intelligence Analyst -
$615 2 exams) - CREST CCHIA (CRESTCertified Host intrustion Analyst -
$2,481 exam & essay, Hands on exam inUK) - eCIR(eLearnSecurity Certified Incident Responder -
$400 lab) - C)IHE (Mile2 Certified Incident HandlingEngineer -
$550 exam)
Penetration Testing
- PACES (Pentester Academy CertifiedEnterprise Security Specialist -
$339-749 Lab access, Exam included) - S-CEHL (SECO Certified Ethical Hacker Leader -
Application) - CREST CRT (CREST RegisteredPenetration Tester -
$612 exam) - CRTO II (ZeroPoint Security Red Team Operator II -
$121 lab) - S-EHE (SECO Ethical Hacker Expert -
TBD(still), Being redesigned) - CREST CCTIM (CRESTCertified Threat Intelligence Manager -
$2,480 3 exams) - OSCP (Offensive SecurityCertified Professional -
$1,499 labs) - GX-PT(GIAC Experienced Penetration Tester -
$1299 exam, SANS course recommended) - GPEN (GIAC CertifiedPenetration Tester -
$979 exam, SANS course recommended) - OSWP (Offensive SecurityWireless Professional -
$450 labs) - CRTO (Zero PointSecurity Certified Red Team Operator -
$121 lab) - LPT(EC Council Licensed Penetration Tester -
$899 exam) - PNPT (TCM Security Practical NetworkPenetration Tester -
$299 exam) - GCPN (GIAC Cloud PenetrationTester -
$2,499 exam, SANS course recommended) - GRTP(GIAC Red Team Professional -
$979 exam, SANS course recommended) - SOG CAPenX (The SecurityOps Group CertifiedAppSec Pentesting eXpert -
$800 exam) - CSTL (CyberScheme Team Leader -
$1945 exam) - eCPPT(eLearnSecurity Certified Professional Penetration Tester -
$400 lab) - eWPT(eLearnSecurity Web Application Penetration Tester -
$400 lab) - CM)IPS (Mile2 Certified MasterIntrusion Prevention Specialist -
Complete C)VA, C)PEH, C)PTE and C)PTC($2200)) - HTB CBBH (Hack the Box Certified Bug Bounty Hunter-
$145 modules + $210 exam, $490 Subscription available)
Exploitation
- eWPTX (eLearnSecurityWeb Application Penetration Tester eXtreme -
$400 exam, $2000 training) - CREST CCSAS (CRESTCertified Simulated Attack Specialist -
$2,520 2 exams & lab) - MCD (Mosse Institute CertifiedCode Deobfuscation Specialist Certification -
$450 certification programme,100% practical. No expiry.) - GMOB (GIAC Mobile Device Security Analyst -
$399 exam, SANS course recommended) - PJMR (Practical Junior MalwareResearcher -
$399 lab) - CREA(Infosec Institute Certified Reverse Engineering Analyst -
$4,599 exam,Course required)
Beginner
Forensics
- OSIP (IntelTechniques OpenSource Intelligence Professional -
$300 practical exam) - Cisco COA (Cisco Certified CyberOpsAssociate Cyber Operations -
~$325 exam) - C)CSA (Mile2 Certified CybersecurityAnalyst -
$550 exam) - CHFI (EC Council Computer HackingForensics Investigator -
$650 exam) - SC-200 (Microsoft Certified: Security OperationsAnalyst Associate -
~$165 exam) - MRCI (Mosse Institute RemoteCybersecurity Internship Programme -
$49 certification programme, 100%practical. No expiry.) - EDRP(EC Council Disaster Recovery Professional -
$450 exam) - HTB CDSA (Hack the Box Certified DefensiveSecurity Analyst -
$145 modules + $210 exam, $490 Subscription available) - CySA+ (CompTIACybersecurity Analyst+ -
$404 exam) - CSX-P (ISACA Cybersecurity Practitioner -
$549lab) - C)NFE (Mile2Certified Network Forensics Examiner -
$550 exam, Groups only) - GOSI(GIAC Open Source Intelligence -
$979 exam, SANS course recommended) - OPSA (ISECOM OSSTMM ProfessionalSecurity Analyst -
$100 annual sub, Unknown exam fee) - CSAE (Cyber Struggle AEGIS -
$1700 course exam, Branded course required) - ASIS PCI (ASIS Professional CertifiedInvestigator -
$485 exam) - MOIS (MOIS Certified OSINT Expert Certification-
$450 certification programme, 100% practical. No expiry.) - CFA (GAQMCertified Forensic Analyst -
$128 exam) - CSA (EC CouncilCertified SOC Analyst -
$550 exam) - GFACT (GIAC FoundationalCybersecurity Technologies -
$979 exam, SANS course recommended) - ECSS (ECCouncil Certified Security Specialist -
$249 exam) - C)DFE (Mile2 Certified Digital ForensicsExaminer -
$550 exam) - C)SP (Mile2 Certified Security Principles -
$550 exam) - CSCU (ECCouncil Certified Secure Computer User -
$125 exam) - MICS (Mosse Institute Introductions toCyber Security -
Free exam)
Incident Handling & Threat Intelligence
- S-TA (SECO Certified Threat Analyst -
$550 exam) - ECIH (EC Council Certified IncidentHandler -
$300 exam) - OSDA (OffensiveSecurity Defense Analyst -
$2,499 exam, Learning subscription required) - CFR (CertNexusCyberSec First Responder -
$250 exam) - CTIA (EC Council Certified Threatintelligence Analyst -
$450 exam) - MAD SOCA (Mitre Att&ck Defender SecurityOperations Center Assessment -
$299 annual subscription) - MAD CTI (Mitre Att&ck Defender Cyber Threatintelligence -
$299 annual subscription) - CCOA (ISACA Certified CybersecurityOperations Analyst -
$760 exam) - CREST CPIA (CRESTPractitioner Intrusion Analyst -
$425 exam) - MESE (Mosse InstituteEnterprise Security Engineer -
$450 exam) - CREST CPTIA (CRESTPractitioner Threat Intelligence Analyst -
$425 exam) - S-SA (SECO Associate SOC Analyst -
$480exam) - DV AOPH (Dark Vortex AdversaryOperations and Proactive Hunting -
$2500 exam, Course required) - CND (ECCouncil Certified Network Defender -
$550 exam) - CSX-F (IBITGQ CyberIncident Response Management Foundation -
$768 course exam, Branded courserequired) - DV MILF (Dark Vortex Malware Incident and LogFoensics -
$2000 exam) - CIRM Fdn (IBITGQ CyberIncident Response Management Foundation -
$768 course exam, Branded courserequired)
Penetration Testing
- C)PSH (Mile2 Certified Powershell Hacker -
$550 exam) - CMWAPT(Infosec Institute Certified Mobile and Web App Penetration Tester -
$4,599exam, Course required) - C)PTC (Mile2 Certified Penetration TestingConsultant -
$550 exam) - CRTOP(Infosec Institute Certified Red Team Operations Professional -
$4,599exam, Course required) - CSR (Cyber Struggle Ranger -
Location Based Cost, Course Req) - CEH (ECCouncil Certified Ethical Hacker -
$1,199 exam) - SOG CAPen (The SecOpsGroup Certified AppSec Pentester -
$500 exam) - C)PTE (Mile2Certified Penetration Testing Engineer -
$550 exam) - SOG CNPen (The SecOpsGroup Certified Network Pentester -
$500 exam) - DV RTOS (Dark Vortex Red Team & OperationalSecurity -
$2500 exam, Course required) - SOG CMPen And (The SecOps Group CertifiedMobile Pentester - Android -
$400 exam) - SOG CMPen iOS (The SecOps Group Certified MobilePentester - iOS -
$400 exam) - DV MoS (Dark Vortex Malware on Steroids -
$2000 exam, Courserequired) - Pentest+ (CompTIA Pentes+ -
$404 exam) - C)VA (Mile2 CertifiedVulnerability Assessor -
$550 exam) - KLCP (Kali Linux Certified Professional -
$299exam)
Exploitation
- eMAPT(eLearnSecurity Mobile Application Penetration Tester -
$400) - BSCP (Portswigger Burp SuiteCertified Practioner -
$99 exam) - OPST (ISECOM OSSTMM ProfessionalSecurity Tester -
Unknown) - OSWA (OffensiveSecurity Web Assessor -
$2,499 Exam, Learning subscription required) - CSTM (CyberScheme Team Member -
$610 exam) - eJPT (eLearnSecurity JuniorPenetration Tester -
$249 lab) - S-EHP (SECO Ethical Hacking Practitioner -
$550 exam) - CHAT (ISECOM Certified Hacker AnalystTrainer -
$100 annual sub, Unknown exam price) - CREST CPSA (CRESTPractitioner Security Analyst -
$425 exam) - OPSE (ISECOM OSSTMM ProfessionalSecurity Expert -
$100 annual sub, Unknown exam cost) - MPT (Mosse Institute CertifiedPenetration Tester Certification -
$450 certification programme, 100%practical. No expiry.) - CPENT (EC Council CertifiedPenetration Testing Professional -
$999 exam) - CREST CCTAPP (CRESTCertified Web Application Tester -
$2,520 exam & lab) - HTB CPTS (Hack the Box CertifiedPenetration Testing Specialist -
$200 modules + $210 exam, $490Subscription available) - MRE (Mosse Institute Certified ReverseEngineer Certification -
$450 certification programme, 100% practical. Noexpiry.) - ECES (EC Council CertifiedEncryption Specialist -
$249 exam) - MCPT (Mosse Institute Cloud PenetrationTester -
$450 exam) - C)PEH (Mile2 CertifiedProfessional Ethical Hacker -
$550 exam) - GCPEH (GAQMCertified Professional Ethical Hacker -
$170 exam) - EEHF (EXIN Ethical Hacking Foundation -
$232 exam) - S-EHF (SECOEthical Hacking Foundation -
$460 exam) - CHA (ISECOM Certified Hacker Analyst-
$100 annual sub, Unknown exam cost) - DV OTD(Dark Vortex Offensive Tool Development -
$2000 exam, Course required) - MVRE (Mosse Institute Vulnerability Researcher and Exploitation Specialist -
$450 Exam)
Best SIEM Tools in 2025: Commercial and Open Source
In 2025, organizations have a variety of SIEM solutions to choose from. As an aspiring SOC analyst, you don’t need to master all of them, but it helps to be aware of the major players and perhaps get hands-on with one commercial and one open-source tool. Below we compare some popular SIEM tools in both categories:
Popular Commercial SIEM Tools
Commercial SIEMs are enterprise-grade solutions usually backed by vendors with support and advanced features. Here are some of the top commercial SIEM platforms:
| SIEM Tool | Vendor | Key Features & Notes |
|---|---|---|
| Splunk Enterprise Security | Splunk (USA) | Market-leading SIEM known for its powerful search language and scalability. Offers extensive add-ons (UEBA, SOAR), strong community support, and a user-friendly interface. Cons: Licensing can be very expensive as data volumes grow. |
| IBM QRadar | IBM (USA) | Robust threat detection with built-in correlation rules and offense management. Excels in enterprise environments with lots of network data. Integrates well with other IBM security tools. Cons: UI can be less intuitive; requires tuning for best results. |
| Microsoft Azure Sentinel (Microsoft Sentinel) | Microsoft (USA) | Cloud-native SIEM (running in Azure) that uses KQL (Kusto Query Language) for querying logs. Tight integration with Microsoft 365 and Defender suite. Pros: Easy to start (pay-as-you-go model), great for cloud and hybrid environments. |
| ArcSight ESM | OpenText (formerly Micro Focus) | A long-standing SIEM used in many large enterprises and governments. Strong real-time correlation capabilities and compliance reporting. Cons: Perceived as complex to manage; has lost some market share to newer solutions. |
| RSA NetWitness | RSA (USA) | SIEM + network traffic analysis. Known for deep packet inspection abilities alongside log management. Provides rich context for incidents. Cons: Complex and resource-intensive to deploy and maintain. |
(Other notable mentions include Securonix (a SaaS SIEM with strong UEBA), LogRhythm, Sumo Logic, and more. The ones above are among the most commonly encountered in SOC roles.)
Popular Open-Source SIEM Tools
Open-source SIEM solutions can be used to build a home lab and are also employed by some organizations (often smaller companies or those with tight budgets). They might require more manual setup but are excellent for learning. Top open-source options include:
| SIEM Tool | Overview & Features | Pros & Cons |
|---|---|---|
| Elastic Stack (ELK) + SIEM | The Elastic Stack (Elasticsearch, Logstash, Kibana) can serve as a SIEM when you ingest logs and use Elastic Security features. Offers powerful search and visualization via Kibana, and you can add detection rules for correlations. | Pros: Highly flexible, free basic license, huge community. Cons: Needs setup and tuning; advanced security features (like machine learning anomaly detection) require a paid license (X-Pack). |
| Wazuh | An open-source fork of OSSEC, now a full platform that combines SIEM and endpoint detection. Wazuh has an agent for collecting host data (file integrity, malware detection, etc.) and a built-in Kibana-based interface for analysis. | Pros: Free and feature-rich (comes with many built-in rules, e.g. for AWS logs, Office 365). Cons: Setup can be complex; documentation isn’t as extensive as major commercial tools. |
| Graylog | A log management platform that can be used for SIEM use-cases. It provides a web interface for searching logs and creating alerts (via pipeline rules or content packs). | Pros: Easier to deploy than a full ELK stack; focused on log search with a simple UI. Cons: Alerting and correlation are basic compared to others; might need plugins or custom scripts for advanced detection. |
| Security Onion | Not a single tool but a Linux distro that packages several security monitoring tools (Elastic, Zeek, OSQuery, etc.) into an out-of-the-box platform. Often used for blue team labs and network monitoring. | Pros: Quick way to stand up a full-featured monitoring environment; great for learning (network IDS + SIEM in one). Cons: Heavy resource needs; can be overkill if you just want a simple SIEM for log collection. |
| AlienVault OSSIM | The open-source predecessor to AT&T’s AlienVault USM. It integrates asset discovery, IDS (Snort), SIEM correlation, and more in one package. (Note: it hasn’t been updated recently, but still used in lab scenarios.) | Pros: All-in-one solution with many security tools pre-integrated. Cons: Outdated in some aspects; interface is not very modern, and community support has waned as focus shifted to the commercial version. |
When learning, you might try setting up an ELK or Wazuh lab, since they are widely used and have active communities. Graylog is also a good starting point if you want something lighter. The key is to understand core SIEM concepts – those will transfer even if you work on a different tool at your job.

Hands-On Experience: Building a SOC Home Lab and Portfolio
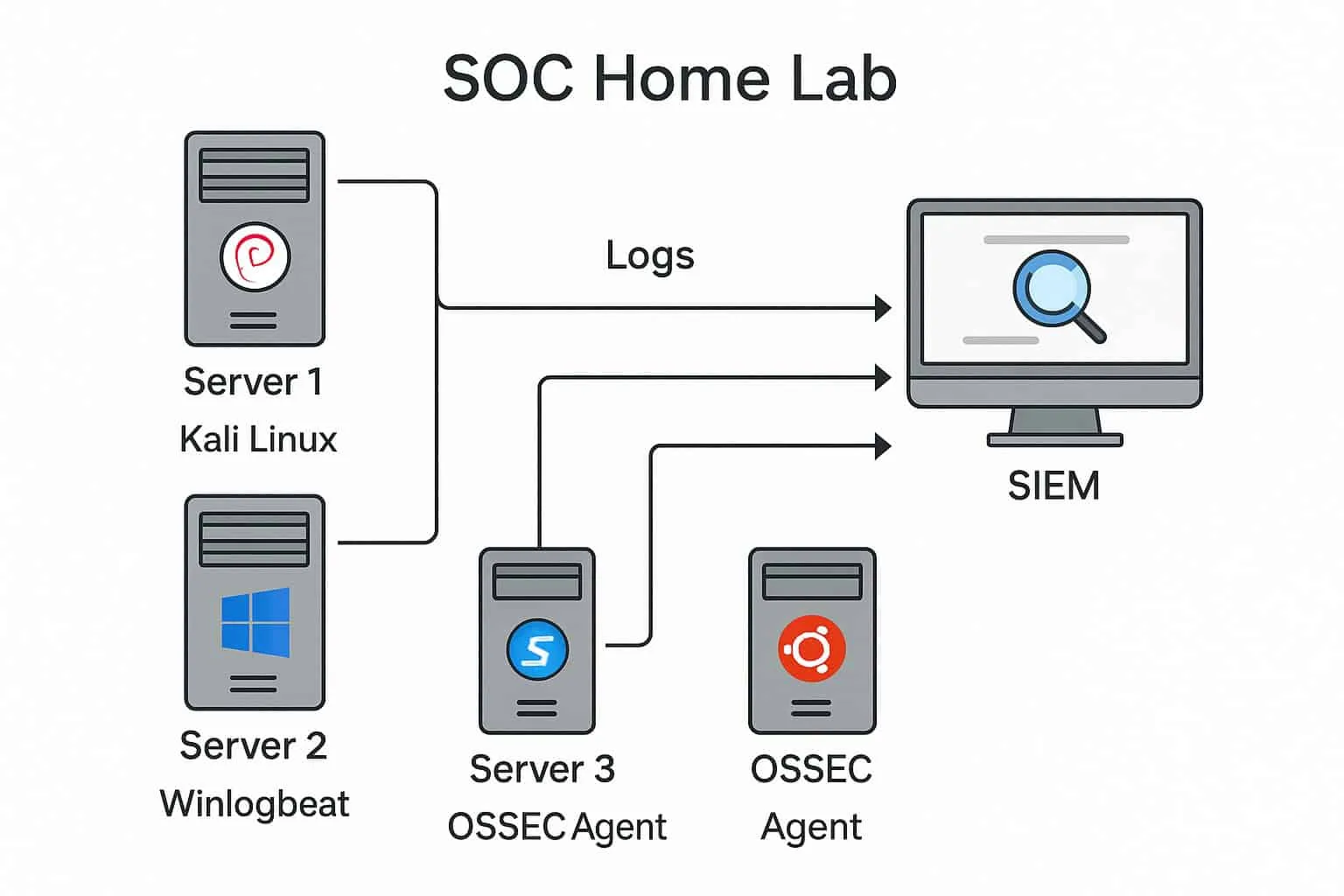
One of the best ways to prepare for a SOC career is to get hands-on practice. Setting up a home lab will allow you to simulate attacks and learn to detect and investigate them – experience that you can showcase in your portfolio and interviews. Here’s how to go about it:
- Set Up a Home Lab Environment: You don’t need fancy hardware – a decent PC or laptop with 8-16 GB RAM can host a few virtual machines. Use VirtualBox or VMware to create a small network: for example, one VM can be a Windows 10 machine (to generate user logs), another a Linux server, and a third running a SIEM platform. You can also use cloud free tiers (AWS, Azure) if your hardware is limited. Many SIEMs have free versions or trials – Splunk offers a free version (up to 500 MB/day of data), and cloud SIEMs like Azure Sentinel have free data allowances. For instance, you could try the Elastic Stack or Wazuh for an open-source solution, or a Splunk 14-day cloud trial to get familiar with a commercial tool.
Need a Linux workstation setup guide? See Debian Lab Setup for Cyber-Security Enthusiast.
-
Generate and Collect Logs: A SIEM is useless without data. Configure your lab machines to produce logs and send them to your SIEM:
- Install Sysmon on Windows to generate detailed security logs (process creation, network connections, etc.).
- Enable logging for authentication events, PowerShell activities, etc. on your Windows VM.
- On Linux, enable syslog for auth logs, and maybe set up a simple web server to generate access logs.
- Use your SIEM’s agents or log forwarders to send these logs. (For example, set up the Splunk Universal Forwarder on each VM, or configure Filebeat/Logstash for Elastic).
-
Simulate Attacks and Incidents: Now, create some “incidents” to detect:
- Use harmless tools like Atomic Red Team or Caldera to simulate attacks (e.g., brute-force login attempts, Mimikatz running for credential dumping, etc.). This will produce log patterns you can catch.
- Manually craft scenarios: e.g., enter wrong passwords multiple times to trigger a Windows failed login event, or run a port scan with Nmap against your Linux server.
- If you have two VMs, you can attempt a simple “malware” execution on one (even a test virus file like the EICAR test file) and see if your anti-virus logs catch it.
-
Practice Using the SIEM: Try to detect the malicious activities using your SIEM:
- Search the logs for keywords or use filters (for example, find all events with “Failed login” or the specific Sysmon Event ID for new process execution).
- Create a detection rule: Most SIEMs allow custom correlation rules or alerts. Write a rule for something like “Alert if more than 5 failed logins on the Windows VM occur within 1 minute” or “Alert if a PowerShell process spawns
whoami.exe” (indicative of certain attacks). - Test your rule by causing the event and see if the SIEM generates an alert.
-
Document Your Findings: Each lab exercise you do can become a mini case study. Take notes and screenshots – for example, screenshot the SIEM dashboard showing an alert you caught, export log events that were interesting, and then write up a brief incident report of what you did and found.
-
Build Portfolio Projects: Use the above artifacts to create portfolio items:
- Threat Hunting Dashboard: For instance, build a dashboard in Kibana or Splunk that visualizes failed login counts, new processes, etc., to demonstrate how you monitor activity.
- Detection Rule Repository: If you write any custom SIEM queries or Sigma rules (a generic format for detections), upload them to a GitHub repository. This shows employers you can create detection logic.
- Incident Report or Blog Post: Write a short report or a blog article about one of your lab investigations (e.g., “Investigating a Brute Force Attack in My Home SOC Lab”). This highlights your analytical approach and communication skills.
- Playbooks: Develop a simple Incident Response playbook for a scenario (for example, “Steps to take when a malware infection is detected”). You can use a Markdown template or diagram and include that in your portfolio to show you understand response procedures.
By creating a home lab and publishing your work on GitHub or a personal blog, you give employers concrete proof of your abilities. It shows initiative and passion – qualities that can set you apart from other entry-level candidates who only have coursework.
Also, engage in practical blue team challenges and CTFs. Platforms like Blue Team Labs Online, TryHackMe, and Cyber Defenders offer SOC-oriented exercises and labs. For example, TryHackMe has rooms for Splunk and threat hunting, and Blue Team Labs Online provides realistic SIEM investigations. These can further sharpen your skills and be mentioned on your CV.
Want an easy DNS-level blocker for your home network lab? Our guide to Building a Pi-hole for Enhanced Network Security walks you through it.
Landing the Job: Crafting Your Cybersecurity CV and LinkedIn Presence
When you’re ready to apply for SOC analyst positions, having a polished cybersecurity-focused resume and LinkedIn profile is crucial. Here are some tips to make them stand out:
Resume Tips:
- Highlight Relevant Skills First: List your cybersecurity skills (SIEM tools, networking, incident response, Python, etc.) prominently. Many recruiters scan for keywords like “SIEM”, “SOC”, “Splunk”, “incident response” – so ensure these appear if you have the knowledge.
- Emphasize Hands-On Projects: Since you may be a learner or fresh graduate, showcase your home lab projects, competitions, or any internships. For example, you could include a bullet: “Built a home SOC lab with Splunk to analyze simulated attacks and created detection rules for brute-force logins.” This shows practical ability even if you haven’t worked in a SOC yet.
- Certifications and Training: Put a section for certifications (Security+, etc.) or relevant courses completed. This can be towards the top if you lack work experience.
- Tailor for ATS: Many companies in Singapore/Malaysia use Applicant Tracking Systems. Use a simple format (no fancy graphics that might confuse parsing) and include relevant keywords from the job description. For example, if a job posting mentions “monitoring SIEM alerts” or specific tools like “QRadar,” make sure those phrases (if you have that skill) appear in your resume.
- Concise and Clear: Keep it to 1-2 pages. Be specific about your contributions in any project or role. Use action verbs and quantify when possible (e.g., “Analyzed 5,000+ daily log events using Graylog in lab environment”, “Detected and responded to 3 simulated incidents during a cyber drill”).
LinkedIn Profile Tips:
- Professional Headline: Use the headline to show you’re a cybersecurity professional or aspiring SOC analyst. For example: “Aspiring SOC Analyst | Security+ Certified | Home Lab Enthusiast”. This line is visible in search results and can attract recruiters.
- Detailed About Section: Write a short bio that tells your story – your skills, what you’re learning, and your career goal. You can mention your lab work or certifications here to add credibility.
- Experience and Projects: Even if you haven’t held a formal cybersecurity job, you can add an “Experience” entry for significant projects or volunteer work. For example, list your role as “Cybersecurity Home Lab Project (Self-driven)” and describe what you accomplished, or mention being part of a university cyber club or Capture-the-Flag team.
- Skills & Endorsements: Add relevant skills (e.g., Network Security, SIEM, Splunk, Incident Response, Threat Analysis). Connect with peers or mentors who can endorse some of those skills. It’s not critical, but a nice-to-have.
- Connect and Engage: Start connecting with cybersecurity professionals, join LinkedIn groups (there are Asia-Pacific cybersecurity groups, for instance), and follow companies that have SOC teams or provide SOC services. Engage with content – comment on or share interesting security news or write your own brief posts about things you learn. Being active can get you noticed and also helps you stay informed about industry trends.
Platforms for Content: Consider writing and sharing content on platforms like Medium, your own personal blog, or LinkedIn Articles. For example, if you document a cool detection technique or a cybersecurity project, turn it into a Medium post. Recruiters and hiring managers often value candidates who contribute to the community. If writing publicly seems daunting, start small – maybe a post like “5 Lessons I Learned Building My Own SOC Lab”. Consistently creating content will bolster your personal brand and SEO (so when someone Googles you, these projects show up).
Exploring Freelance and SOC-as-a-Service Opportunities
While many pursue a traditional in-house SOC role, there are alternative paths in the SOC career – like working for Managed Security Service Providers (MSSPs) or even freelancing as a security analyst. In Southeast Asia, outsourcing is common, and a lot of companies rely on SOC-as-a-Service (SOCaaS) vendors to handle their security monitoring. This means MSSPs and specialist firms need lots of analysts, often providing a gateway for newcomers to get experience.
Interested in offensive work instead? You might explore our regional guide Launching a Penetration Testing Career in Malaysia & Singapore.
MSSP Roles: If you join an MSSP, you’ll do the same work (monitoring, incident response) but for multiple client organizations. The benefit is you might see a wider variety of incidents across different industries, which can accelerate learning. Companies like global consultancies (Deloitte, EY, etc.), security firms, or telecom providers often have SOC services. In Malaysia and Singapore, there are local MSSPs where fresh graduates can get SOC analyst jobs – sometimes these roles are shift-based (including night shifts to cover 24/7 monitoring). It’s a great way to enter the field, just be prepared for the demands of multi-client environments.
Freelancing as a SOC Analyst: You might wonder, can a SOC analyst work freelance or remotely? The answer is increasingly yes. Platforms like Upwork regularly list jobs for security monitoring or incident response on a contract basis. Small businesses that can’t afford a full SOC team sometimes hire freelancers to set up SIEM monitoring or handle on-call incident response. To go this route, you’ll typically need some experience and a strong reputation:
- Platforms to check: Upwork, Freelancer.com, Fiverr (for smaller gigs), and LinkedIn (clients sometimes post or search for freelance security analysts).
- Build trust: On freelance profiles, highlight any certifications and clearly list the specific services you offer (e.g., “SIEM setup and monitoring”, “Incident investigation and report writing”, “Security log analysis”).
- Consider time zones: Being in Southeast Asia can be an advantage for remote work, as you can cover off-hours for companies in other regions. You might land a part-time remote SOC role where you monitor alerts during your daytime (which is another region’s night).
- SOCaaS for SMBs: Some enterprising professionals offer SOCaaS to small businesses by themselves or as a small team. Essentially, acting as an on-demand SOC. This could involve deploying a cloud SIEM for the client and then providing regular monitoring and reports. If you eventually build enough skill and trust, this could become a freelance business avenue (though it requires significant responsibility and reliability).
Important: When starting out, freelancing in SOC can be challenging since companies entrust you with sensitive data. It’s often easier to begin in a company or MSSP to gain experience, then later leverage that for remote or freelance opportunities. Nonetheless, it’s good to know these pathways exist. As the cybersecurity talent shortage continues, more organizations are open to flexible arrangements. In fact, with an estimated 4.8 million cybersecurity professionals needed worldwide as of 2024 (and many unfilled SOC roles), there’s room to carve a non-traditional career if you are proactive and skilled.

Where to Find Jobs: Leverage the popular job portals and networks:
✨ 🇸🇬 Click to check Top 20 Websites to Find IT Jobs in Singapore
| # | Website | Focus / Notes |
|---|---|---|
| 1 | MyCareersFuture | Official government portal; trusted source for local IT jobs |
| 2 | JobStreet SG | Popular across SEA; strong in tech, finance, and corporate hiring |
| 3 | LinkedIn Jobs | Top choice for IT professionals and remote-friendly opportunities |
| 4 | eFinancialCareers SG | Great for fintech, cyber risk, and IT roles in banking sector |
| 5 | Tech in Asia Jobs | Focused on startups, regional tech jobs, and remote options |
| 6 | NodeFlair | Singapore-based tech career platform with salary transparency |
| 7 | STJobs | Backed by The Straits Times, mostly local listings |
| 8 | JobTech | AI-driven platform that curates real-time job market data |
| 9 | Glints SG | Fast-growing platform for tech & creative roles, great for startups |
| 10 | JobsCentral SG | Covers both IT and non-IT sectors; good for fresh grads |
| 11 | StartupJobs Asia | Startup-centric, often includes equity-based and flexible roles |
| 12 | HackerTrail | Tech-specific hiring platform, includes coding challenges |
| 13 | Wantedly SG | Company culture-focused job search for startups and tech firms |
| 14 | Monster SG | International platform, useful for IT and expat positions |
| 15 | GrabJobs | Features chatbot-based application process, includes tech support roles |
| 16 | Xcruit | New-age job platform with integrated video resumes |
| 17 | InternSG | Best for internships, junior roles in IT, marketing, and engineering |
| 18 | TalentTribe | Visual job descriptions, focuses on tech and youth jobs |
| 19 | JobsDB SG | Still active, though many jobs are mirrored with JobStreet |
| 20 | DrJobs SG | Popular in the expat and overseas Singaporean community |
✨ 🇲🇾 Click to check Top 20 Websites to Find IT Jobs in Malaysia
| # | Website | Focus / Notes |
|---|---|---|
| 1 | JobStreet | Most popular job portal in Malaysia, strong IT category |
| 2 | Great for IT & cybersecurity, allows direct networking with employers | |
| 3 | JobsCentral | IT, engineering, and graduate jobs |
| 4 | Hiredly (WOBB) | Young, startup-friendly; includes internships & entry-level IT roles |
| 5 | myFutureJobs | Government portal, good for local IT and GLC jobs |
| 6 | Tech in Asia Jobs | Startup-focused, regional, many remote tech jobs |
| 7 | Glints | IT jobs in startups & SMEs, also has freelance and contract listings |
| 8 | FastJobs | Simple UI; has tech support, IT admin, and basic dev jobs |
| 9 | Jobstore | Broad platform, decent number of tech job listings |
| 10 | Indeed Malaysia | Global portal, wide range of local and expat-friendly IT roles |
| 11 | Job Majestic | Specializes in high-paying or niche roles, strong tech presence |
| 12 | FutureLab | Mentorship platform with growing job board for students and juniors |
| 13 | Monster Malaysia | Older platform but still lists IT jobs across Asia |
| 14 | Bossjob | AI-based matching, supports messaging employers directly |
| 15 | JobCart | Malaysian job portal gaining traction in tech & digital job markets |
| 16 | Jobify | Emerging site, startup jobs, internships, tech openings |
| 17 | Ricebowl | Bilingual portal (English/Chinese), includes tech jobs |
| 18 | TribeHired | For tech and startup talent, includes high-level developer roles |
| 19 | Maukerja | Blue-collar + tech support/IT admin roles |
| 20 | InternSheeps | Internships in IT, cybersecurity, and digital marketing |
✨ 🌐 Click to check Top 10 Fresh Remote IT Job Sites
| # | Website | Focus / Highlights |
|---|---|---|
| 1 | We Work Remotely | One of the oldest & largest platforms for remote software & DevOps jobs |
| 2 | Remote OK | Remote tech jobs with global employers; filter by timezone |
| 3 | Turing | U.S. companies hiring vetted remote developers from Asia |
| 4 | Remotive | Curated list of remote dev, cloud, and cyber jobs globally |
| 5 | Jobspresso | Remote-only jobs in tech, sysadmin, cybersecurity, product, and support |
| 6 | Working Nomads | Daily updated list of remote tech roles from global sources |
| 7 | Outsourcely | Remote jobs from startups looking to hire directly — no commission cuts |
| 8 | Pangian | Remote jobs with timezone matching; strong in tech, cyber, data |
| 9 | Hubstaff Talent | Free remote job marketplace for freelancers and long-term IT contracts |
| 10 | CodementorX | High-paying freelance/remote developer jobs, especially for experienced devs |
Salary Expectations and Job Market in Southeast Asia
One big question on jobseekers’ minds: How much can I earn as a SOC analyst? Salaries vary by country and level of experience, but here’s a general overview focusing on Malaysia and Singapore (two key markets in SE Asia):
-
Malaysia: According to recent data, a SOC analyst in Malaysia earns around RM 57,600 per year on average (approximately USD $12–13k). Entry-level positions might start lower (perhaps RM 36k–48k for fresh graduates), while those with a few years’ experience or senior roles can command higher (RM 70k+). It’s also reported that Malaysia currently has about 15,000 cybersecurity professionals but needs 27,000 to meet the current demand – a gap of 12,000 talent. This shortage is pushing salaries up and companies are eager to hire and train junior analysts to fill the gap. On top of base pay, some organizations offer shift allowances for SOC analysts (since many work in 24/7 rotations).
-
Singapore: In Singapore, the pay is higher (reflecting the higher cost of living). The average SOC analyst salary is about SGD $64,500 per year (roughly USD $47k). Junior analysts might see offers in the range of SGD $40k–50k, and those with experience can go above SGD $70k. Singapore is a regional cybersecurity hub with many international companies and banks – meaning lots of SOC roles and competitive salaries. However, competition can be stiff, so certifications and hands-on experience are valued.
-
Regional and Global: Other Southeast Asian countries like Indonesia, Vietnam, or Thailand have emerging SOC job markets too, but salaries there might be lower than Malaysia’s. On the flip side, some SOC analysts in the region choose to work remotely for U.S. or European companies, which can pay in USD or Euros (often much higher). With remote work becoming more common, a skilled analyst in, say, Kuala Lumpur or Jakarta might land a role with a foreign company and significantly boost their earning potential – truly a remote SOC job scenario.
Apart from salary, consider the career trajectory: SOC roles often lead to higher positions like SOC Manager, Incident Response Lead, or specialized roles (Threat Hunter, Malware Analyst) which command even better salaries. And globally, cybersecurity unemployment is essentially zero – there’s far more demand than supply. This is good news for newcomers: once you get that first year or two of experience, you become even more valuable.
In terms of job demand in the region, both governments and private sectors are investing heavily in cybersecurity:
- Malaysia has been ramping up its cyber defense initiatives. Local banks, telecoms, and energy companies all maintain SOCs (either in-house or via MSSP), and the government’s agency CyberSecurity Malaysia supports talent development programs. Notably, Malaysia needed to double its cyber workforce as of 2025 to meet demand, indicating plenty of opportunities for new analysts.
- Singapore’s Cyber Security Agency (CSA) and the presence of many multinational companies mean lots of openings and initiatives to grow talent. There are even programs to convert IT professionals into cybersecurity roles. The financial sector in Singapore especially drives demand for SOC analysts to protect banking infrastructure.
Both countries (and others in SE Asia) face a shortage of skilled analysts – as noted earlier, many organizations report difficulty finding qualified people. For you, this means that with the right skills and determination, you likely won’t struggle to find opportunities.
Keep an eye on local job portals and sites like LinkedIn Jobs, JobStreet (for Malaysia), and MyCareersFuture (for Singapore). The titles to search for include “SOC Analyst”, “Security Operations Center”, “Cybersecurity Analyst”, “Security Monitoring”, etc. Sometimes entry-level roles are listed as “Information Security Executive” or “IT Security Analyst” – read the description to see if it’s SOC-related (monitoring, incident response duties). If you can, attend local cybersecurity meetups or job fairs (many are virtual now) to network with industry professionals.
Six-Month Roadmap to Become a SOC Analyst
By now, we’ve covered the knowledge and tools you need. To wrap up, let’s outline a 6-month roadmap that an aspiring SOC analyst can follow to build skills methodically. This plan assumes you might be starting from basic IT knowledge:
| Month | Focus Area | Goals and Milestones |
|---|---|---|
| Month 1 | Foundations (Networking & Linux) | - Learn networking basics (TCP/IP, common ports, protocols). - Get comfortable with Linux command line and Windows administration fundamentals. - Complete an online course or study CompTIA Network+ materials for networking. |
| Month 2 | Security Basics (Cybersecurity Fundamentals) | - Study security fundamentals: types of attacks (malware, phishing, etc.), security concepts (CIA triad, encryption, firewalls). - Take an introductory course like CompTIA Security+ or equivalent. - Practice on platforms like TryHackMe (beginner-friendly security labs) to apply concepts hands-on. |
| Month 3 | SIEM and Monitoring | - Pick a SIEM tool to focus on (Splunk, Elastic/Wazuh, or Azure Sentinel) and set it up in a lab. - Learn to ingest logs and create simple searches/alerts in your SIEM. - Follow a guided project or tutorials for that SIEM (Splunk has free workshops; Elastic has documentation with examples). |
| Month 4 | Hands-On Blue Teaming (Lab & Detection) | - Expand your home lab: simulate attack scenarios (use tools like Atomic Red Team) and practice detecting them in your SIEM. - Join a blue team exercise: e.g., complete a Blue Team Labs Online challenge or a TryHackMe room focused on SOC/SIEM. - Document one lab investigation as a report or blog post (to use in your portfolio). |
| Month 5 | Advanced Skills (Incidents & Scripting) | - Learn incident response in depth: read about IR steps, maybe take a course (e.g., SANS SEC504 or an incident handling course). - Practice basic malware analysis in a safe environment (use online sandboxes or static analysis for malware samples) to understand the artifacts attacks leave behind. - Improve your scripting: write a Python script to parse a log file or automate a repetitive task in your lab. - If ready, attempt a certification exam (Security+, CySA+, or Azure SC-200, etc.) this month. |
| Month 6 | Career Prep (Job Hunting Skills) | - Finalize your resume with the projects, skills, and any certs you obtained. - Update your LinkedIn with a detailed profile as discussed earlier (add your lab projects in the experience section). - Start applying to SOC analyst jobs or internships; also reach out to connections or mentors for referrals. - Continue learning: pick up knowledge on any weak areas you discover during interviews (e.g., if you get cloud security questions, do a quick AWS/Azure security overview). |
This 6-month roadmap is intensive, but even if you stretch it to 9 or 12 months, the sequence of learning remains valid. The key is consistent progress – building your knowledge step by step and demonstrating that knowledge through projects or certifications. By the end of six months, you could have a solid foundation, a home lab with real-world simulations, a cert or two, and a strong resume ready to go.
Conclusion: Your SOC Career Awaits in 2025
Building a SOC and SIEM career is challenging but immensely rewarding. You’ll be entering a field where demand is high, the work is exciting (there’s never a dull day when cyber threats are evolving constantly!), and you have the chance to make a real impact by protecting organizations from harm.
By following this guide – learning the fundamentals, getting hands-on with SIEM tools, creating a lab and portfolio, and making connections – you are well on your way to becoming a SOC analyst. Remember to stay curious and keep learning; the best analysts are those who adapt with the changing threat landscape.
2025 is an excellent time to start this journey. Companies in Malaysia, Singapore, and around the world are actively looking for fresh talent to join their security teams. Whether you aim to work in a high-tech Security Operations Center, or prefer the flexibility of remote/freelance work, the opportunities are out there for you.
Next Steps: Take the first action now – set up that lab, enroll in that course, or reach out to a mentor. And when you do land your SOC role, don’t stop learning! This field offers many pathways (incident responder, threat hunter, SOC manager, etc.) as you gain experience.
If you found this guide useful, be sure to explore other articles on our blog for more cybersecurity career tips. Feel free to contact us for mentorship opportunities or if your business needs freelance SOC/SIEM consulting services. We’re here to help you succeed in your cybersecurity journey.

